In today’s digitally driven world, businesses are increasingly reliant on technology to operate efficiently and effectively. However, with this dependence comes a significant risk of cyber threats, data breaches, and IT system vulnerabilities.
As a result, conducting regular IT security audits has become a crucial aspect of business protection.
In this article, we will delve into the purpose and importance of IT Security Audit: Purpose, Importance, and Why It is Crucial for Business Protection?
What is an IT Security Audit?
An IT security audit is a comprehensive evaluation of an organization’s IT systems, policies, and procedures to identify vulnerabilities, risks, and weaknesses that could compromise the security and integrity of its digital assets.
The audit assesses the effectiveness of existing security controls, identifies areas for improvement, and provides recommendations for mitigating potential risks.
Purpose of an IT Security Audit
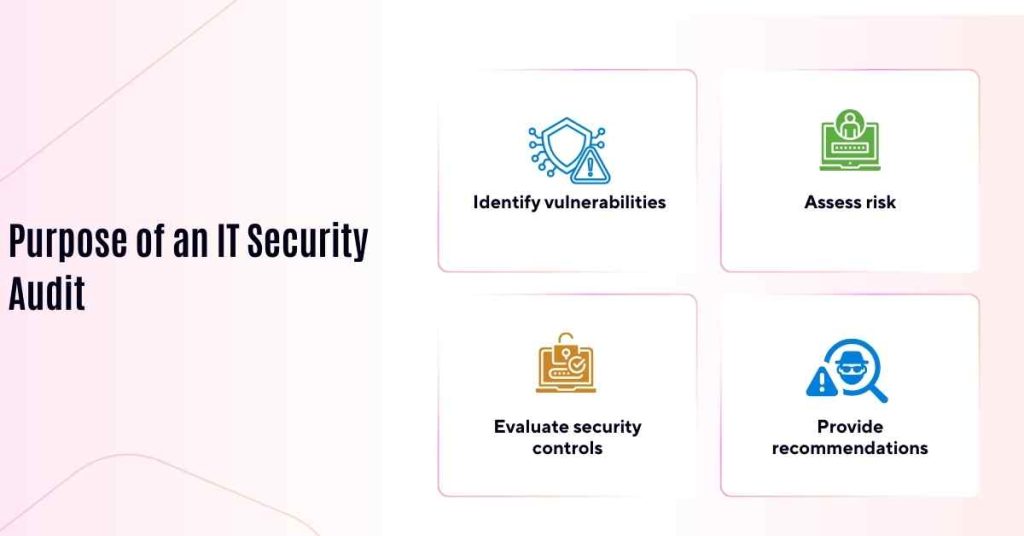
The primary purpose of an IT security audit is to ensure that an organization’s IT systems are secure, reliable, and compliant with relevant laws, regulations, and industry standards. The audit aims to:
1. Identify vulnerabilities
Suggest areas of risk, and threat or system, network and application-based security breaches.
2. Assess risk
Determine the chances and consequences of compromising including the security of information loss.
3. Evaluate security controls
Evaluate the effectiveness of existing measures against particular threats for instance firewalls, antivirus and access controls respectively.
4. Provide recommendations
Provide recommendations on how the security controls may be enhanced, how risk can be minimised and how the applicable legislation can be complied with.
Importance of IT Security Audits
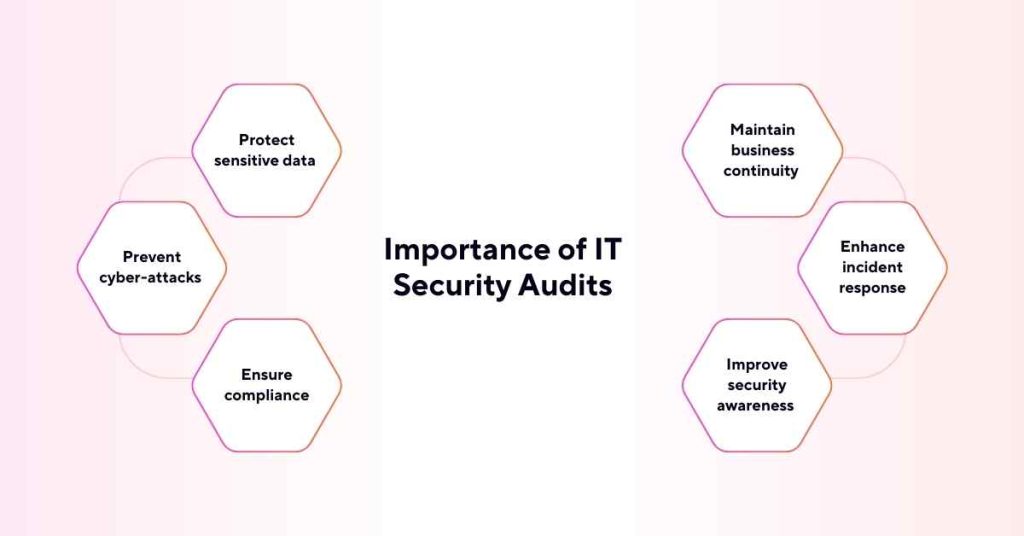
Conducting regular IT security audits is essential for businesses to:
1. Protect sensitive data
IT security audits enable one to discover weaknesses that threaten data confidentiality, integrity and availability, including customer details, customer and financial data or intellectual property.
