In recent years, the Internet of Things (IoT) has revolutionised the way businesses operate in Australia. IoT devices have enabled organizations to streamline processes, improve efficiency, and enhance customer experience. However, with the growing adoption of IoT devices, the risk of cyber threats has increased exponentially. As a result, it has become essential for businesses to prioritize IoT device Vulnerability Assessment and Penetration Testing (VAPT) to protect their sensitive data and prevent financial losses.
In this article, we will discuss the top 15 reasons why IoT device VAPT is crucial for businesses in Australia.
List of Top 15 Reasons Why IoT Device VAPT is Important for Businesses in Australia

Here is the list of Top 15 Reasons Why IoT Device VAPT is Important for Businesses in Australia
1. Protection against Data Breaches
The IoT devices can help to accumulate and relay personal and corporate data, which are a primary objective for hackers. Lack of security features exposes business organizations to data loss and since such data is worth money losing it would be likened to losing cash and the company’s reputation suffers too. VAPT can also assist in knowing the IoT devices that are at risk and how to secure vital data.
2. Compliance with Australian Regulations
Australian firms are subject to numerous laws and rules including the Privacy Act 1988, and rules set by the Australian Prudential Regulation Authority (APRA). These regulations require sound security measures to be put in place in organisations that process such information. VAPT can assist organizations in fulfilling the compliance requirements of these regulations.
3. Prevention of Financial Losses
‘Common, but damaging, financial losses come with the costs of responding to the attack, fixing the affected IoT devices, and recovering the reputational loss. VAPT can describe gaps in IoT devices that may lead to money loss.
4. Reduced Risk of Denial of Service (DoS) Attacks
The privileged attackers can easily launch a DoS attack on the IoT devices and in the process lead to a disconnect between the devices and their networks. Using VAPT one can identify other issues that these IoT devices may be having, and in the process, make sure that these devices cannot be used to launch DoS attacks.
5. Prevention of Malware and Ransomware Attacks
Malicious activities such as virus and malware attacks and ransomware attacks on IoT devices present great threats to business organizations. The use of VAPT means is also useful for classifying IoT devices that may been left open for potential malware and ransomware to infect.
6. Protection of Endpoints
Other endpoints include sensors, cameras and actuators; IoT devices can communicate between themselves as well as with such attached peripherals. This is because VAPT can ascertain that the endpoints are in the correct state of defenceless against the cybercons.
7. Improved Brand Reputation
If IoT devices are hacked, a business will lose customer trust because its brand reputation will be at risk. Through VAPT, a business can avoid any cyber threats that may exist and also can maintain its brand image intact.

8. Compliance with Industry Standards
Many industry frameworks like ISO 27001 and the PCI-DSS call on an organization to have measures in place to safeguard sensitive information. Thus, VAPT can assist businesses in providing compliance with these standards.
9. Reduced Risk of Intellectual Property Theft
Since IoT devices possess the capability to store the data of their users and third parties, they also entail a high risk of exposing documented IP, encompassing algorithms and the code of embedded applications and software. It can also help in the defence against the nuances of theft and other types of unauthorized usage/access of IP.
10. Protection of Critical Infrastructure
The Internet of Things (IoT) devices are already embedded in high-risk areas like power utility, transportation and health services. VAPT can therefore help in the security of such systems against cyber risks.
11. Reduced Risk of Physical Harm
The primary risk of cyber threats affects IoT devices, which risk delivering physical harm to persons and organizations. Through VAPT, an organization can be able to come up with ways of getting it right in as far as the security of IoT devices is concerned and also an organization should be in a position to ensure that such devices are patched against various cyber attacks.
12. Improved Incident Response
VAPT can assist business organisations in coming up with response measures on how to handle an instance of an IoT device being compromised.
13. Reduced Risk of Insider Threats
One of the main risks for IoT devices is represented by insider threats meaning that people working for the organization or contracting services for the same represent a great danger. Forest, VAPT can assist in discovering problems with IoT devices and make sure they are protected from threats from insiders.
14. Improved Security Awareness
Through the use of VAPT, awareness can be provided to the personnel and contractors which shall safeguard the IoT devices from cyber threat.
15. Improved Return on Investment (ROI)
By implementing VAPT, businesses can reduce the risk of cyber-attacks on IoT devices, which can improve ROI and optimize business operations.
How to Implement VAPT in IoT Devices?
