In the realm of web security, two common threats continue to pose significant risks to individuals, organizations, and businesses alike Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF). While both attacks exploit vulnerabilities in web applications, they differ in their intentions, execution, and mitigation strategies.
In this article, we will delve into the details comparison of both Cross Site Scripting Vs Cross Site Forgery, exploring their differences, consequences, and prevention techniques.
What is Cross-Site Scripting (XSS)?
Cross-site scripting is a type of web vulnerability that enables attackers to inject malicious JavaScript code into a vulnerable web application.
When an unsuspecting user interacts with the infected webpage, the injected code executes on their browser, allowing the attacker to steal sensitive information, such as login credentials, or take control of the user’s session.
XSS attacks are usually initiated when an application that accepts information from web users does not adequately check the content of the information it receives.
For instance, when a user inserts data into a form, a web application may fail to sanitize it and may allow an attacker to inject more scripts into the webpage. The injected code can again be run through the user’s browser, which results in a security violation.
3 Types of XSS Attacks
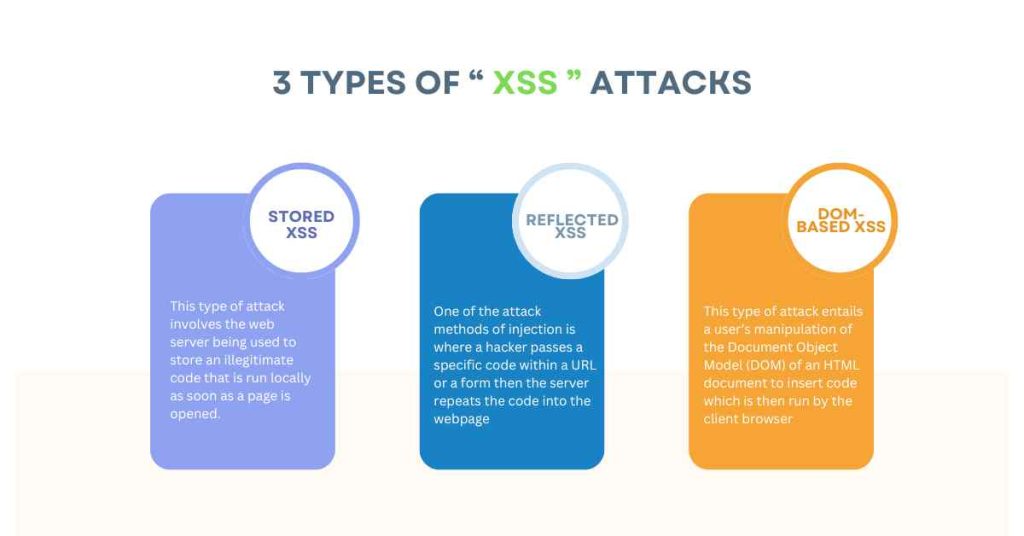
There are three primary types of XSS attacks:
1. Stored XSS
This type of attack involves the web server being used to store an illegitimate code that is run locally as soon as a page is opened.
2. Reflected XSS
One of the attack methods of injection is where a hacker passes a specific code within a URL or a form then the server repeats the code into the webpage.
3. DOM-based XSS
This type of attack entails a user’s manipulation of the Document Object Model (DOM) of an HTML document to insert code which is then run by the client browser.
What is Cross-Site Request Forgery (CSRF)?
Cross-site request Forgery is another type of web vulnerability that helps attackers manipulate users into executing undesired operations on any web application.
This is done by taking advantage of the confidence that the user has placed in the web application by tricking the user browser into making unauthorized requests to the weak application.
CSRF attacks often occur where the web application is unable to handle appropriate mechanisms for authentication and authorization; this results in the attacker’s impersonation of legal requests from the target user’s browser.
