In today’s digital age, businesses in Australia are increasingly relying on cloud computing to store, manage, and process their data. While cloud computing offers numerous benefits, such as scalability, flexibility, and cost-effectiveness, it also introduces new security risks.
Cloud Vulnerability Assessment and Penetration Testing (VAPT) also known as Cloud Security Testing a critical process that helps businesses identify and mitigate these risks.
In this article, we will explore the top 15 reasons why Cloud VAPT is important for companies in Australia.
List of Top 15 Reasons Why Cloud VAPT is Important for Businesses in Australia

Here is the list of the Top 15 Reasons Why Cloud VAPT is Important for Businesses in Australia:
1. Protection of Sensitive Data
Cloud VAPT helps businesses secure their valuable data from hacking, theft and other superior breaches.
The cloud structure assessment helps organisations anticipate the loopholes and risks that hackers can use to gain unauthorized access to business databases.
2. Compliance with Regulatory Requirements
In Australia, corporations are obligated to adhere to several rules and regulations, including the Australian Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme.
In particular, Cloud VAPT enables organisations to ensure compliance with these requirements because it highlights possible security threats.

3. Prevention of Financial Losses
Piracy, hacking and other instances of data violation can lead to a major impact on the company’s financial position.
Cloud VAPT works to stop such losses by discovering other vulnerabilities that might exist within the business that a hacker can exploit, thus minimising the chances of a breach.
4. Protection of Reputation
Any company’s reputation may be undermined, and customer trust may be reduced due to a cyber-attack or data breach.
Cloud VAPT enables organisations to safeguard their image since the potential risks are detected throughout the process making it difficult for an attacker to access the company’s network.
5. Identification of Vulnerabilities
Cloud VAPT provides organizations with a means of discovering risks inherent to cloud resources, such as misconfigured systems and misused credentials.
In this way, businesses notice these weaknesses and can work on them and avoid different cyber-attacks.
6. Improvement of Incident Response
Cloud VAPT aids the firms in strengthening their insights through strategising a course of action in case the envisaged security threats emerge.
This makes it easier for businesses to adequately respond to the calamity once it has been attacked by cybercriminals.
7. Compliance with Industry Standards
Cloud VAPT allows the business to meet requirements set by the PCI DSS and ISO 27001.
Through adherence to these standards, organizations can be in a position to show their concern for the secure and safe undertaking of their operations.
8. Protection of Intellectual Property
Cloud VAPT also shields the businesses’ proprietary information such as trade secrets, patents, and copyrights.
Preventing unauthorized access to information is important for businesses because it minimizes or eliminates susceptibilities to external threats.
9. Reduction of Risk
Cloud VAPT makes this possible because it effectively minimizes risk exposure for the business to potential security threats.
This makes it possible for businesses to predict their cloud infrastructure properly, and take necessary precautions where necessary.
10. Improvement of Security Posture
Cloud VAPT offers organizations an option to enhance the security of their business following the analysis of potential risks.
This makes it possible for business organisations to fortify their security measures and thus lower the rate of successful attacks.
11. Identification of Misconfigured Systems
Cloud VAPT assists organisations in discovering misconfigured systems such as firewalls, intrusion detection systems and access control. These are some of the misconfigurations that, by identifying them, businesses can take measures that will not allow hackers to attack them.
12. Detection of Malware
It is crucial because Cloud VAPT can identify malware as part of the overall solution, including viruses, Trojans, and ransomware.
Malware makes it easy for business companies to get rid of it and prevent other incursions in the future.
13. Protection of Customer Data
Cloud VAPT safeguards customer’s data in organizations such as PII and other customers’ sensitive financial data.
In other words, one can state that by knowing potential security threats and eliminating them, companies can protect their client’s information from illicit access.
14. Improvement of Cloud Security
Cloud VAPT avails security and vulnerability assessment of business entities’ cloud infrastructure with a view of eliminating threats to their cloud security.
This makes it easier for businesses to improve the cloud security controls in place and thus decreases the possibility of an attack being successful.
15. Cost Savings
Cyber-attacks and data breaches cost businesses a lot of money in terms of response and recovery from the attack and hence should be avoided.
Thus Cloud VAPT can benefit any business by minimizing the costs that the firm might incur as a result of a vulnerability in its system.
Top 5 Best Practices for Implementing Cloud VAPT
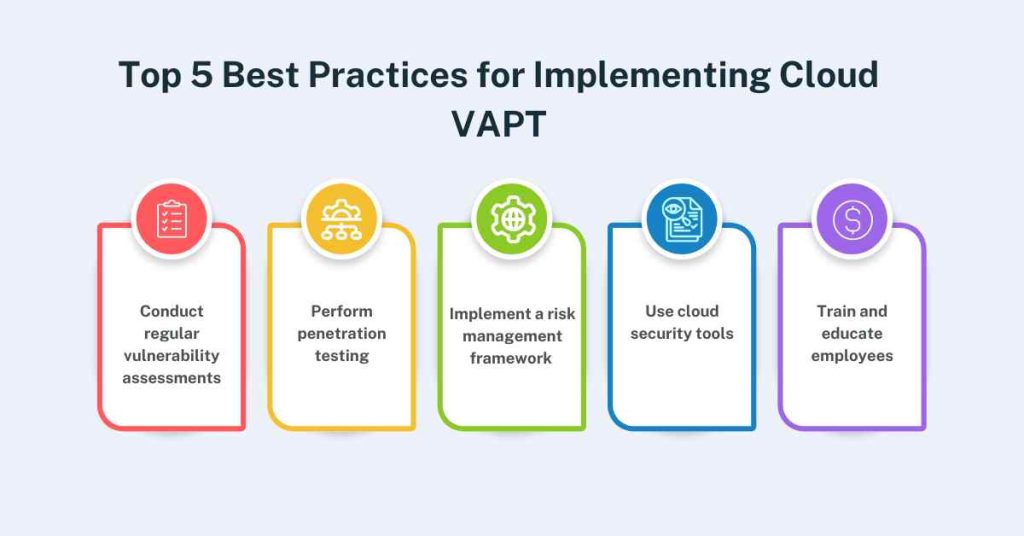
To implement Cloud VAPT effectively, businesses should follow these best practices:
1. Conduct regular vulnerability assessments
Vulnerability scanning performed from time to time assists organizations to discover any security loopholes that may exist in their cloud environment.
