Start Up Your Career in Cyber Security Before its too late...
- 1,00,000+ Students Trained
- 100% Placement Assistance
- Daily Live+Recorded Sessions
- 40+ Expert Trainers
What we are offering is not just Training.
But its Training + Internship + Certification all in One Cyber Security Training Program.
This is probably the best opportunity to procure an Internship, Training, Professional Experience, Real-time exposure to Cyber Security, and even opportunities to earn – Everything in one!
Learn Top 8+ In Demand Skills in just 6 Months!
The Best Thing is You Learn & Earn at the Same Time!
Enroll
Before
& Get FREE Membership of the Hacker's Club!
This is a Training + Job (Internship) program and is for those candidates who are passionate about Cyber Security and wish to pursue their career in Cyber Security. As one of the Best Cyber Security companies in Australia, we exactly know what the industry needs. And thus, we will provide you with industry-oriented training and experience, which is unique in the market and is job guaranteed.
Robin D Souza - Founder & Director CyberSapiens
Program Curriculum
We provide a very unique Industry Oriented Curriculum from basics to an advanced level.
The training covers 13 Modules which are divided into 3 Chapters – Basic, Advanced and Specialization.
Chapter 1: Basic
This chapter covers all the basic topics that companies expect in an individual. These topics help you to make your base strong in the Cyber Security domain.
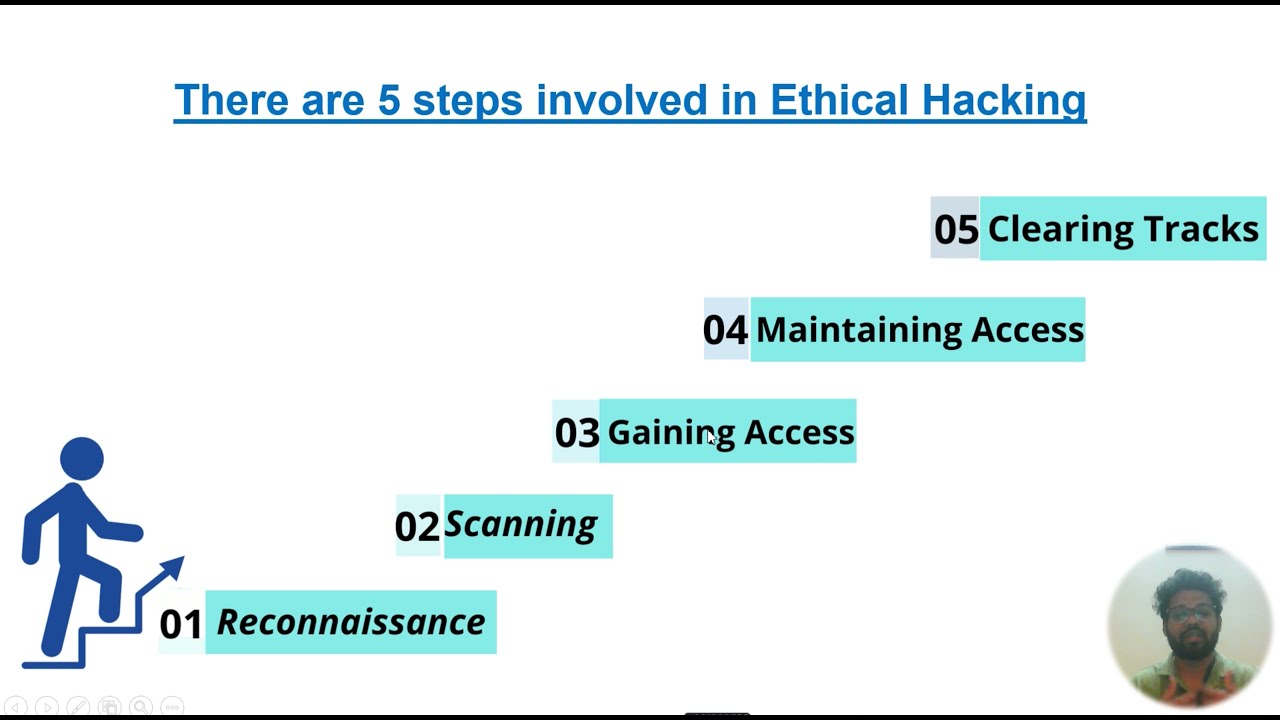
Module 1 – Foundation to Cyber Security
- Why Cyber Security & How it Works in an organization?
