Nowadays, the digital era seems to be beneficial for companies of all dimensions but cyber threats strive forward. Australian Cyber Security Centre (ACSC) has been instrumental in being proactive in giving a solution-driven approach to thwart this menace.
Here we are mainly focusing on the topic “All About ACSC Essential 8 Cybersecurity Model“.
The list they came up with, the ACSC Essential Eight, is not a complete solution but a resilient, eight strategies that can be done in priority order. Herein are those strategies in which we will take a deep dive into what they mean and how they can significantly bolster the cybersecurity posture of your organization.
The ACSC website is a great place to check for materials that can be used for implementing the Essential Eight and raising your cyber security level.
They give you tactical guidance via steps to be followed and models of maturity to get a view of where you stand. Through proper implementation and ceaseless development of a cybersecurity stance, the likelihood of you experiencing a cyberattack will be greatly reduced.
In this Blog, we have Covered The Following Topics
What is the ACSC Essential 8 Cybersecurity Model?
The ACSC Essential Eight is, in many ways, an acceptable model but a better-suited description for it is a framework. It’s a useful tool devised by the Australian Cyber Security Centre (ACSC), which will aid in reducing the risk of malicious cyberattacks.
Here’s the key distinction:
- Model: Models are normally applied to systems or concepts in a way that is a simplification of them. It is a means to understand certain things but it is not a solution for the actual problem in terms of actions to be taken.
- Framework: A framework is the foundation or the guiding principle for the process of getting an issue or an undertaking done. In the guide, it will list the most important aspects of the approach and also give the general principles, that will make it be more actionable than the model.
The ACSC Essential Eight is a framework because it provides organizations with a practical way to implement as a mitigation strategy their cybersecurity risks, which can significantly diminish their cybersecurity risks.
Why is ACSC Essential 8 Compliance is Important?
ACSC Essential Eight compliance is important for several reasons:
1. Strengthens Your Defenses
The strategies eight are focused towards the core cybersecurity functions that are application resistance to the majority of the attacks. These go a long way towards that and all their attempts become unsuccessful trying to get access to your systems.
2. Reduces the Risk of Cyberattacks
Finally, if you take into account these good practices, you will passively lower the level of common cyber vulnerabilities existing in the systems. Through this mindset, the chances of your business getting attacked by cybercriminals can be reduced.
3. Minimizes Damage
The worst scenario can still be managed successfully with the Essential Eight principles by virtue of the fact the impact would be minimized. Using backups and reducing the probability of wrongdoings could aid in identifying the hack and its source. The speed of recovery could be increased.
4. Boosts Business Resilience
With the growing cyber risks, securing a business against attacks is critical for you to succeed in the market. Through the manifestation of adherence to the major 8, you will prove your devotion to the data protection thus, increasing the trust of the customers and may encourage more partnerships with investors.
5. Mandatory for Some
In Australia, Essential Eight compliance is mandatory for every NCCE. NCCEs can be government organizations or Commonwealth entities not related to a corporation. Apart from some companies, it is not a legal requirement, but it still usually has the status of a recommended measure of Maturity for cyber hygiene.
6. Foundation for Advanced Security
The Essential Eight is a good foundation for building up security in cyberspace. When you have your critical security strategies set, you can then add further bolstering devices to make sure that your defenses are solid, and that potential security breaches are avoided.
List of Essential 8 Cyber Security Checklist
1. Application Control
Therefore, this incident isolates the software so only authorized applications can perform and all the malware is not allowed to run on your systems.
2. Patch Application Vulnerabilities
Similarly, just as silicon a roof repair prevents a house from leaking, so let’s software vulnerabilities do the same and close the entry points deployed by hackers.
3. Run Microsoft Office Macro Settings.
Malicious macros can be injected into documents, and their usefulness is in part why they have been disabled by default, therefore reducing the exploitation risk.
4. User Application Hardening
Therefore, setting IP access control, strong passwords, and necessary authorization is necessary to prevent possible exposure.
5. Restrict Administrative Privileges
Achieving this goal minimizes accessibility to privileged accounts. Hence, hackers find it difficult to do damage once those accounts are compromised.
6. Patch Operating System Vulnerabilities
However, updating operating systems on a regular basis with “known vulnerabilities” security patches is highly essential.
7. Multi-factor Authentication
Moreover, an extra layer of security given that just a password is not sufficient becomes really a tight security to unauthorized users entering.
8. Daily Backups
By practicing regular backups you will be able to provide yourself with the safety net if something like a cyberattack happens. Even though you will spend a little time on the recovery, it is whole times better than losing your data.
Essential Eight Assessment Process
Essential Eight of the ACSC also isn’t grounded on typical risk assessment wherein the central process should be strict and constant. Instead of that method, the approach takes the essential eight maturity model which is a concept.
This framework serves organizations as a reference to take snapshots of their progress for each strategy and check it against the path of growth which is defined by the increasing levels of sophistication.
Here’s a breakdown of the key aspects of the assessment process
1. Maturity Levels:
- Maturity Level Zero (ML0): Actually, this says more about the organization because this implies that they don’t have any goal for even Maturity Level One.
- Maturity Level One (ML1): Here is the foundation framework. This society has been built with a set of precautionary measures and each benchmark, as such, has been addressed as far as they are concerned.
