Network Vulnerability Assessment and Penetration Testing (VAPT) are essential cybersecurity practices designed to identify and exploit vulnerabilities in network infrastructure. By proactively identifying weaknesses, organizations can mitigate risks and protect their sensitive data.
This document will explore common vulnerabilities identified during VAPT, their potential consequences, and the techniques used to effectively assess these vulnerabilities, including detecting common vulnerabilities in network VAPT.
1. Open Ports and Services
- Description: Open ports on a network device expose services that could be exploited by attackers. Each open port represents a potential entry point into the network.
- Common Risks: Attackers can utilize open ports to execute unauthorized commands, access sensitive data, or launch attacks such as Denial of Service (DoS).
Testing Methods:
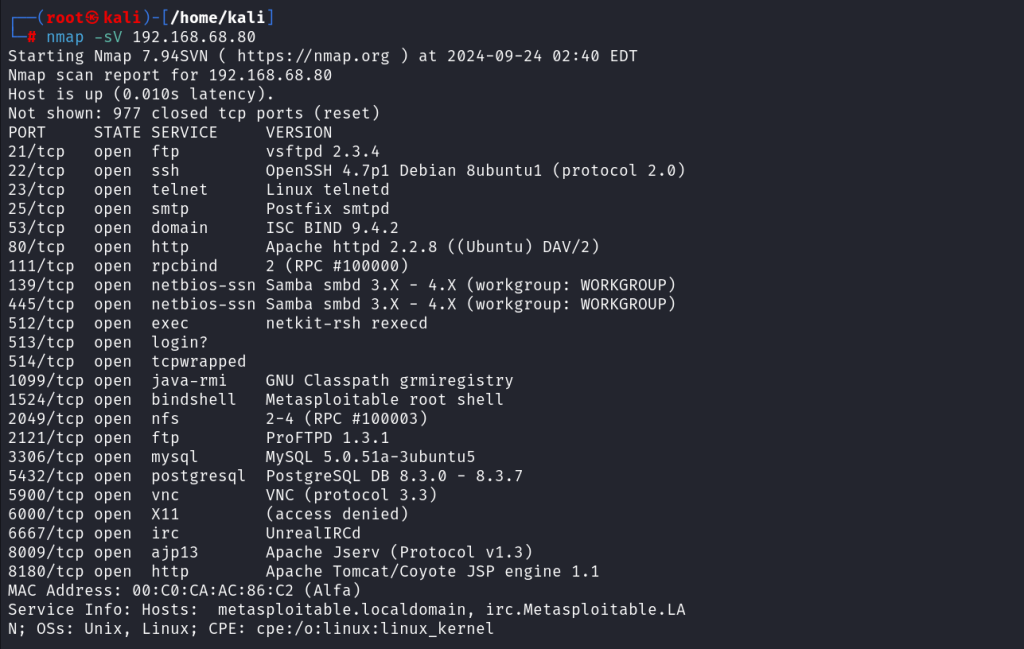
- Port Scanning: Use tools like Nmap or Netcat to perform scans of the target IP range to identify open ports.
- Service Enumeration: Utilize Nmap’s service/version detection (-sV) to identify running services and their versions, determining if they are outdated or vulnerable.
IMG 1: Diagram illustrating common open ports and associated risks in network security
2. Unpatched Software/Operating Systems
- Description: Unpatched software and operating systems are susceptible to known vulnerabilities that attackers can exploit.
- Common Risks: Exploiting unpatched vulnerabilities can lead to unauthorized access, data breaches, and system compromises.
Testing Methods:
- Vulnerability Scanning: Implement scanners such as Nessus, OpenVAS, or Qualys to identify unpatched software and vulnerabilities.
- CVE Database Checks: Cross-reference installed software versions against public databases (CVE) to identify known vulnerabilities.