2. Perform penetration testing
For instance, penetration testing enables organizations to attempt real-life attacks and discover risks associated with their cloud environments.
3. Implement a risk management framework
A risk management framework is a process of addressing and minimizing security risks in a cloud environment for the business.
4. Use cloud security tools
Cloud security tools are a CSG and cloud access security Broker which assist a business enterprise in monitoring and securing a cloud environment.
5. Train and educate employees
Educating and training employees about cloud security also minimizes human error, making it harder for a hacker to breach the system.
Summary
Here is the summary of the blog titled “Top 15 Reasons Why Cloud VAPT is Important for Businesses in Australia“
- Protection of Sensitive Data
- Compliance with Regulatory Requirements
- Prevention of Financial Losses
- Protection of Reputation
- Identification of Vulnerabilities
- Improvement of Incident Response
- Compliance with Industry Standards
- Protection of Intellectual Property
- Reduction of Risk
- Improvement of Security Posture
- Identification of Misconfigured Systems
- Detection of Malware
- Protection of Customer Data
- Improvement of Cloud Security
- Cost Savings
Conclusion
Cloud VAPT is a critical process that helps businesses in Australia identify and mitigate potential security risks in their cloud infrastructure.
By protecting sensitive data, complying with regulatory requirements, and preventing financial losses, Cloud VAPT is an essential component of any business’s security strategy.
By incorporating Cloud VAPT into their security program, businesses can strengthen their security posture, reduce their risk exposure, and protect their reputation.
FAQs: Top 15 Reasons Why Cloud VAPT is Important for Businesses in Australia
1. What is Cloud VAPT?
Ans: Cloud VAPT (Vulnerability Assessment and Penetration Testing) is a process that helps businesses identify and mitigate potential security risks in their cloud infrastructure. It involves a combination of vulnerability assessments and penetration testing to identify weaknesses and vulnerabilities in the cloud infrastructure.
2. Why is Cloud VAPT important for businesses in Australia?
Ans: Cloud VAPT is important for businesses in Australia because it helps them protect their sensitive data, comply with regulatory requirements, and prevent financial losses. It also helps businesses improve their security posture, reduce their risk exposure, and protect their reputation.
3. What are the benefits of Cloud VAPT?
Ans: The benefits of Cloud VAPT include protection of sensitive data, compliance with regulatory requirements, prevention of financial losses, improvement of security posture, reduction of risk exposure, and protection of reputation.
4. How often should Cloud VAPT be performed?
Ans: Cloud VAPT should be performed regularly, ideally every 6-12 months, or whenever there are significant changes to the cloud infrastructure. This helps businesses stay on top of potential security risks and ensure their cloud infrastructure remains secure.
5. What is the difference between vulnerability assessment and penetration testing?
Ans: Vulnerability assessment is a process that identifies potential security risks and vulnerabilities in the cloud infrastructure, while penetration testing simulates real-world attacks to identify weaknesses and vulnerabilities. Both are essential components of Cloud VAPT.
6. Can Cloud VAPT be performed in-house or should it be outsourced?
Ans: Cloud VAPT can be performed in-house or outsourced, depending on the business’s resources and expertise. However, outsourcing Cloud VAPT to a reputable third-party provider can provide an objective and unbiased assessment of the cloud infrastructure.
7. What are the common types of vulnerabilities identified through Cloud VAPT?
Ans: Common types of vulnerabilities identified through Cloud VAPT include misconfigured systems, outdated software, weak passwords, unpatched vulnerabilities, and misconfigured access controls.
8. How can businesses implement Cloud VAPT effectively?
Ans: Businesses can implement Cloud VAPT effectively by conducting regular vulnerability assessments, performing penetration testing, implementing a risk management framework, using cloud security tools, and training and educating employees on cloud security best practices.
9. What are the common cloud security tools used in Cloud VAPT?
Ans: Common cloud security tools used in Cloud VAPT include cloud security gateways, cloud access security brokers, cloud security information and event management (SIEM) systems, and cloud vulnerability scanners.
10. How can businesses measure the effectiveness of Cloud VAPT?
Ans: Businesses can measure the effectiveness of Cloud VAPT by tracking the number of vulnerabilities identified and remediated, monitoring the reduction in risk exposure, evaluating the improvement in security posture, and assessing the return on investment (ROI) of Cloud VAPT.