2. Prevent cyber-attacks
Cyber threats are ever-increasing, and the outlining of the vulnerabilities and weaknesses will help organizations to be on the lookout and prevent future attacks on the systems.
3. Ensure compliance
Conducting IT security reviews minimizes legal noncompliance exposures that lead to fines or have adverse effects on brand image among organizations.
4. Maintain business continuity
This is important because IT security audits assist in proving that an organization’s IT systems will function optimally in the event of a security threat, thus reducing downtime and disruption of business.
5. Enhance incident response
Once an organization understands potential exposures, strategies can be designed or smoothed for addressing actualization possibilities of vulnerability or weakness to an incident response plan.
6. Improve security awareness
Security audits are a good way to present to the employees the most typical threats and the ways to protect them.
Why is IT Security Audit Crucial for Business Protection?
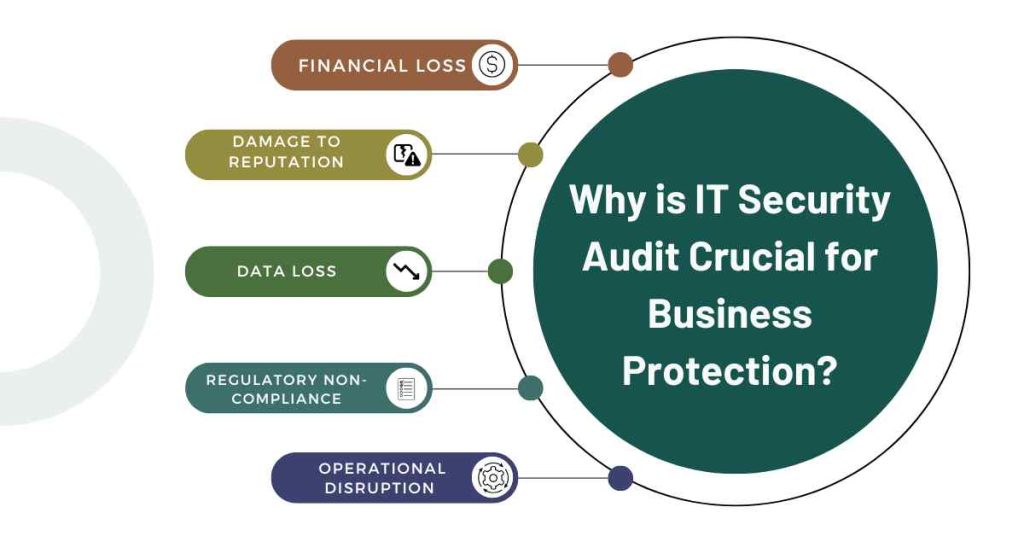
In today’s digital landscape, the consequences of a security breach can be severe and long-lasting. A single breach can lead to:
1. Financial loss
Claims for damages, fines imposed by the regulatory authorities and loss of business eliminate strong profits.
2. Damage to reputation
An imposed threat affects an organization’s image thus leading to low customer confidence and ensuing emulation.
3. Data loss
A security threat may lead to exposure of private information, most of which would seriously affect business functionality.
4. Regulatory non-compliance
If the laws and regulations affecting a company are not followed, the consequences are hefty fines, penalties and damage to reputation.
5. Operational disruption
Any security breach causes a business to shut down for a while hence affecting productivity and as well income.
Types of IT Security Audits

There are various types of IT security audits, including:
1. Network security audits
Define the firewall, routers, and switches and assess an organization’s network security.
2. Application security audits
Analyse general software protection and specific issues such as threats, risks and compliance.
3. Data security audits
Assess how data security is done effectively including where the sensitive data is stored, transmitted and accessed.
4. Compliance audits
Audit an organization for the applicable laws, rules, and regulations and the standards governing organizations in a particular economic sector.