3 Types of CSRF Attacks
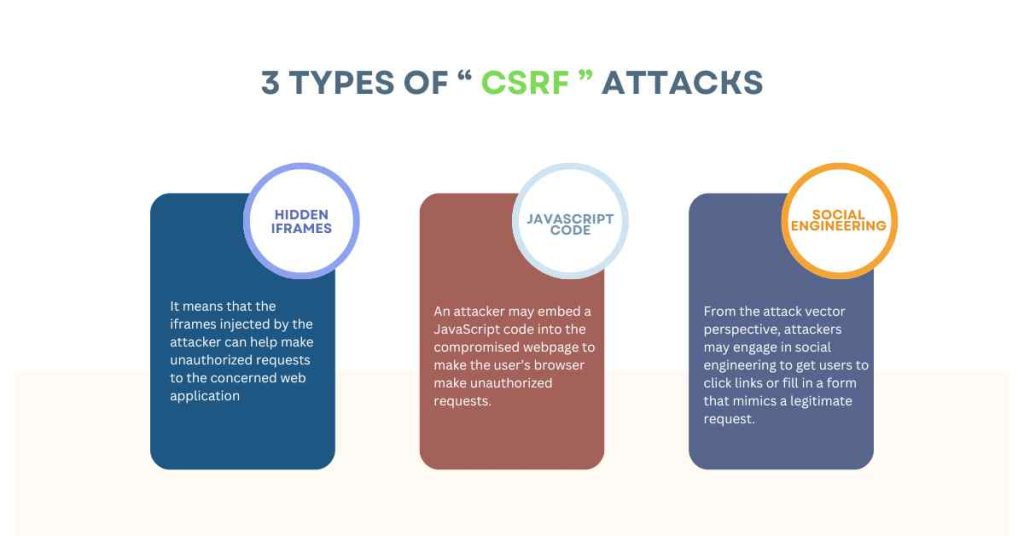
The attacker may use various tactics to achieve this, including:
1. Hidden iframes
It means that the iframes injected by the attacker can help make unauthorized requests to the concerned web application.
2. JavaScript code
An attacker may embed a JavaScript code into the compromised webpage to make the user’s browser make unauthorized requests.
3. Social engineering
From the attack vector perspective, attackers may engage in social engineering to get users to click links or fill in a form that mimics a legitimate request.
Consequences of XSS and CSRF Attacks
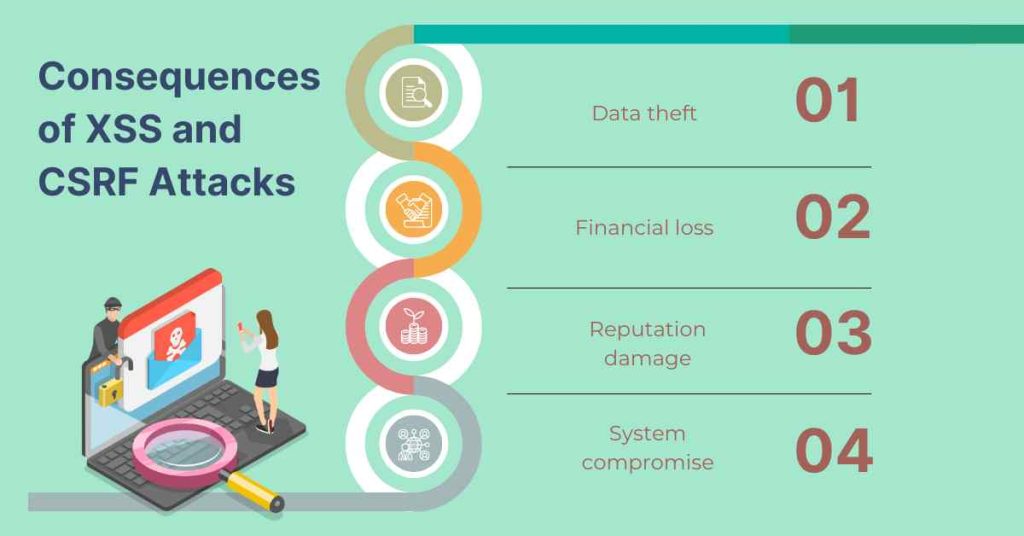
Both XSS and CSRF attacks can have severe consequences for individuals, organizations, and businesses. Some of the potential consequences include:
1. Data theft
XSS and CSRF attacks are relatively dangerous because their implementation gives the hacker complete permission to access sensitive information like login details, credit information and other personal information.
2. Financial loss
Criminals may use the data or can make them perform actions that such users will not do willingly such as performing fraudulent transactions.
3. Reputation damage
Successful attacks can destroy the reputation of a certain organization and affect the trustworthiness of users.
