E-commerce has become a booming industry, with numerous startups emerging every day. As these startups build their web applications to cater to their online customers, they often overlook one crucial aspect – security.
The consequences of neglecting security can be disastrous, resulting in data breaches, financial losses, and damage to their reputation.
According to a report by IBM, the average cost of a data breach is around $3.86 million. For startups, such a financial blow can be catastrophic.
In this article, we will discuss the Top 10 Major Ecommerce Security Threats Startups Face When Building a Web Application.
List of Top 10 Major Ecommerce Security Threats Startups Face When Building a Web Application
Here is the list of the Top 10 Major e-commerce security Threats Startups Face When Building a Web Application:
1. SQL Injection (SQLi)
Web application threat is of SQL injection type in which unauthorized SQL commands are injected into the application’s database. This enables the hackers to get what they want such as credit card numbers, user names and passwords among others.
SQL injection attacks are very dangerous, however, there are a few things that Startups can do to guard against them such as; using prepared statements, input validation, and constantly updating your Database software.
2. Cross-Site Scripting (XSS)
Another threat prevalent in web applications is Cross-Site Scripting (XSS), which is an attack that involves injecting application code – in this case, JavaScript, into a web application. It makes way for an unauthorized party to gain access to the system, and transfer session cookies and login information to themselves.
To sum up, the startups can defend themselves by input validation, output encoding and CSP implementation.
3. Cross-Site Request Forgery (CSRF)
A cross-site request forgery (CSRF) is a form of web application security threat, where a user is tricked into performing specific actions in a web application they otherwise have no intention of executing.
This can result in the breakdown of security control where hackers may control user accounts, make unauthorized purchases and even steal users’ information.
CSRF can be prevented by startups through token-based validation, header-based validation and through the use of a library that offers CSRF protection.
4. Unvalidated Redirects and Forwards
Invalid redirects and forwards are also some of the general web application security concerns where hackers can manipulate URL redirections to gain customers’ data and credentials or even install malicious programs into the customer’s devices.
These are measures that startups can take: Validate URLs, utilize whitelist filtering, and do not use redirects to vulnerable sites.
5. Weak Password Recovery and Storage
Stored password breach and recovery is another common insecurity in web applications whereby hackers get easy access to users’ data through a weak password or password reset.
Major risks can be mitigated in the following ways: Strong password policies, the appropriate password hashing algorithms, and secure password resets.
6. Command Injection
Web application vulnerability describes a situation in which an attacker injects another system command into a web application. This lets hackers gain full control of the underlying system, even installing viruses and Trojans, in addition to siphoning off sensitive information.
Startups should protect themselves through the use of statements that have been prepared, input validation, and regular updates on the software they use.
7. Broken Authentication and Session Management
This is a web application security threat that occurs when hackers can exploit weaknesses in authentication or session management mechanisms to access sensitive data.
To reduce the vulnerability of starting a company the following strategies should be taken; perform authentication and authorization on the client side, avoid using cookies to store the user’s identification details, and always ensure that the software is updated to the latest versions.
8. Malware and Ransomware
Malware is a web application security threat wherein hackers implant unwanted software into a web application while ransomware is whereby hackers compromise web applications and encrypt user data to force the user to make payment.
Startups have to manage powerful security controls, update software, and use anti-malware and anti-ransomware software.
9. Denial of Service (DoS) and Distributed Denial of Service (DDoS)
DoS and DDoS are varieties of aggressive web application security risks that see hackers bring overwhelming amounts of traffic to a particular web application in order to make it inaccessible to its users.
This can be achieved through increased security control that is implemented on the startups, load balancing as well as outsourcing to a professional web application security organization.
10. Zero-Day Exploits
Zero-day are a class of attacks against web applications which include taking advantage of ‘holes’ in software still unknown to the vendor.
Businesses should update their software generously, adopt good patterns of security controls, and find an advisor from the web application security services.
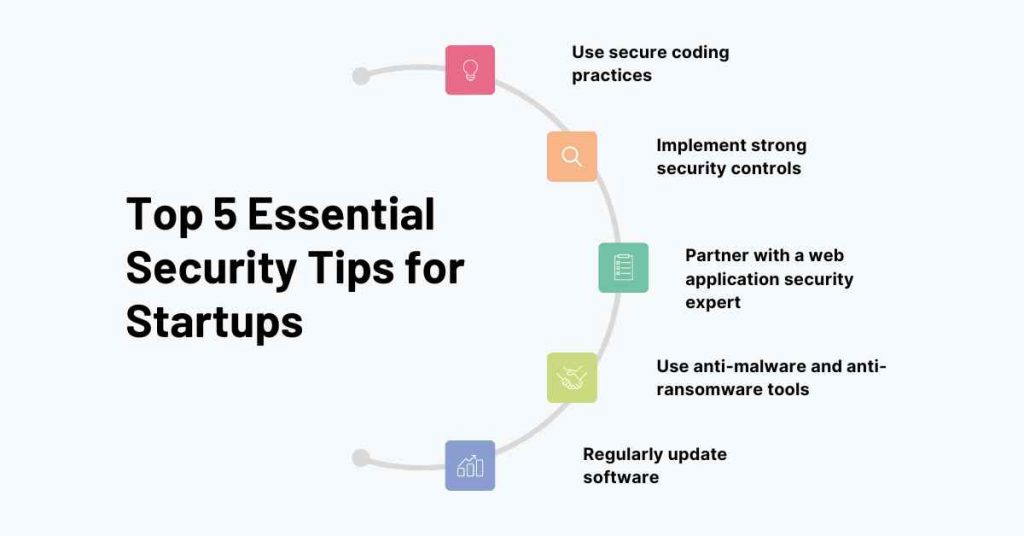
Top 5 Essential Security Tips for Startups
By following these recommendations, startups can protect themselves and their customers from e-commerce security threats and build a secure web application that meets the needs of their online customers.