Best Practices for Conducting an IT Security Audit
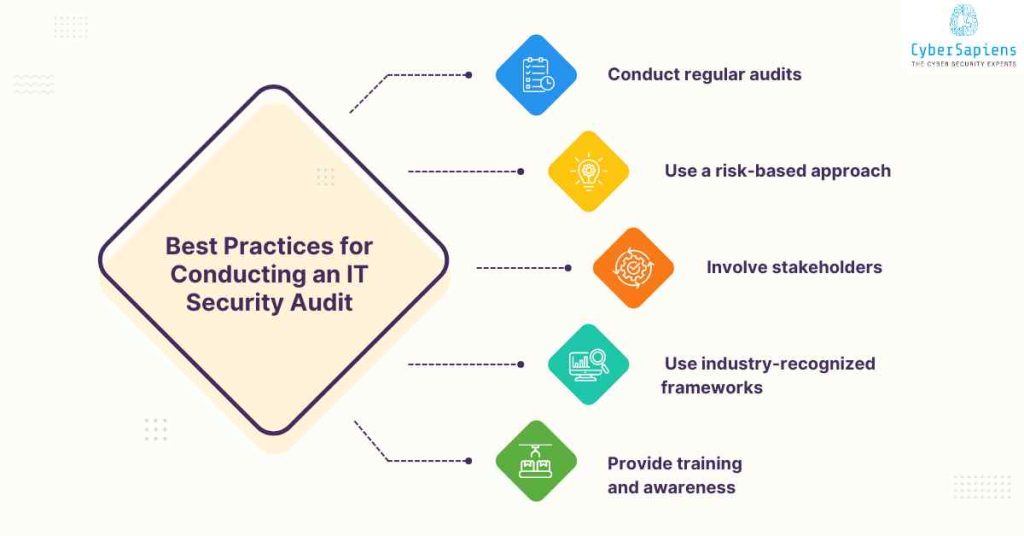
To ensure a comprehensive and effective IT security audit, organizations should:
1. Conduct regular audits
This means that frequent audits should be made to maintain security and correct compliance standards.
2. Use a risk-based approach
Focus the audit on those areas and assess the degree of risk.
3. Involve stakeholders
Include employees, management and other parties to have a more comprehensive audit expanded.
4. Use industry-recognized frameworks
Incorporate best practice frameworks from the industry where the audit process is to be implemented including NIST, ISO 27001and HIPAA.
5. Provide training and awareness
It is vital to ensure that awareness programs for employees are provided as well as training for how security should be maintained.
Conclusion
In conclusion, an IT security audit is a critical component of business protection, helping organizations identify vulnerabilities, assess risk, and evaluate security controls.
Regular audits are essential for ensuring compliance with relevant laws and regulations, protecting sensitive data, and preventing cyber-attacks.
By understanding the purpose, importance, and benefits of IT security audits, organizations can take proactive measures to safeguard their digital assets and maintain business continuity.
FAQs: IT Security Audit
1. What is the primary purpose of an IT security audit?
Anss: The primary purpose of an IT security audit is to assess the security and integrity of an organization’s IT systems, identify vulnerabilities and weaknesses, and evaluate the effectiveness of existing security controls.
2. Why are IT security audits important for businesses?
Ans: IT security audits are essential for businesses to protect sensitive data, prevent cyber-attacks, ensure compliance with relevant laws and regulations, maintain business continuity, and enhance incident response.
3. What areas of an organization’s IT systems are typically evaluated during an IT security audit?
Ans: An IT security audit typically evaluates an organization’s network infrastructure, software applications, data storage and transmission, access controls, and security policies and procedures.
4. Who should conduct an IT security audit?
Ans: An IT security audit can be conducted by an internal team or an external third-party auditor. However, it is recommended to use a combination of both internal and external auditors to ensure a comprehensive and unbiased audit.
5. How often should an IT security audit be conducted?
Ans: An IT security audit should be conducted regularly, ideally every 6-12 months, or as required by regulatory compliance.
6. What are the benefits of an IT security audit?
Ans: The benefits of an IT security audit include identifying vulnerabilities and weaknesses, reducing the risk of cyber-attacks, ensuring compliance with regulations, and improving incident response and business continuity.
7. What is the difference between an IT security audit and a vulnerability assessment?
Ans: An IT security audit is a comprehensive evaluation of an organization’s IT systems and security controls, while a vulnerability assessment is a specific examination of an organization’s IT systems to identify vulnerabilities and weaknesses.
8. What types of IT security audits are available?
Ans: There are various types of IT security audits, including network security audits, application security audits, data security audits, and compliance audits.
9. How long does an IT security audit typically take to complete?
Ans: The duration of an IT security audit can vary depending on the scope and complexity of the audit, but it typically takes several weeks to several months to complete.
10. What are the next steps after an IT security audit is completed?
Ans: After an IT security audit is completed, the next steps typically include implementing recommended security controls, addressing identified vulnerabilities and weaknesses, and conducting follow-up audits to ensure compliance and effectiveness of the implemented controls.