4. System compromise
Sometimes, XSS and CSRF attacks can be used to gain complete control of the system, after which other malicious activities can be conducted.
Comparison of Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF)
Here is the full Comparison of Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) please go through the below table for a clear understanding:
| Category | XSS | CSRF |
| Intent | Execute malicious code on the user’s browser | Trick users into performing unintended actions on the vulnerable web application |
| Execution | Inject malicious code into a webpage | Manipulate the user’s browser into sending unauthorized requests to the vulnerable application |
| Attack Type | Stored, Reflected, DOM-based | Hidden iframes, JavaScript code, social engineering |
| Vulnerability | Failure to validate and sanitize user input | Lack of authentication and authorization mechanisms |
| Consequences | Data theft, financial loss, reputation damage, system compromise | Data theft, financial loss, reputation damage, system compromise |
| Mitigation | Input validation and sanitization, Content Security Policy (CSP) | Token-based validation, secure coding practices |
| Complexity | Can be complex to execute, but also simple if vulnerabilities exist | Relatively simple to execute, as it relies on user interaction |
| Detection | Difficult to detect, as it involves analyzing user input and code execution | Can be detected through analysis of user interaction and system activity |
| Prevention | Implementing robust input validation and sanitization, CSP | Implementing token-based validation, secure coding practices, regular security audits |
| Risk Level | High, as it can lead to sensitive data theft and system compromise | High, as it can lead to sensitive data theft and financial loss |
| Frequency | Common, as many web applications have input validation and sanitization vulnerabilities | Less common, but still a significant threat due to the lack of authentication and authorization mechanisms |
Conclusion
Cross-site scripting and cross-site request forgery are two dangerous web vulnerabilities that are dangerous to individuals organizations and businesses.
It is important to differentiate these attacks for the right prevention measures to be taken and how to minimize them. Hence, by employing secure coding standards, token base validation and security scaring the developers and the organization would reduce the frequency of XSS & CSRF attacks.
FAQs: Cross-Site Scripting Vs Cross-Site Forgery
1. What are the differences between XSS and CSRF?
Ans: XSS is designed to execute malicious code on the user’s browser, while CSRF is designed to trick users into performing unintended actions. Additionally, XSS involves injecting malicious code into a webpage, while CSRF involves manipulating the user’s browser into sending unauthorized requests.
2. How can I prevent XSS attacks?
Ans: To prevent XSS attacks, implement robust input validation and sanitization, use a Content Security Policy (CSP), and conduct regular security audits to identify and address vulnerabilities in web applications.
3. How can I prevent CSRF attacks?
Ans: To prevent CSRF attacks, implement token-based validation, use secure coding practices, and conduct regular security audits to identify and address vulnerabilities in web applications.
4. Can XSS and CSRF attacks occur simultaneously?
Ans: Yes, XSS and CSRF attacks can occur simultaneously, as they both exploit vulnerabilities in web applications. It is essential to address both types of attacks to ensure the security of web applications.
5. Are XSS and CSRF attacks common?
Ans: Yes, XSS and CSRF attacks are common, as many web applications have input validation and sanitization vulnerabilities (XSS) or lack authentication and authorization mechanisms (CSRF).
6. What are the consequences of XSS and CSRF attacks?
Ans: Both XSS and CSRF attacks can lead to sensitive data theft, financial loss, reputation damage, and system compromise.
7. Can XSS and CSRF attacks be detected easily?
Ans: No, XSS and CSRF attacks can be difficult to detect, as they involve analyzing user input and code execution (XSS) or user interaction and system activity (CSRF).
8. What is the best way to ensure the security of web applications?
Ans: The best way to ensure the security of web applications is to implement robust security measures, including input validation and sanitization, token-based validation, secure coding practices, and regular security audits, to identify and address vulnerabilities in web applications.
9. How do I protect myself from XSS and CSRF attacks as a user?
Ans: To protect yourself from XSS and CSRF attacks as a user, use strong passwords, keep your browser and plugins up to date, avoid suspicious links and attachments, and use reputable antivirus software.
10. Where can I learn more about XSS and CSRF attacks?
Ans: You can learn more about XSS and CSRF attacks by visiting reputable websites, such as OWASP, W3Schools, and Web Security Tutorials, that provide information on web security and vulnerabilities.