IMG 2: Flowchart showing the process for identifying unpatched software vulnerabilities
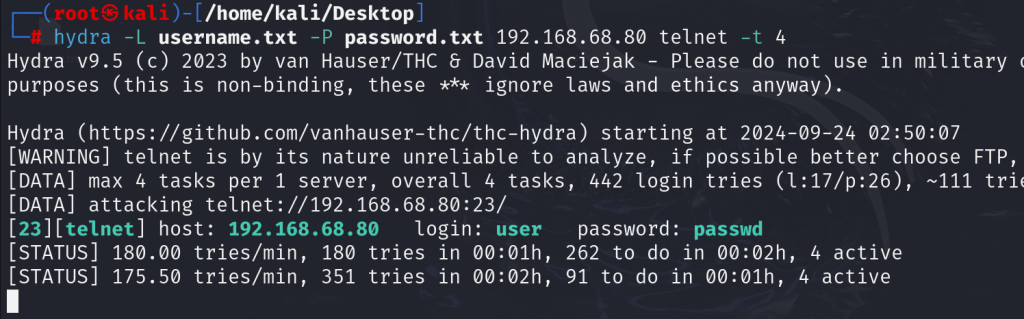
3. Weak Passwords or Default Credentials
- Description: Weak or default passwords provide an easy entry point for attackers. Many devices come with factory-set credentials that are well-known.
- Common Risks: Attackers can gain immediate access to systems and sensitive data if default or weak passwords are used.
Testing Methods:
- Password Cracking: Utilize brute-force tools like Hydra or Medusa to attempt to crack weak passwords.
- Default Credential Testing: Test common usernames and passwords (e.g., admin) against services to identify vulnerabilities.
IMG 3: Image depicting weak password examples and testing strategies
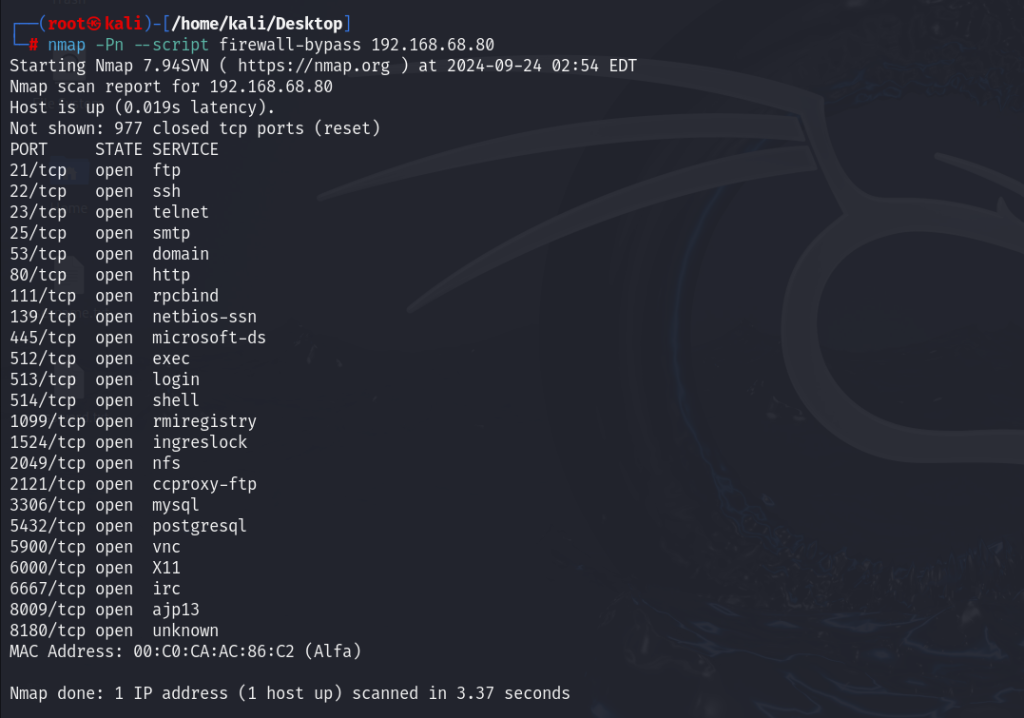
4. Misconfigured Firewalls or ACLs
- Description: Firewalls and Access Control Lists (ACLs) are critical for securing network traffic, but misconfigurations can lead to exposure.
