The increasing adoption of cloud computing in the United Kingdom has led to a significant shift in the way businesses operate and store their data.
Cloud computing offers numerous benefits such as scalability, flexibility, and cost-effectiveness, but it also poses a unique set of security challenges.
One of the most effective ways to address these challenges is through Cloud Vulnerability Assessment and Penetration Testing (VAPT) also known as Cloud Security Testing.
In this article, we will explore the top 15 reasons why Cloud VAPT is important for businesses in the United Kingdom.
List of Top 15 Reasons Why Cloud VAPT is Important for Businesses in the United Kingdom

Here is the list of the Top 15 Reasons Why Cloud VAPT is Important for Businesses in the UK:
1. Protection Against Cyber-Attacks
Thus, Cloud VAPT plays a pivotal role in safeguarding businesses in the UK from cyber threats. As it is aware that cloud computing environments are most attractive targets to hackers and cyber-attackers, a VAPT assessment exposes many of the gaps and flaws in the system.
These are ways through which different businesses can avoid such attacks since their data is at high risk of being attacked.
2. Compliance with Regulations
There are several legal measures and requirements for the protection and safeguarding of data in the UK, for instance; the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
Cloud VAPT can assist organizations shows compliance to these regulations by establishing threats and openings in cloud infrastructures.

3. Reduced Risk of Data Breaches
Cloud VAPT can act as a solution to this threat by pointing out gaps and flaws in cloud environments hence helping organizations minimize threats.
An incident of data breach may result in the following negative implications; loss of money, poor image and fines.
It also creates vulnerabilities and weaknesses that one can avoid in order not to be a victim of hackers or cyber criminals aiming at getting too sensitive business information.
4. Improved Incident Response
Therefore when there is a cyber-attack or data breach, a Cloud VAPT can be useful in enabling quick and adequate responses.
Because companies become aware of threats and risks in their cloud computing systems, they can build up strategies that can help them to respond to any incident consequences as well as reduce the amount of time that will be taken before the cloud environment is up and running again.
5. Enhanced Security Posture
The Cloud VAPT is very useful to businesses in the sense that it can improve their defensive position in the event of a cloud computing attack.
All these vulnerabilities and weaknesses if treated result in the enhancement of the firm’s security level thus minimizing cyber threats and attacks.
6. Identification of Misconfigurations
It has been established that Cloud VAPT can assist organizations in detecting misconfigurations of the cloud computing environment. There are always possibilities to misconfigure a system expose sensitive data, and compromise security, and getting a VAPT assessment done helps to avoid such misconfigurations from becoming very large problems.
7. Reduced Risk of Unintended Data Exposure
Cloud VAPT can assist the enterprise in minimizing the chance of inadvertent disclosure of data by scanning the cloud structures for risks and susceptibilities.
It can also happen when the customer data is accidentally placed in an unprotected bucket in the cloud or in a situation whereby an unauthorized person receives access to the information.
8. Compliance with Industry Standards
Cloud VAPT can assist organisations in how they can adhere to compliance both at regional and international levels including SOC 2, ISO 27001 and PCI DSS.
These standards force the firm to ensure security controls and measures for the protection of such data and a VAPT enables organizations to show compliance with those standards.
9. Enhanced Reputation
Thus, carrying out consistent Cloud VAPT can be an excellent way of proving the security and data protection measures of companies. This can give them a better brand image and credibility with their customers, affiliates and investors.
10. Cost Savings
Cloud VAPT can assist businesses in reducing costs as it will address vulnerabilities and weaknesses in a cloud computing environment.
By so doing, issues that act as vulnerabilities and weaknesses to cyber-attacks and data breaches are spotted and dealt with hence minimizing the impacts of financial losses that are a result of the attacks.
11. Identification of Vulnerabilities in Cloud Services
Cloud VAPT can assist organizations to detect the threats that are associated with cloud services including AWS, Azure as well as Google Cloud Platform.
These weaknesses can lead to leakage of data as well as security breaches and a VAPT assessment has the potential of realizing these mishaps.
