SOC 2 Compliance

SOC 2 Compliance Made Easy & Effortless!
Our team of experts is dedicated to providing comprehensive SOC 2 Compliance solutions tailored to your organization’s unique needs.
We guide you through the entire compliance journey, from assessment to implementation and ongoing maintenance, helping you navigate the complex requirements of SOC 2 compliance with confidence and ease.
Just fill out the form below to get in touch with us!!!
Our SOC 2 Compliance Process
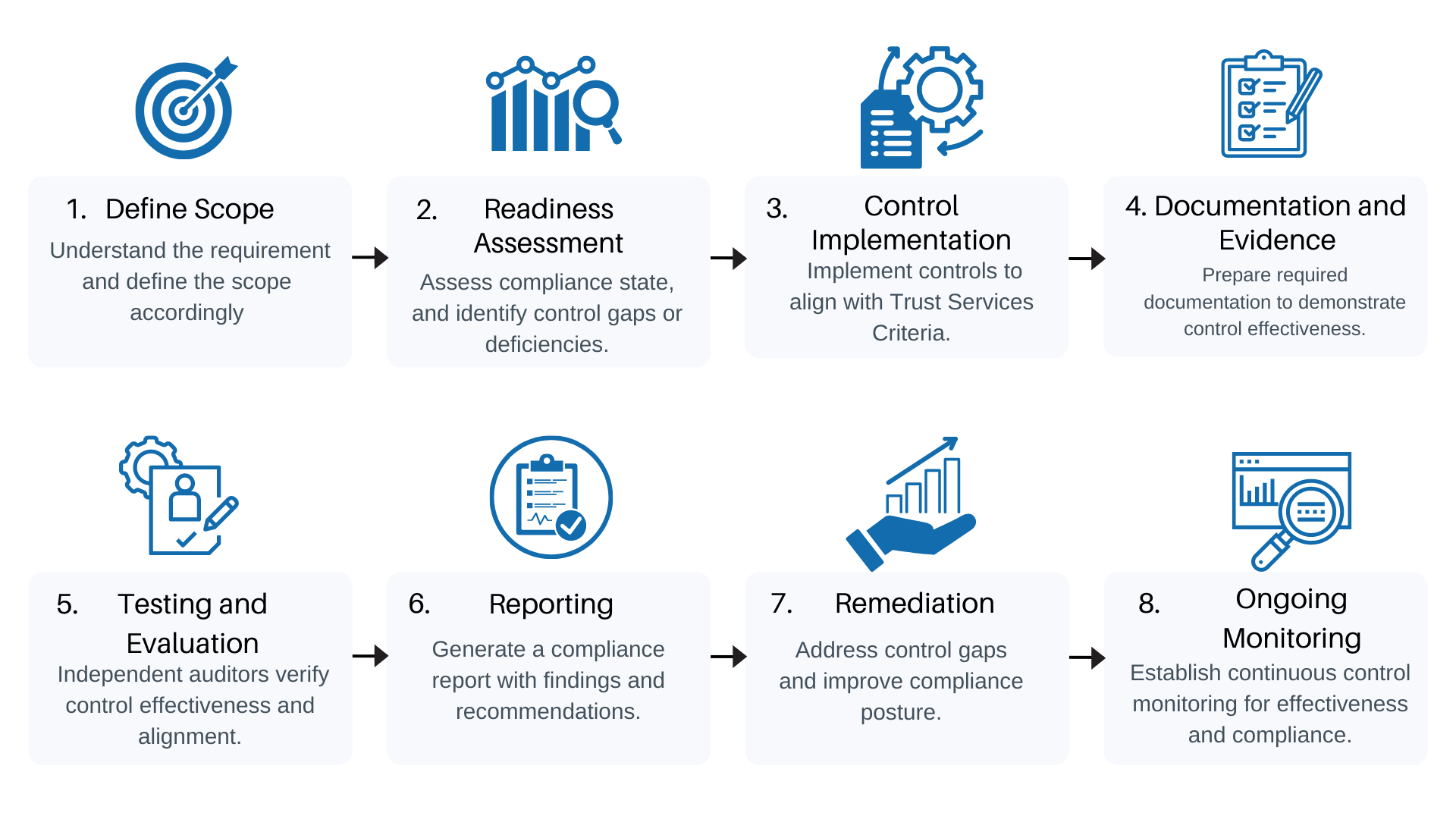

