In cybersecurity, understanding the systems and services within a network is often the first step in defence and attack. Whether you’re an ethical hacker performing penetration testing or a malicious actor seeking vulnerabilities, one technique is almost universally relied upon during this initial reconnaissance phase banner grabbing.
Despite its simplicity, banner grabbing can provide deep insights into network configurations, potentially revealing critical weaknesses. In this article, we will explore Mastering Banner Grabbing, its importance in Network Vulnerability Assessment and Penetration Testing (VAPT), and demonstrate how it can be practically applied using tools like Netcat, Telnet, and Nmap to grab banners from an SSH port.
What is Banner Grabbing?
Banner grabbing is a technique used to retrieve the details of services running on open ports. When a client connects to a network service (such as SSH), that service often responds with a banner a string of metadata that typically reveals information such as the service name, version number, and sometimes even the operating system it’s running on.
This information, while intended for diagnostics, can inadvertently expose crucial details that attackers can use to find security flaws. In many cases, the banner can help identify whether the system is running outdated software, unpatched versions, or misconfigured services all of which are potential entry points for exploitation.
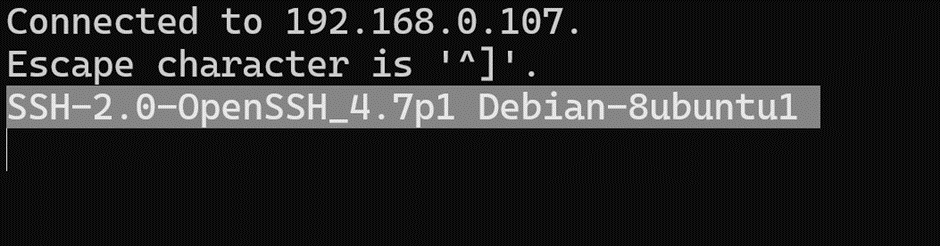
IMG 1: Example of a network service banner displaying software and version details for SSH server
The Role of Banner Grabbing in VAPT
Banner grabbing is an integral part of the reconnaissance phase of Vulnerability Assessment and Penetration Testing (VAPT). Here’s why it’s so important:
- Service Identification: The primary purpose of banner grabbing is to identify the services running on open ports. By determining what software and versions are being used, testers can more accurately assess potential vulnerabilities. This information is critical for further stages of testing, where known exploits for specific software can be leveraged.
- Vulnerability Detection: Once the software version is known, testers can cross-reference that information with known vulnerabilities in public databases, such as the Common Vulnerabilities and Exposures (CVE) database. If a vulnerable version is detected, it can help testers (or attackers) prioritize their next steps.
- Attack Surface Evaluation: Banner grabbing contributes to the overall understanding of an organization’s attack surface. If a service reveals excessive details about its software or version, it’s indicative of poor configuration management. Reducing these exposures can mitigate the likelihood of a successful attack.
- Informed Exploitation: Knowing the exact version of a service running on a target system enables attackers to refine their exploitation methods. For example, if a specific version of OpenSSH is known to be vulnerable to a specific attack, the attacker’s efforts can be focused on exploiting that particular weakness.
Active Banner Grabbing: Practical Demonstrations
1. Banner Grabbing with Netcat
Netcat is a versatile and simple tool for banner grabbing. It can establish a raw connection to a network service, allowing you to manually send and receive data.
Example: Let’s grab the banner from an SSH server running on port 22.
nc 192.168.0.115 22The SSH service should respond with a banner like:
SSH-2.0-OpenSSH_7.1This banner indicates that the SSH server is running OpenSSH 7.1on Debian, which can provide insights into potential vulnerabilities if there are known issues with this version.
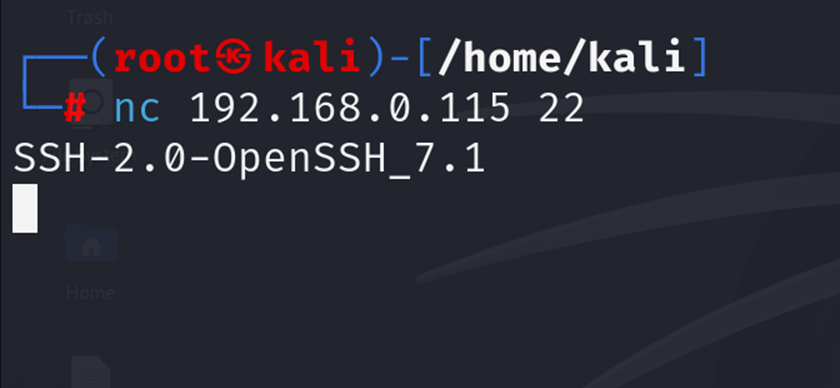
IMG 2: Terminal screenshot demonstrating banner grabbing using Netcat on SSH port, showing OpenSSH server response
2. Banner Grabbing with Telnet
Telnet, while less secure, can also be used for banner grabbing. It’s often used for quick checks.
Example: To grab the banner from the SSH server using Telnet:
telnet 192.168.1.10 22The SSH server will respond with a banner similar to:
SSH-2.0-OpenSSH_7.1Telnet will establish a connection and show the service’s banner, which helps identify the software and its version.