12. Improved Cloud Security Governance
It will aid Cloud VAPT in enhancing the cloud security governance of businesses by revealing gaps in organisations’ cloud computing architectures.
By closing the aforementioned vulnerabilities and weaknesses organizations can establish sound mechanisms for cloud security governance in a way that maintains security as well as compliance.
13. Reduced Risk of Insider Threats
Through Cloud VAPT, insiders can be protected since the business environments that have been adopted in cloud computing can be tested for weaknesses and vulnerabilities.
An insider has authorized access to a system and then either knowingly or unknowingly puts the organizational security at risk, and a VAPT assessment will come in handy in detecting such anomalies before they assume catastrophic proportions.
14. Identification of Hidden Backdoors
Real-life examples state that Cloud VAPT can assist corporate enterprises in discovering additional concealed backdoors in cloud computing surroundings.
There are, in particular, hidden backdoors that, if not properly addressed, may lead to leakage of sensitive data and other security threats; all these should be determined through a VAPT assessment.
15. Enhanced Cloud Security Maturity
Cloud VAPT acts as a useful solution to check and improve the security maturity of an organisation to assess risks and loopholes in cloud computing.
Pinning down these vulnerabilities and weaknesses, business people can come up with well-coordinated cloud security strategies that enhance security and compliance.
Top 5 Best Practices for Cloud VAPT
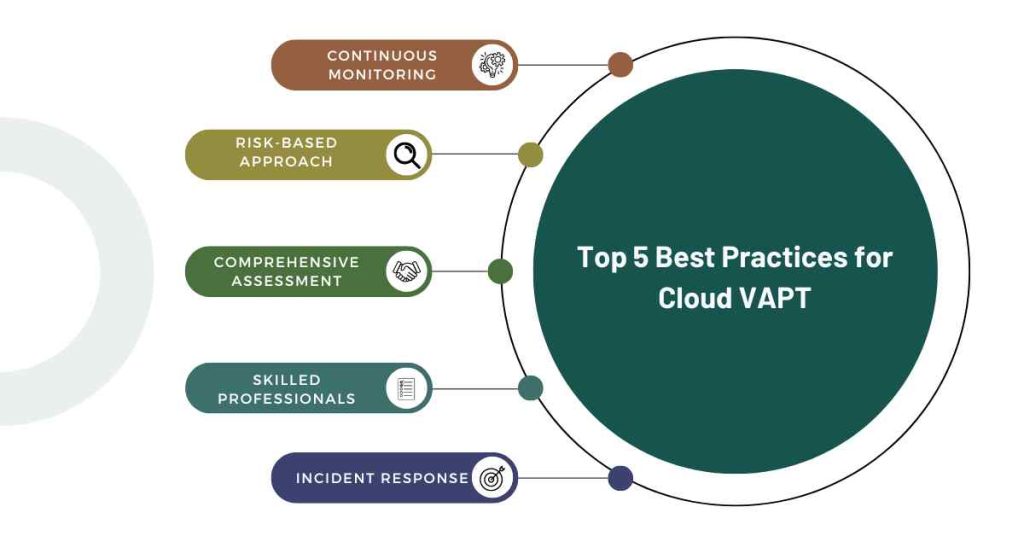
To ensure effective Cloud VAPT, businesses should follow best practices such as:
1. Continuous Monitoring
Conduct regular security scanning of the firm’s cloud computing environments to identify critical vulnerabilities and risk areas.
2. Risk-Based Approach
Risk assessment should be taken out to determine which aspects or systems are most vulnerable and which are not very robust.
3. Comprehensive Assessment
Carry out advanced VAPT assessments that would incorporate all cloud services and applications.
4. Skilled Professionals
Use experienced people in cloud security to do vulnerability assessment and penetration testing.
5. Incident Response
Create contingency plans that would enable handling of such risks as well as reducing the time of disruption.
Summary
Here is the Summary of the ” Top 15 Reasons Why Cloud VAPT is Important for Businesses in the United Kingdom” article.