- Maturity Level Two (ML2): In the other age group, a more mature product can be expected. The controls are documented, reviewed, and kept up-to-date, till the process is done.
- Maturity Level Three (ML3): This is the best level, as you have already taken adequate care to assure security. Modifications are permanently sought and the plans are subject to control systems.
2. Assessment Steps
- Determine Assessment Scope: What will come next is to affix the target classroom level, which has to be agreed not only by stakeholders but also by responsible persons. Do not forget that the eight principles that correspond to the pharmaceutical approach should be treated as a holistic package.
- Gather Information: This necessitates putting an evidence trail together to prove how the company acts at a given maturity level by applying the respective strategy. It can comprise of these policies, such as algorithms, parameters, structure settings, and risk results.
- Evaluate Implementation: The score determined whether the controls met the maturity conditions specified for each of the controls selected.
- Document Findings: A full report, that covers post-assessment results as well as the areas of need and possible enhancements – is created right away.
ACSC Strategies to Mitigate Cyber Incidents
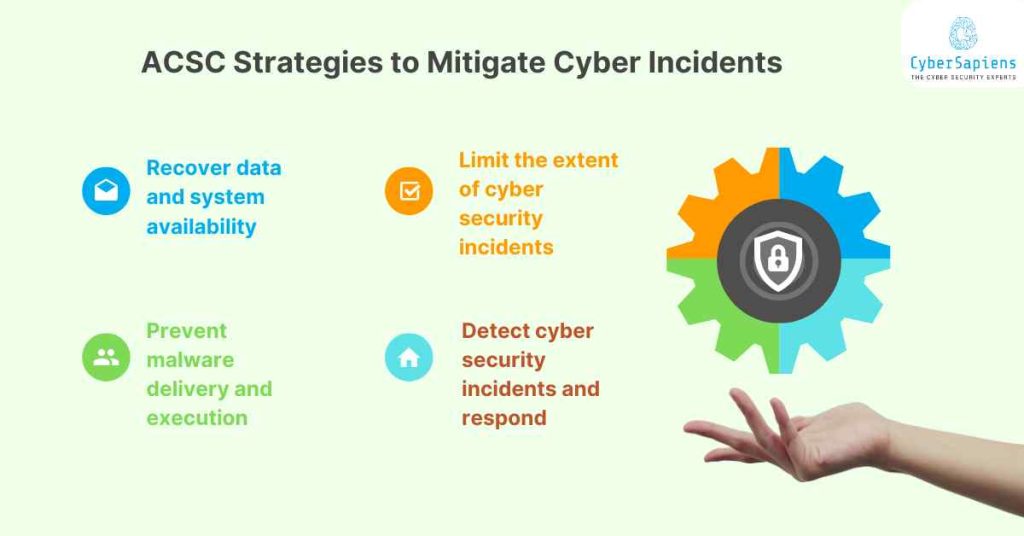
Besides just emphasising the eight essential cybersecurity mitigation measures, the ACSC additionally focuses on efficient event management as well as incident responses to effectively deal with cyber incidents.
Similarly, the Essential Eight stands as a fundamental set of processes; the Strategies to Mitigate Cyber Security Incidents (SSICS) lead to a cruise framework called “Strategies to Mitigate Cyber Security Incidents”. Here’s a breakdown of this framework
| Recover data and system availability | This type of restoration-orientated paradigm helps to reduce downtime duration following an attack. |
| Prevent malware delivery and execution | Bad software that is distributed and spread is a problem you have to ward off. |
| Limit the extent of cyber security incidents | Limit the extent of cyber security incidents: The objective is to restrict and quell the breach which could entail it becoming widespread. |
| Detect cyber security incidents and respond | Early and quick detection and reaction is the key to the identification and addressing of attacks timely and efficiently. |
The ACSC Mitigation Strategies
The framework outlines various strategies categorized by their effectiveness:
1. Essential Mitigation Strategies
This is the fundamental approach, which comprises the Eight Essential (of which Essential Eight is best known). They are a bedrock, data-driven cybersecurity and restrain severe threats as much as possible.
2. Excellent Mitigation Strategies
These tactics are grounded on the Essential strategies and then build up another protective shield on top of the first layer. Illustrations can be filtering email content, setting up network segmentation and user awareness campaigns.
3. Less Effective Mitigation Strategies
However, the effectiveness of these measures may be relative, based on unique circumstances, and compete for efficiency with the strategies that have been categorized in the tiers below.
Benefits of Implementing the Essential Eight
1. Stronger Defenses
Brings attackers multiple steps further from your systems, and thus, data extraction becomes a complicated job for them to perform.
2. Reduced Cyberattack Risk
Actively prevents implications of the commonly abused vulnerabilities applied by cybercriminals.
3. Minimized Damage
A major advantage is that it reduces the leverage that a successful attack may possess and speeds up the recovery process.
4. Improved Business Resilience
A formidable cybersecurity scheme realizes to a highly reliable business.
5. Demonstrated Security Commitment
Adherence to the essential eight gives you the guarantee that you are totally data protected. This could be interpreted as a plus to your reputation and will attract new partnerships.
Conclusion
ACSC Essential Eight framework gives organizations the basic and easy steps to follow to help how to strengthen their cybersecurity positions.
These strategies achieve the aim of developing a proactive data protection culture and appear to be more than enough to counter effectively cyberattack risks.