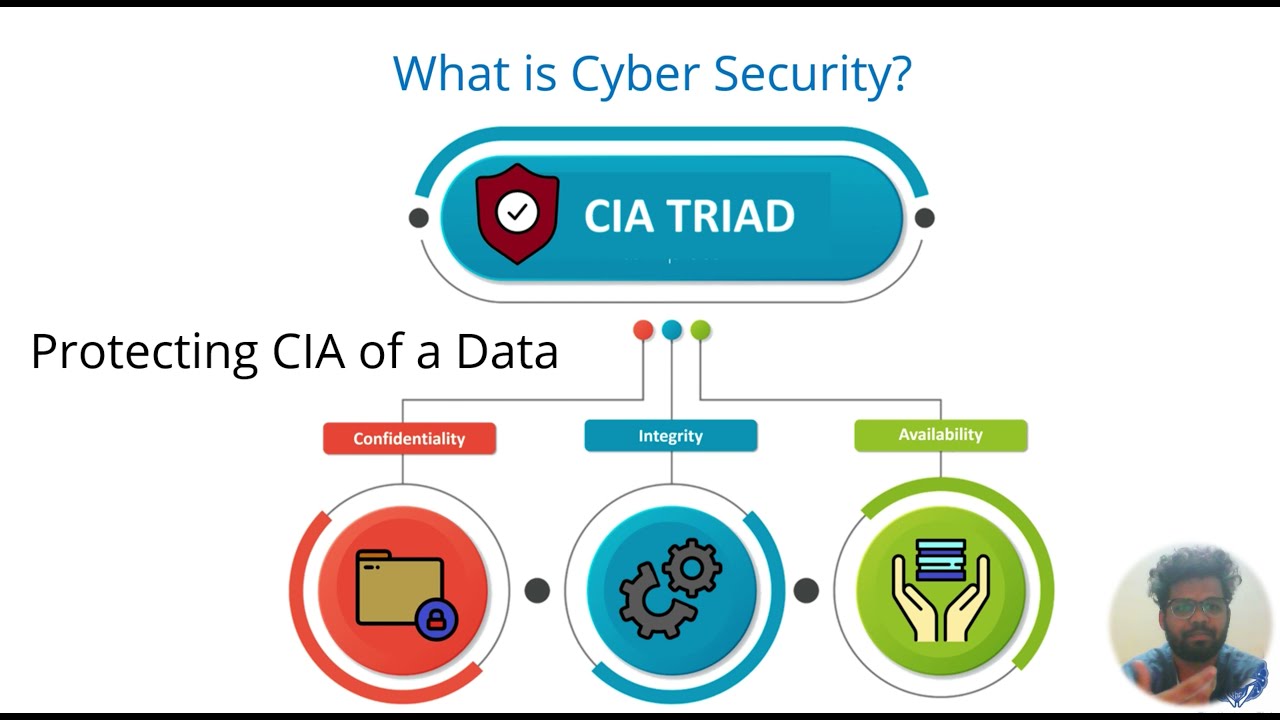
- CIA – The Three Pillars of Cyber Security
- Cyber Attacks & Data Breaches
- Classification of Information
- Domains in Cyber Security
- Job Roles and Designations in the organizations
- Controls, Standards & Regulations
- Protocols & Port Numbers
- Cryptography
- Digital Signatures
Chapter 2: Advance
This chapter covers all the advance topics of the cyber security domain from an industry perspective which is required for every cyber security professional. It especially covers the four primary topics – GRC, SOC, VAPT and Cloud which are the core domains in Cyber Security. This Chapter will help you in gaining a good weightage to your profile.