- 1. Protection Against Cyber-Attacks
- 2. Compliance with Regulations
- 3. Reduced Risk of Data Breaches
- 4. Improved Incident Response
- 5. Enhanced Security Posture
- 6. Identification of Misconfigurations
- 7. Reduced Risk of Unintended Data Exposure
- 8. Compliance with Industry Standards
- 9. Enhanced Reputation
- 10. Cost Savings
- 11. Identification of Vulnerabilities in Cloud Services
- 12. Improved Cloud Security Governance
- 13. Reduced Risk of Insider Threats
- 14. Identification of Hidden Backdoors
- 15. Enhanced Cloud Security Maturity
Conclusion
In conclusion, it is highly recommended that Cloud VAPT should be adopted by organizations operating in the United Kingdom that utilize cloud computing platforms, and subenvironments for storing and processing critical information.
In this way, enterprises define the list of risks that their cloud computing environments might face and find necessary actions to protect against cyber threats, decrease the likelihood of insider attacks, and enhance their security situation in general.
In addition, Cloud VAPT can assist organizations in proving that they are compliant with the legal requirements and guidelines, protect from unintentional data leakage, and improve the company’s image and cloud security management. Thus, the Cloud VAPT should be conducted periodically to guarantee security and compliance in cloud computing, as well as the security of the information that is classified as critical.
FAQs: Top 15 Reasons Why Cloud VAPT is Important for Businesses in the United Kingdom
1. What is Cloud VAPT?
Ans: Cloud VAPT stands for Cloud Vulnerability Assessment and Penetration Testing. It is a comprehensive security assessment that identifies vulnerabilities and weaknesses in cloud computing environments.
2. Why is Cloud VAPT important for my business?
Ans: Cloud VAPT is important for your business because it helps identify vulnerabilities and weaknesses in your cloud computing environment, which can be exploited by hackers and cyber-attackers. By addressing these vulnerabilities, you can prevent cyber-attacks and data breaches, reduce the risk of insider threats, and improve your overall security posture.
3. What are the benefits of Cloud VAPT?
Ans: The benefits of Cloud VAPT include:
Improved security posture
Reduced risk of cyber-attacks and data breaches
Enhanced compliance with regulations and industry standards
Reduced risk of insider threats
Improved incident response
Enhanced reputation and trust with customers, partners, and stakeholders
4. How does Cloud VAPT work?
Ans: Cloud VAPT involves a comprehensive security assessment that includes:
Vulnerability scanning and identification
Penetration testing to identify weaknesses and vulnerabilities
Risk assessment to prioritize vulnerabilities and weaknesses
Recommendations for remediation and mitigation
5. Who should perform Cloud VAPT?
Ans: Cloud VAPT should be performed by skilled professionals with expertise in cloud security. This can include internal security teams, third-party security vendors, or cloud service providers.
6. How often should Cloud VAPT be performed?
Ans: Cloud VAPT should be performed regularly, ideally every 3-6 months, to ensure that your cloud computing environment is secure and compliant.
7. What are the different types of Cloud VAPT?
Ans: There are two main types of Cloud VAPT:
Compliance-based Cloud VAPT: This type of Cloud VAPT focuses on ensuring compliance with regulations and industry standards.
Risk-based Cloud VAPT: This type of Cloud VAPT focuses on identifying and prioritizing vulnerabilities and weaknesses based on risk.
8. How long does Cloud VAPT take?
Ans: The length of Cloud VAPT can vary depending on the complexity of the cloud computing environment and the scope of the assessment. Typically, Cloud VAPT can take anywhere from a few days to several weeks to complete.
9. Can I perform Cloud VAPT myself?
Ans: While it is possible to perform Cloud VAPT yourself, it is not recommended. Cloud VAPT requires specialized skills and expertise, and attempting to perform it yourself can lead to incomplete or inaccurate results.
10. Is Cloud VAPT expensive?
Ans: The cost of Cloud VAPT can vary depending on the scope and complexity of the assessment. However, the benefits of Cloud VAPT far outweigh the costs, and it is a small price to pay for the security and peace of mind that comes with knowing that your cloud computing environment is secure and compliant.