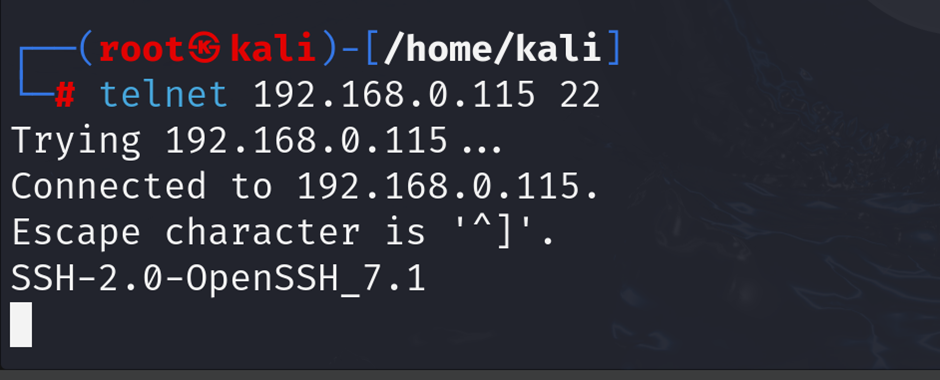
IMG 3: Telnet session capturing SSH banner after connecting to port 22
3. Automated Banner Grabbing with Nmap
Nmap automates the banner-grabbing process and provides a comprehensive view of the network by scanning multiple ports simultaneously.
Example: To scan a target system for open ports and gather banner information, use:
nmap -sV 192.168.1.10Nmap will output details like:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.1 (protocol 2.0)The -sV flag enables service version detection, which automates the process of gathering banners from various services, including SSH.
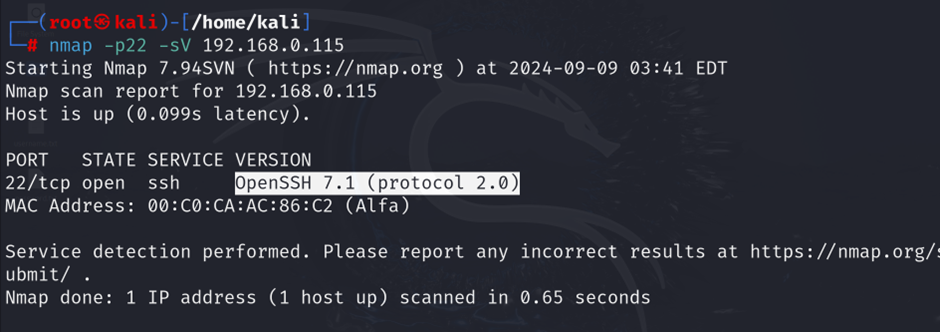
IMG 4: Nmap scan result showing open SSH port and banner information with OpenSSH version details
Passive Banner Grabbing: Analysing Network Traffic with Wireshark
Wireshark is a powerful tool for capturing and inspecting network traffic. It can also be used for passive banner grabbing by observing traffic between systems.
Example:
- Start Wireshark and begin capturing traffic on the relevant network interface (e.g., eth0 or wlan0).
- Use a filter to isolate SSH traffic, such as:
tcp.port == 22Inspect the captured packets to find the SSH service banner. For example, you might see:
Protocol: SSH-2.0-OpenSSH_7.1This method allows you to gather banner information without directly interacting with the target system, making it a stealthier option.
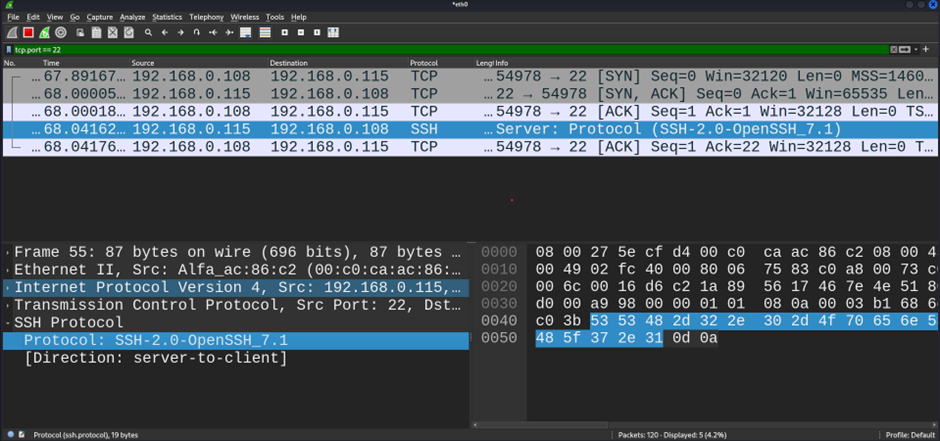
IMG 5: Wireshark interface capturing network traffic and showing SSH response banner
Best Practices for Protecting Against Banner Grabbing
While banner grabbing is a valuable technique for penetration testers, it can also expose vulnerabilities. Here are some best practices to minimize risks:
- Disable Banners: Configure services to suppress version numbers and other details in their banners. For SSH, ensure that the Banner option is not set or configured to show minimal information.
- Patch and Update Software: Regularly update services to their latest versions to avoid exploitation of known vulnerabilities.
- Implement Firewalls and IDS: Use network firewalls and Intrusion Detection Systems (IDS) to monitor and block unauthorized scanning attempts.
Special thanks
Dheeraj Prabhu K, Senior Security Analyst at CyberSapiens, for contributing his expertise to this content.
Conclusion
Banner grabbing, though simple, is an essential technique during the reconnaissance phase of network vulnerability assessments and penetration tests. By gathering service and version information, ethical hackers and attackers alike can identify weak points in a network’s defence. Tools like Netcat, Telnet, and Nmap make it easy to actively gather banners, while Wireshark provides a more passive approach.
From a security perspective, minimizing the information disclosed through banners is crucial in reducing your attack surface. Configuring services to withhold version details and regularly updating software can limit the effectiveness of reconnaissance techniques, protecting your network from potential threats before they escalate.