What is SOC 2 Compliance?
SOC 2 compliance is a critical aspect of establishing trust and credibility in today’s digital landscape.
It involves aligning an organization’s controls with the stringent Trust Services Criteria defined by the American Institute of CPAs (AICPA). By adhering to SOC 2 standards, businesses can demonstrate their commitment to maintaining high levels of security, availability, processing integrity, confidentiality, and privacy. SOC 2 compliance audits provide valuable insights into an organization’s control environment, assuring clients and stakeholders that their data and systems are protected.
It’s an essential step towards building a robust cybersecurity framework, mitigating risks, and gaining a competitive edge in an increasingly security-conscious market.
So, invest in SOC 2 compliance today to safeguard your business and inspire trust among your valuable customers.
Why your Organisation needs SOC 2 Compliance?
SOC 2 compliance is essential to establish consideration and credibility in the virtual age. It assures clients and stakeholders that a company has implemented robust controls to protect sensitive data and ensure the security, availability, processing integrity, confidentiality, and privacy of their information.
Through the present process of a SOC 2 audit, companies can show their dedication to industry-recognized requirements and satisfactory practices. SOC 2 compliance enables mitigating dangers, preventing statistics breaches, and meeting the increasing need for statistics safety and privacy. It offers groups an aggressive part, as clients prioritize operating with depended-on companions who prioritize the safety and integrity of their data.

Types of SOC 2 Compliance
There are 2 types of SOC 2 Compliance!
SOC 2 Type 1
The SOC 2 Type 1 report examines the performance of an organization’s controls over a specific period of time. It provides an overview of the branding that has been implemented, and assesses its suitability for achieving reliable service standards. This report provides stakeholders with insight into the design of controls and their alignment with established standards, assuring them that the organization has implemented the right processes to manage security , address availability, functional integrity, privacy, and confidentiality issues.
SOC 2 Type 2
A SOC 2 Type 2 report assesses the layout and operating effectiveness of an organisation's controls over a defined period, normally six to twelve months. It gives stakeholders a comprehensive know-how of ways nicely the controls had been carried out and operated over time. The file includes specified data approximately exams performed, results acquired, and any diagnosed manipulation deficiencies. SOC 2 Type 2 provides valuable insights into the continued adherence to the Trust Services Criteria, giving a higher degree of warranty concerning the effectiveness of controls.
Benefits of SOC 2 Compliance!
Enhanced Security
Compliance with SOC 2 regulations requires the implementation of strong security controls, ensuring the protection of sensitive data against unauthorized access and breaches.
Regulatory Compliance
SOC 2 compliance adheres to industry-specific regulations, helping your organization meet compliance requirements and avoid fines or legal issues.
Increased Client Trust
SOC 2 compliance demonstrates your commitment to data security and privacy, building trust with customers and stakeholders who value the security of their information.
Competitive Advantage
SOC 2 compliance sets you apart from competitors by demonstrating your commitment to data security and privacy, giving you a competitive edge in the marketplace.
Operational Efficiency
SOC 2 compliance encourages the implementation of standardized processes and systems, leading to improved performance and efficiency.
Risk Mitigation
SOC 2 compliance involves identifying and mitigating risks, allowing you to address vulnerabilities and strengthen your risk management processes.
Vendor Due Diligence
SOC 2 compliance helps facilitate a vendor's due diligence process as potential customers can trust that they have implemented effective controls to protect their data.
Improved Internal Processes
A SOC 2 compliance process often highlights areas of improvement within your organization, allowing you to improve your internal processes and security measures.

Certified Company!

Why Choose Us for your SOC 2 Compliance Audit?
Reach Compliance at your own pace
Establish Roadmap & Stay on Target
Save time & money
Ensure you meet the control requirements
Ensure you pass your certification audit
Ensure you maintain certification every year
Certified Company!