- Common Risks: Misconfigured firewalls can allow unauthorized access and create opportunities for attacks.
Testing Methods:
- Firewall Probing: Use tools like Nmap or Firewalk to identify firewall rules and configurations.
- ACL Review: Analyse ACLs to ensure they are appropriately set to restrict access based on the principle of least privilege.
IMG 4: Illustration of firewall misconfigurations and their potential impacts
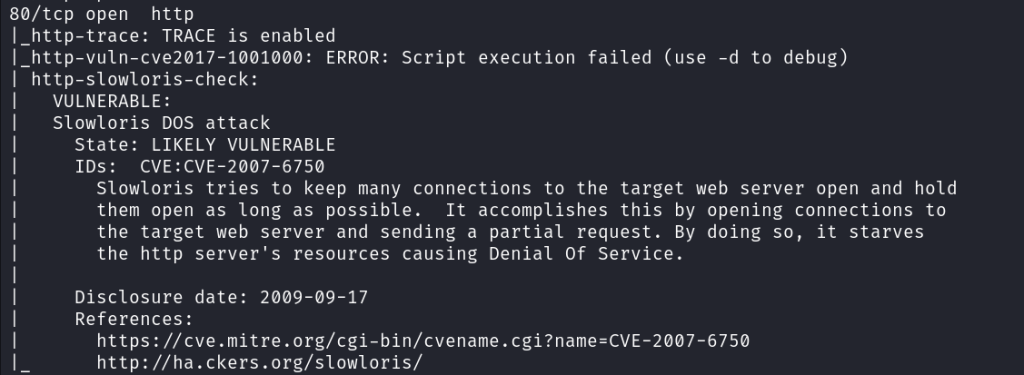
5. Insecure Remote Services (SSH, Telnet, RDP)
- Description: Remote services like SSH, Telnet, and RDP can be exploited if not properly secured.
- Common Risks: Attackers may gain unauthorized access to critical systems and data if these services are poorly configured.
Testing Methods:
- Service Exposure Testing: Identify exposed remote services using Nmap or Shodan to check for insecure configurations.
- Encryption Strength Analysis: Test for weak encryption algorithms in SSH configurations using tools like ssh-audit to ensure secure connections.
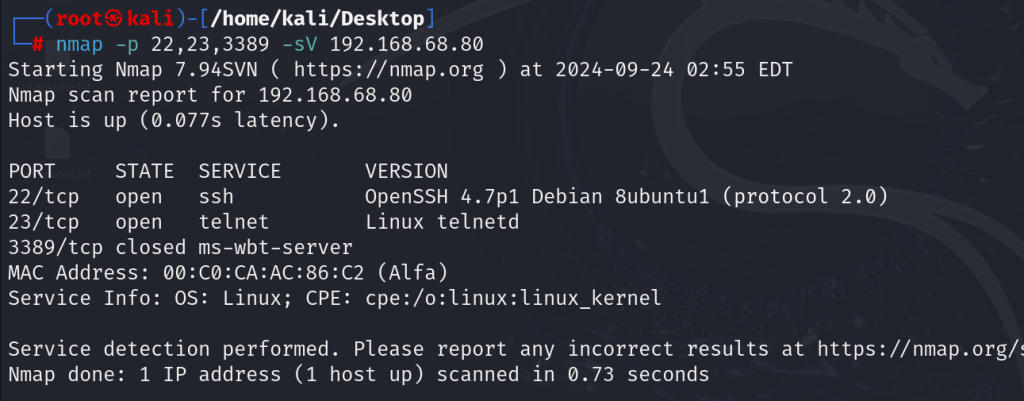
IMG 5: Graphic showing risks associated with insecure remote services.
6. Weak Encryption Protocols (SSL/TLS)
- Description: Weak or outdated encryption protocols can lead to data interception and exploitation.