1. Use secure coding practices
Using managed parameters, validated inputs, and passwords hashed using a good password hashing algorithm can provide absolute protection against SQL injection, cross-site scripting, and weak password recovery and storage.
2. Implement strong security controls
Install the latest version of the software, and use load balancer and token base validation to prevent CSRF or DDoS attacks.
3. Partner with a web application security expert
Entrepreneurs can benefit from a web application security expert because they can determine the weaknesses and strengthen the security measures.
4. Use anti-malware and anti-ransomware tools
To secure against malware attacks use anti-malware and for securing against ransomware attacks, use anti-ransomware.
5. Regularly update software
It helps users keep their system up to date to prevent operating on a zero-day vulnerability and other malicious attacks.
Summary
Here is the summary for the blog title Top 10 Major Ecommerce Security Threats Startups Face When Building a Web Application.
- SQL Injection (SQLi)
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Unvalidated Redirects and Forwards
- Weak Password Recovery and Storage
- Command Injection
- Broken Authentication and Session Management
- Malware and Ransomware
- Denial of Service (DoS) and Distributed Denial of Service (DDoS)
- Zero-Day Exploits
Conclusion
Ecommerce security threats are real, and startups need to be aware of the risks involved when building a web application.
By understanding the top 10 major e-commerce security threats, startups can proactively protect themselves and their customers. This includes using secure coding practices, implementing strong security controls, and partnering with a web application security expert.
FAQs: Top 10 Major Ecommerce Security Threats Startups Face When Building a Web Application
1. What is the most common e-commerce security threat that startups face?
Ans: The most common e-commerce security threat that startups face is SQL injection (SQLi). This is a type of web application security threat that involves injecting malicious SQL code into a web application’s database.
2. How can startups protect themselves against cross-site scripting (XSS) attacks?
Ans: Startups can protect themselves against cross-site scripting (XSS) attacks by using input validation, output encoding, and implementing a Content Security Policy (CSP). They can also use secure coding practices and regular security testing to identify vulnerabilities.
3. What is the difference between a denial of service (DoS) and a distributed denial of service (DDoS) attack?
Ans: A denial of service (DoS) attack involves a single hacker overwhelming a web application with traffic to make it unavailable to users. A distributed denial of service (DDoS) attack involves multiple hackers from different locations overwhelming a web application with traffic.
4. How can startups protect themselves against malware and ransomware attacks?
Ans: Startups can protect themselves against malware and ransomware attacks by implementing strong security controls, regularly updating their software, and using anti-malware and anti-ransomware tools.
5. What is a zero-day exploit, and how can startups protect themselves against it?
Ans: A zero-day exploit is a type of web application security threat that involves hackers taking advantage of previously unknown vulnerabilities in software. Startups can protect themselves against zero-day exploits by regularly updating their software, implementing strong security controls, and partnering with a web application security expert.
6. How can startups prevent weak password recovery and storage?
Ans: Startups can prevent weak password recovery and storage by implementing strong password policies, using secure password hashing algorithms, and providing secure password reset mechanisms.
7. What is the impact of e-commerce security threats on a startup’s reputation?
Ans: E-commerce security threats can have a devastating impact on a startup’s reputation. A data breach or security incident can lead to a loss of customer trust, negative reviews, and a loss of revenue.
8. How can startups ensure the security of their e-commerce platform when outsourcing development?
Ans: Startups can ensure the security of their e-commerce platform when outsourcing development by working with reputable development partners, implementing strong security controls, and regularly testing for vulnerabilities.
9. What is the cost of not implementing e-commerce security measures?
Ans: The cost of not implementing e-commerce security measures can be significant. A data breach or security incident can result in financial losses, regulatory fines, and damage to a startup’s reputation.
10. How can startups stay up-to-date with the latest e-commerce security threats and best practices?
Ans: Startups can stay up-to-date with the latest e-commerce security threats and best practices by attending security conferences, reading industry blogs and reports, and partnering with a web application security expert.