Get In Touch
By filling this form ↓
FAQ's
The time to achieve SOC2 compliance varies based on factors such as the complexity of your organization's systems and processes, current security measures in place, and the adequacy of your internal controls.
At CyberSapiens, we work closely with businesses to assess their unique needs and create a timeline that fits their unique circumstances, ensuring a smooth and efficient compliance journey.
Businesses often face challenges such as defining the scope of a compliance assessment, identifying and addressing security gaps, implementing the necessary controls, and documenting policies and procedures.
Our experienced team at CyberSapiens understands these challenges and provides expert guidance and support throughout the compliance process to overcome these hurdles.
We conduct a thorough gap analysis to assess your current security practices against SOC2 requirements.
Based on the findings, we develop a customized roadmap including recommendations and implementation strategies to close any gaps. We guide you through the process of aligning your current practices with SOC2 requirements, ensuring a seamless transition to compliance.
Failure to comply with SOC2 can result in reputational damage, loss of customer confidence, legal and regulatory implications, and potential financial loss.
Achieving SOC2 compliance demonstrates your commitment to security and helps mitigate these risks by establishing strong internal controls and protecting customer data.
Absolutely! Our team of experts at CyberSapiens has extensive experience in developing and implementing security policies and processes consistent with SOC2 requirements.
We work closely with your organization to understand your specific needs, provide customized templates and guidance, and help implement strong security policies and procedures.
At CyberSapiens, we make protecting your organization's sensitive data a priority. We follow strict confidentiality and data security protocols, using industry-standard encryption and access controls.
Our team handles your data with utmost care and follows best practices to ensure its confidentiality, integrity and availability during the SOC2 compliance process.
SOC2 compliance requires continuous efforts to maintain the required level of security and control.
At CyberSapiens, we help you establish processes and controls to ensure continued compliance.
We offer regular assessments, monitoring and guidance to help you maintain a strong security posture and adapt to changing requirements over time.
Yes, employee training and awareness are important aspects of SOC2 compliance.
We provide comprehensive training programs tailored to your organization's needs.
We educate your employees on the importance of SOC2 compliance, their roles and responsibilities, and best practices for maintaining security controls and protecting sensitive data.
At CyberSapiens, we understand that different industries have specific compliance requirements. We have experience working with diverse sectors and tailor our SOC2 compliance services to meet industry-specific needs.
Our team has the industry knowledge and expertise to effectively address your unique compliance challenges.
The cost of achieving and maintaining SOC2 compliance depends on a variety of factors, such as the size and complexity of your organization, the scope of the compliance assessment, and the level of support required.
At CyberSapiens, we provide transparent pricing based on your specific needs, ensuring that you receive value-driven services with no hidden costs.
Absolutely! We guide you through the entire SOC2 audit process, helping you prepare for the audit and ensuring you have the necessary documentation, controls and evidence in place.
Our experts offer comprehensive support to make the audit experience smooth and successful.
SOC2 compliance offers several benefits beyond meeting regulatory requirements.
It enhances your organization's security posture, strengthens customer confidence, improves your competitive advantage, and demonstrates your commitment to protecting sensitive data.
It also provides a framework for continuous improvement and helps you stay ahead of evolving security threats.
Yes, we provide assistance in resolving audit findings and implementing remedial measures. Our team helps you understand audit findings, develop effective remediation strategies, and implement the necessary improvements to align with SOC2 requirements.
We work with you to ensure that any identified gaps are promptly addressed and corrected.
At CyberSapiens, we have a team of highly skilled professionals with extensive experience in assisting organizations with SOC2 compliance. Our experts have in-depth knowledge of SOC2 requirements, best practices, and industry standards.
With our proven track record, we are well equipped to guide you through the compliance process and help you achieve your compliance goals.
Yes, we offer ongoing support and guidance even after achieving SOC2 compliance. We provide monitoring services, periodic assessments and ongoing guidance to ensure you maintain your compliance status and keep up with security threats and regulatory changes.
Our goal is to establish a long-term partnership and support your organization's ongoing compliance journey.
SOC2 compliance demonstrates your organization's commitment to data security and serves as a valuable benchmark for vendor selection and third-party risk management.
This allows you to assess the security controls and practices of potential vendors and partners, ensuring they meet your compliance standards and protect your sensitive data.
Absolutely! We assist in developing the documentation required for SOC2 compliance, including policies, procedures, control frameworks, and evidence collection templates.
Our experts ensure that your documentation meets SOC2 requirements and best practices, saving you time and effort in preparing the required documentation.
SOC2 compliance demonstrates your organization's commitment to data security and privacy.
This instills confidence in your customers that their sensitive information is safe. By achieving and maintaining SOC2 compliance, you can enhance your organization's reputation, build trust with customers, and establish long-lasting relationships based on a strong security foundation.
SOC2 Type 1 assesses the design and implementation of controls at a specific point in time, providing a snapshot of an organization's controls.
SOC2 evaluates the effectiveness and operational efficiency of Type 2 controls over a period of time, typically spanning at least six months.
Choosing between SOC2 Type 1 and Type 2 depends on your organization's goals. If you want to show the design and implementation of controls, Type 1 is appropriate.
If you want to demonstrate the effectiveness of controls and ongoing operation, Type 2 is recommended.