- Common Risks: Attackers can exploit weak ciphers and SSL vulnerabilities (e.g., POODLE, Heartbleed) to decrypt sensitive information.
Testing Methods:
- SSL Scanning: Use tools such as SSLyze or testssl.sh to analyse SSL/TLS configurations and identify weak protocols or ciphers.
- Certificate Analysis: Review SSL certificates for validity, expiration, and strength of the encryption methods used.
7. Vulnerable Web Applications
- Description: Web applications are common targets for attackers due to vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and insecure APIs.
- Common Risks: Successful exploitation can lead to data breaches, unauthorized access, and significant reputational damage.
Testing Methods:
- Web Vulnerability Scanning: Utilize scanners like Burp Suite, OWASP ZAP, or Nikto to identify common vulnerabilities in web applications.
- Manual Testing: Perform manual testing to exploit vulnerabilities such as SQL injection using tools like SQLmap or testing for XSS through crafted payloads.
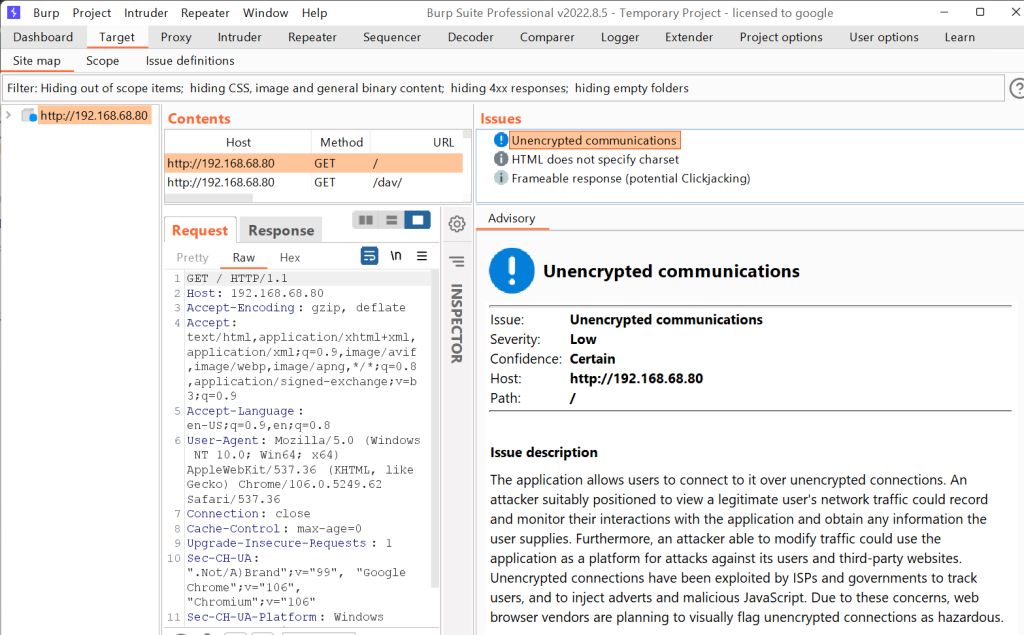
IMG 6: Infographic illustrating common web application vulnerabilities
8. SMB Vulnerabilities
- Description: Server Message Block (SMB) vulnerabilities can be exploited to gain unauthorized access to files and services.
- Common Risks: Known vulnerabilities, such as EternalBlue, can lead to remote code execution and extensive network access.
Testing Methods:
- Nmap SMB Scripts: Use Nmap with SMB-related scripts to check for vulnerabilities (nmap — script smb-vuln*).
- Metasploit Framework: Simulate known SMB attacks using Metasploit to assess the security of SMB configurations.