Module 2 – Vulnerability Management & Penetration Testing
- Introduction to VAPT
- Types of Pentesting
- VAPT Targets & Tools
- VAPT Report Writing & Documentation
- Skills required for VAPT
Module 3 – Network Security
- Network Security Concepts
- Defense in Depth
- Network Security Devices - DLP, Firewall, IDS-IPS, AV
- Network Segmentations
- Protocols - SSL, TLS, VPN
- Zero trust approach to network security
- Network Monitoring
Module 4 – Web Application Security
- Web Application Protocols
- OWASP Top 10
- Using Burp Suite Tool for Web VAPT
- Web VAPT Tools & Methods
- Information Disclosure Vulnerability
Module 5 – API Security
- Importance of API & API Pentesting
- API pentesting VS Traditional Web Pentesting
- API Documentation
- Postman Tool Introduction
- LAB Setup Demonstration
Module 6 – Mobile Application Security
- Introduction To Android & Android Architecture
- Introduction To IOS & IOS Architecture
- OWASP Mobile TOP 10
- Mobile Application Pentesting Process
Module 7 – Network VAPT & Attacks
- Network VAPT Types
- Tools for Network VAPT - Qualysis & Nessus
- Network Traffic Analysis
- Performing VA using nmap
- Creating automated nmap scripts for scanning
- Banner Grabbing Attack
- User Enumeration Attack
- Bruteforce Attack
- Password Cracking Attack
- Finding & Analysing CVE for Vulnerable services
Module 8 – Governance Risk & Compliance
- Introduction to GRC
- ISO 27001
- PCI DSS
- HIPAA
- NIST
- GDPR
- Data Privacy
- SOC Audits – SSAE16/SOC 1, SOC 2 & SOC 3
- Risk Management
- Security Audits
- Business Continuity
- Third Party Risk Management
- Compliance Management
Module 9 – Security Operations Centre (SOC)
- SOC Fundamentals
- SOC Team Roles and Responsibilities
- Security Information & Event Management
- Recognizing Security Incidents and Events
- Threat Intelligence
- Incident Detection & Response
- MITRE ATTACK
- Incident response procedures
- Security Alerts & Alarms
- Overview of Splunk
- Splunk architecture
- Installation of Splunk (Windows & Linux)
- Usage of Splunk in log analysis
Module 10 – Cloud Security
- Introduction to Cloud security
- Cloud Pentesting Methodology
- AWS Cloud Security
- Azure Cloud Security
Chapter 3: Specialization
This chapter is where you will be gaining the skills of a Penetration Tester for performing Web + API & of a Penetration Tester for performing Web + API & Mobile Pentesting and you will be working on live Mobile Pentesting and you will be working on live targets hunting for vulnerabilities. targets hunting for vulnerabilities.
Module 11 – Web Application VAPT & Attacks
- XSS & HTML Injection
- SQL Injection
- CORS & HSTS
- Host Header Injection & Password Reset Poisoning
- SSRF
- File Upload Vulnerabilities, LFI, RFI & File Path-traversal vulnerabilities
- CSRF
- Business Logic Vulnerabilities
- Business Logic Vulnerabilities
- XXE
- Subdomain Takeover & Broken Link Hijacking,
- Buffer Overflow & Long Password DoS Attack
- RCE & Command Injection
Module 12 – RCE & Command Injection
- Broken Object Level Authorisation
- Broken Authentication
- Broken Object Property Level Authorisation
- Unrestricted Resource Consumption
- Broken Function Level Authorisation
- Unrestricted Access to Sensitive Business Flows
- Server-Side Request Forgery
- Security Misconfiguration
- Improper Inventory Management
- Unsafe Consumption of APIs
Module 13 – Mobile Application (Android & iOS) VAPT & Attacks
- Setup of Tools in (Windows, Kali, Mac)
- Static & Dynamic Analysis (Android) Methods
- Static & Dynamic Analysis (iOS) Methods
- Insecure Data Storage
- Sensitive Data Exposure
- Input Validation and Manipulation
- Improper Platform Usage
- Insecure communication
- Insecure Authentication & Authorization
- Insufficient Cryptography & Poor Code Quality
- Code tampering
- Reverse Engineering
- Extraneous Functionality
Not only this we have got Additonal Suprises for you all!
Get these 2 additional courses along with the main Training Program…

Get CEH v12 Course of 40+ Hours for FREE along with this Program and register yourself as a Certified Ethical Hacker for V12

Get our Bug Hunting Essential Course which covers around 20 Web & API Bugs to become a Bug Hunter for FREE
Also Do Watch Our Free Demo Videos!
Free Cyber Security Demo Videos
Session 2 | CIA | Cyber Security Controls | Standards & Regulations | Cyber Security in Industry
1:08:33
Session 5 | Web Application Security | Protocols | TCP UDP | Cryptography | Hashing | Digital Signat
1:12:37Summary of What will be covered in the Training?
So the training will cover both the Compliance & Technical aspects of Cyber Security and as part of the Technical modules, you will learn 33 & + vulnerabilities to exploit in a manual way and not using any automated tools.