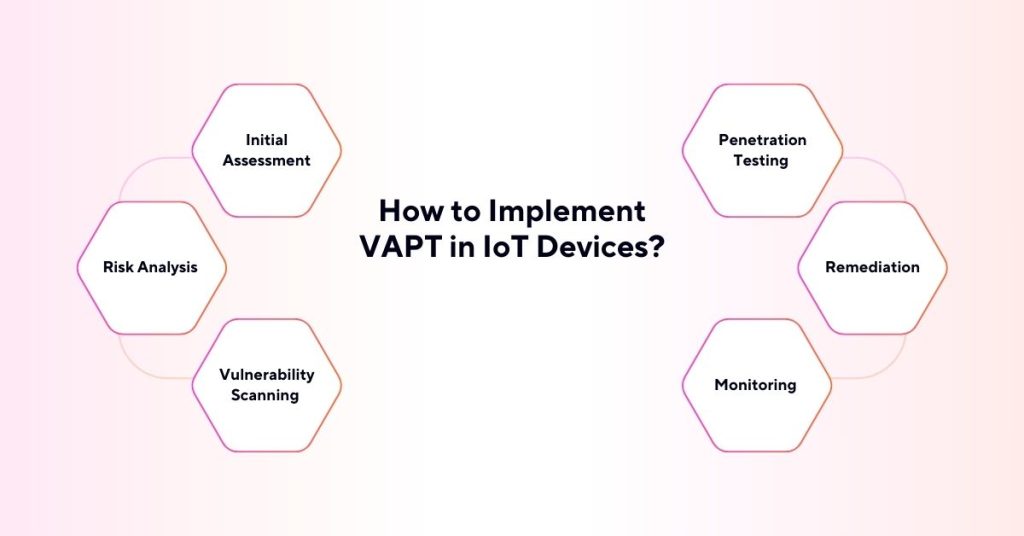
Implementing VAPT in IoT devices requires a structured approach, which includes the following steps:
1. Initial Assessment
Conduct a first scan to explore the vulnerabilities to IoT devices.
2. Risk Analysis
Arrange all the demonstrated risks according to the level of risk on an as-administered schedule.
3. Vulnerability Scanning
Use heavy scanning to determine the exact vulnerability that is inherent in the IoT devices.
4. Penetration Testing
Perform vulnerability assessment scans, megalog and their IOT-based mirage of hackers.
5. Remediation
Make corrections to the vulnerabilities mentioned below and implement effective security patches.
6. Monitoring
Press the importance of the continuous search for vulnerabilities and cyber threats within IoT devices.
Conclusion
In conclusion, IoT device VAPT is essential for businesses in Australia to protect their sensitive data, prevent financial losses, and ensure compliance with regulations and industry standards. By implementing VAPT, businesses can reduce the risk of cyber-attacks on IoT devices and improve their return on investment. We highly recommend that businesses in Australia prioritize VAPT to ensure the security and integrity of their IoT devices.
Summary
- Protection against Data Breaches
- Compliance with Australian Regulations
- Prevention of Financial Losses
- Reduced Risk of Denial of Service (DoS) Attacks
- Prevention of Malware and Ransomware Attacks
- Protection of Endpoints
- Improved Brand Reputation
- Compliance with Industry Standards
- Reduced Risk of Intellectual Property Theft
- Protection of Critical Infrastructure
- Reduced Risk of Physical Harm
- Improved Incident Response
- Reduced Risk of Insider Threats
- Improved Security Awareness
- Improved Return on Investment (ROI)
FAQs
1. What is IoT Device VAPT?
Ans: IoT Device VAPT (Vulnerability Assessment and Penetration Testing) is a security testing process that identifies vulnerabilities in IoT devices and simulates cyber-attacks to determine the potential impact of those vulnerabilities.
2. Why is IoT Device VAPT necessary?
Ans: IoT Device VAPT is necessary to identify vulnerabilities in IoT devices and prevent cyber attacks that can lead to financial losses, reputational damage, and compromise of sensitive data.
3. What are the benefits of IoT Device VAPT?
Ans: The benefits of IoT Device VAPT include protection of sensitive data, prevention of financial losses, compliance with regulations and industry standards, and improved brand reputation.
4. What are the steps involved in IoT Device VAPT?
Ans: The steps involved in IoT Device VAPT include initial assessment, risk analysis, vulnerability scanning, penetration testing, remediation, and monitoring.
5. How often should IoT Device VAPT be performed?
Ans: IoT Device VAPT should be performed regularly, ideally every 6-12 months, or as part of a continuous monitoring and testing program.
6. What is the difference between vulnerability scanning and penetration testing?
Ans: Vulnerability scanning is an automated process that identifies potential vulnerabilities in IoT devices, while penetration testing simulates cyber-attacks on IoT devices to determine the potential impact of those vulnerabilities.
7. What are the most common vulnerabilities found in IoT devices?
Ans: The most common vulnerabilities found in IoT devices include weak passwords, outdated software, and lack of encryption.
8. How can IoT Device VAPT help comply with regulations and industry standards?
Ans: IoT Device VAPT can help comply with regulations and industry standards by identifying vulnerabilities in IoT devices and ensuring that they are addressed, which demonstrates compliance with regulations and industry standards.
9. Can IoT Device VAPT be performed in-house or must it be outsourced?
Ans: IoT Device VAPT can be performed in-house or outsourced, depending on the resources and expertise of the organization. It is recommended to outsource IoT Device VAPT to a reputable and experienced security testing partner.
10. How can IoT Device VAPT help improve incident response?
Ans: IoT Device VAPT can help improve incident response by identifying vulnerabilities in IoT devices and developing incident response plans to quickly respond to cyber attacks on IoT devices.