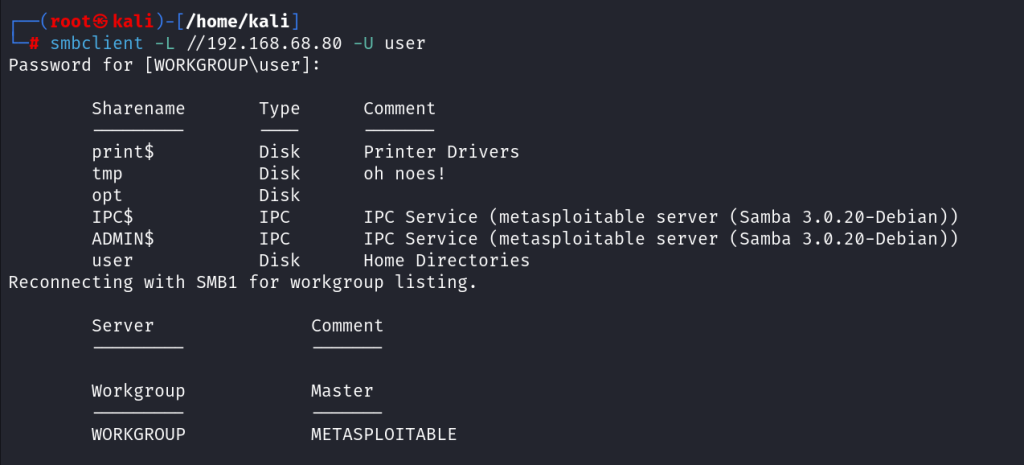
IMG 7: Diagram showing potential SMB vulnerabilities and their exploitation
9. Insecure SNMP Configurations
- Description: Simple Network Management Protocol (SNMP) is often misconfigured, leading to unauthorized access to network devices.
- Common Risks: Attackers can exploit default community strings or weak configurations to gather sensitive network information.
Testing Methods:
- SNMP Scanning: Use tools like Onesixtyone or snmpwalk to identify SNMP configurations and community strings.
- Security Assessment: Review SNMP configurations to ensure they utilize SNMPv3, which provides better security features.
10. Wireless Network Vulnerabilities
- Description: Wireless networks may have security weaknesses that can be exploited, such as weak encryption standards or rogue access points.
- Common Risks: Attackers can intercept sensitive information transmitted over unsecured Wi-Fi connections.
Testing Methods:
- Wi-Fi Auditing: Use tools like Aircrack-ng or Kismet to perform assessments on wireless security configurations.
- Rogue Access Point Detection: Identify unauthorized access points that may compromise network security.
11. ARP Spoofing or Poisoning
- Description: Address Resolution Protocol (ARP) spoofing can enable attackers to intercept network traffic and conduct Man-in-the-Middle (MitM) attacks.
- Common Risks: Sensitive data can be captured or altered as it travels across the network.
Testing Methods:
- ARP Poisoning Testing: Use tools like Ettercap or Bettercap to simulate ARP poisoning attacks.
- Network Traffic Analysis: Monitor network traffic using tools like Wireshark to detect ARP spoofing attempts.
12. Denial of Service (DoS) Vulnerabilities
- Description: DoS attacks aim to make a service unavailable by overwhelming it with traffic or exploiting vulnerabilities.
- Common Risks: Service disruptions can lead to downtime, financial losses, and reputational damage.
Testing Methods:
- DoS Simulation: Use tools like Hping3, LOIC, or Metasploit to simulate DoS attacks on critical services and assess their resilience.
- Rate Limiting Testing: Test the effectiveness of rate limiting and traffic shaping measures in place to prevent DoS attacks.
Special thanks
Dheeraj Prabhu K, Senior Security Analyst at CyberSapiens, for contributing his expertise to this content.
Conclusion
Network Vulnerability Assessment and Penetration Testing (VAPT) is a critical cybersecurity practice that helps organizations identify and mitigate vulnerabilities in their network infrastructure.
By systematically scanning for weaknesses, exploiting potential vulnerabilities, and analyzing the impact of successful attacks, VAPT provides valuable insights to strengthen security measures. Regular VAPT assessments, combined with robust security policies, employee training, and ongoing monitoring, are essential to protect networks from cyber threats and ensure the confidentiality, integrity, and availability of sensitive information.