The exploitation will be first done on The Hackers Club machine and then once you practice, you then implement in real-time targets or in any private bug-hunting programs and earn rewards and/or awards.
THUS, AS PART OF THE TRAINING, WE WOULD COVER ALMOST EVERY ASPECT OF CYBER SECURITY AND THE PRIMARY FOCUS WOULD BE ON WEB APPLICATION SECURITY WHEREIN 30+ REAL-TIME WEB VULNERABILITIES WILL BE COVERED.
Summary of What will be covered in the Internship?
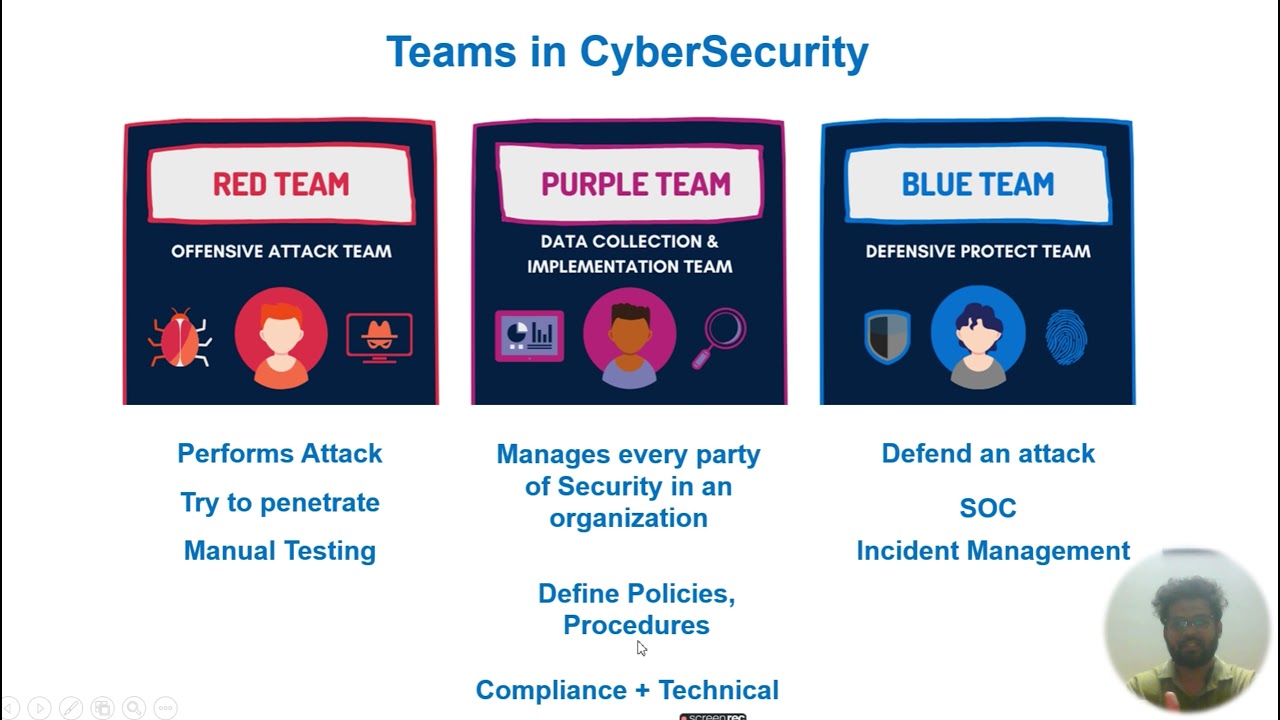
As part of the INTERNSHIP, you will be working for our Red Team projects for Threat Hunting.
Wherein we will assign you with real-time targets (companies) and you will need to assess these targets and identify the vulnerabilities and threats.
Apart from Threat Hunting, as part of the internship, you will be assigned with various tasks to work upon.
Tasks such as researching on topics and tools, security blog writing, conducting sessions, etc., which you would need to complete in the stipulated time.
Some more Perks You Get!!!
- Your performance will be monitored on a daily basis.
- Also a dedicated mentor will be assigned to you along with a reporting manager.
- We use Telegram application for day to day activities and discussions.
This is a Job-Oriented Program wherein you would be either promoted in our company with a fixed stipend or assisted for jobs outside.
At the end, you would have a training certificate and an experience certificate to kick start your career further.
What Qualifications You Need?
Anyone who has completed or pursuing their graduation or post-graduation can apply. Even those who are in the first, second, or final year can join us.
Required feasibility and time will be granted during examination time.
How to Apply for the Post?
If you find it worthy and interesting, please let us know by sending an email to [email protected] along with your resume, stating that you have gone through the document and videos, and would like to enroll in the internship.
Please note that there will be minimal fees to be paid for the Training, which will be communicated to you upon interest.
However, if you feel that you are knowledgeable and skilled, then please apply for the job position.
Achievements of Our Ethical Hackers!






















Take a Look at Monthly Internship Report of Our Students!
Most Frequently Asked Questions!
Yes, EMI is available and you can make payments in installments.
It helps in fighting against national security breaches and cyber terrorism, building a system that prevents penetration by hackers, protecting financial and security establishments, etc.
Yes, we will pay on your performance basis. Whenever you find and report a bug, you will be paid for that bug. The payment will depend on the level of the bug you find and on the client.
Individuals who hold the skills required for conducting Ethical Hacking get higher ranks in companies and get paid more than an average IT Professional.
During the Ethical Hacking training, you will learn various essential topics such as concepts of SQL injection, skill of wireless attacks, buffer overflow, etc. You will also learn about ethical hacking methodologies, network security, malware and malware analysis, and many more concepts.
Weekly 2-4 sessions will be taken depending on the vulnerabilities. As we will give one or two day time to practice the vulnerability covered.
Yes, you can join us this is a remote internship.
Yes, anyone from any part of the world can be a part of our Cyber Security Intern Training Program.
We have both remote as well as offline based. For offline, the candidate is required to be from Mangalore, Karnataka.
Any graduate or postgraduate with a keen interest in cyber security can join. Even Working professionals are invited to enroll in the training.
No need to pay complete fees at the beginning itself.
You can make a partial payment initially which can be any amount.
So once you confirm the joining, our HR will start with the onboarding process which includes background verification as well.
Once background verification is done, the offer letter will be released. That is when you are supposed to make the payment.
SMiShing, war driving, WPA attack, Bluejacking, replay attacks, bluesnarfing, and RF jamming are the different skill of wireless and mobile device attacks.
Yes, an experienced letter of 6 months will be provided to you as per your performance.
Yes, Cyber Security & Threat Hunting certificate will be awarded to you upon completion of the internship.
We too will refer you with the companies who have requirements and will also assist you with Resume Building, Mock Interviews, etc.,
Yes, this program is designed for fresher’s and beginners with no or little knowledge about computers or security.
We will be sharing our company’s Current Bank Account details and the transfer can be done through E-banking, Gpay, Cheque or DD.
Yes, this is job guaranteed. We will teach you 33 vulnerabilities in this program and these are all real time vulnerabilities and once you learn all of them, you can perform Bug Hunting and can easily get a job.
We too will refer you with the companies who have requirements and will also assist you with Resume Building, Mock Interviews, etc.,
The duration is 6 months, which includes Training and Internship together.
The training will be provided online either through Google Meet or Zoom.
There is no dedicated timings as such. Whatever tasks is given, it should be completed on the given timeline. In case of failure of competition, the candidate should inform the mentor, and exception will be given.
The training is divided into two modules, 1. Compliance & 2. Technical.
The idea is to train you on every domain in the security at least at a high level and the primary focus would be on Web App Security, wherein we will cover around 33+ vulnerabilities.
Yes, any working professional can join us as an Intern Trainee or as a member of The Hackers Club.
As an intern, you are required to work on the assigned tasks such as:
a. Writing blogs
b. Researching on topics
c. Working on tools
d. Working on assigned targets
e. Using LinkedIn daily
etc.,
Yes, as a student, you can join us. If you have exams or any other work, you will have to inform your mentor and seek for an exception. Upon approval, you will be given with exceptions.
At CyberSapiens, we prioritize providing valuable training services to our clients. We do not offer refunds for any of the payments made against the enrolments in any circumstances.
However, we understand at times certain unexpected situations may arise and therefore in such cases, participants have the flexibility to utilize their paid fees towards our services within the next 8 months.
In the event a refund is requested, it will be considered for a small portion of the amount only. Thus, we encourage participants to take advantage of this opportunity and engage with our services within the specified timeframe.