The IoT has revolutionized businesses, transforming traditional industries and creating new ones. From smart homes to industrial automation, IoT devices are omnipresent in the United Arab Emirates (UAE).
As the IoT ecosystem expands, it also introduces new risks and vulnerabilities.
In this article, we will explore the top 15 reasons why IoT device Vulnerability Assessment and Penetration Testing (VAPT) is crucial for businesses in the UAE.
List of Top 15 Reasons Why IoT Device VAPT is Important for Businesses in UAE

Here is the list of the Top 15 Reasons Why IoT Device VAPT is Important for Businesses in UAE:
1. Protecting Sensitive Data
IoT devices gather and forward massive information which may contain personal details, money-related data, and important business secrets.
If appropriate security is not followed then interception of this data can be readily accomplished by hackers.
VAPT for IoT devices enables people to find loopholes in devices to make sure that the data they contain are not easily accessed by unauthorized people.
2. Preventing Data Breaches
Peculiar events like data breaches are fatal to companies since they entail business reputational loss, financial loss, and action by the regulators.
By exposing IoT devices to tests that mimic real-world threats, VAPT enables businesses to address possible risks before unfavourable circumstances occur, such as data breaches.

3. Ensuring Compliance with UAE Regulations
At present, any member state of the UAE fulfils the requirements of certain rules and laws governing data and cyberspace.
IoT device VAPT assists with these regulations like the UAE Cybercrime Law and the EU General Data Protection Regulation (GDPR).
This way, businesses can check on certain devices to be sure they do not have any vulnerabilities or weak points that violate certain regulations.
4. Safeguarding Against Ransomware Attacks
Ransomware attacks are becoming an increased threat to businesses in the UAE.
VAPT of the IoT device indicates unlawful entry points of ransomware attacks in devices, which guide businesses in taking necessary precautions against future attacks.
5. Protecting Against DDoS Attacks
DDoS attacks can have severe impacts on an organisation’s operations, resulting in monetary losses and damage to the organisation’s reputation.
The VAPT for IoT devices enables business companies to know the gaps that need to be exploited by the DDoS attacks and work on it preventing the attacks from occurring.
6. Ensuring Business Continuity
This shows that IoT devices are business essential and disruptions catastrophic.
The VAPT of IoT devices enables a business to have proactive measures to prevent disruptions and hence keep the businesses running.
7. Reducing Financial Losses
This creates large losses since there are attacks and intrusions, that compromise companies’ cybersecurity.
IoT device VAPT enables businesses to minimize financial risks by using the assessment results to control attacks that exploit the main weaknesses and flaws of the connected devices.
8. Protecting Reputation
Cyber threats also present a threat to a business because the customers may not trust a business once their details have been leaked.
IoT device VAPT thereby covers the aspect of reputation by checking for vulnerabilities and weaknesses and taking the necessary steps against the devices.
9. Ensuring Conformity with International Standards
Trade and commerce massively take place in the UAE; thus, firms need to adhere to universally accepted norms and laws.
IoT Device VAPT assists organizations in keeping up with global best practices which include Iso 27001 and SOC 2.
10. Identifying Unknown Vulnerabilities
VAPT on IoT devices lets the unknown vulnerabilities on these devices be revealed which hackers might leverage.
Such vulnerabilities help one understand areas in business that need protection to reduce the likelihood of threats.
11. Protecting Against Insider Threats
In the UAE, insider threats remain one of the biggest threats that any organization is preparing to face.
IoT device vapt enables organizations to protect their networks against existing insider threats by identifying weaknesses in IoT devices that can allow such threats to happen.
12. Ensuring Secure Communication
IoT devices interact with each other and the cloud to deal with private data. IoT device VAPT gives businesses a sense of security by scanning for software issues and allowing them to block unauthorized access to devices.
13. Safeguarding Against Physical Attacks
It is also an avenue where IoT devices have weaknesses that are prone to physical attacks like the device layer and the eavesdropping layer.
IoT device VAPT therefore assists organizations to detect flaws that may be exploited by physical assaults on these devices to protect the companies against such capacities.
14. Ensuring Secure Deployment
IoT devices are often deployed in remote or hard-to-reach locations, making them vulnerable to unauthorized access.
IoT device VAPT helps ensure secure deployment by identifying vulnerabilities in devices, allowing businesses to take proactive measures to prevent unauthorized access.
15. Enhancing Customer Trust
IoT device VAPT helps enhance customer trust by demonstrating a commitment to security and data protection.
By identifying vulnerabilities and weaknesses in devices, businesses can take proactive measures to prevent attacks, ensuring that customer data is protected.
Top 5 Best Practices for IoT Device VAPT
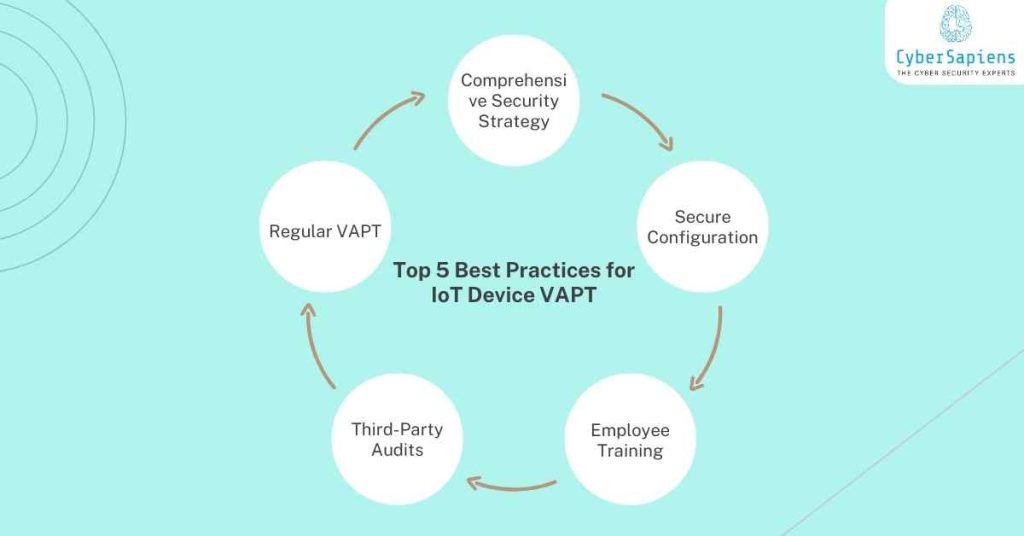
To ensure the effectiveness of IoT device VAPT, businesses should follow best practices, including:
1. Regular VAPT
It is recommended that VAPT should be conducted regularly to determine the gaps and openings in the existence of the devices.
2. Comprehensive Security Strategy
IoT device VAPT, threat intelligence, and incident response should in turn create a strong and general security plan.
3. Secure Configuration
Make sure that computer systems and networks that identify with IoT are secured and that the detecting and rectifying of security openings are up to date.
4. Employee Training
Teach employees through security tutorials for IoT and ensure that everyone understands their part of security and data protection.
5. Third-Party Audits
Consult cybersecurity professionals from a reliable provider to perform the IoT device VAPT and offer advice on cybersecurity measures and data protection.
Conclusion
IoT device VAPT is essential for businesses in the UAE, providing a proactive approach to security and data protection.
By identifying vulnerabilities and weaknesses in devices, businesses can take proactive measures to prevent attacks, ensure compliance with regulations, and protect sensitive data.
As the IoT ecosystem continues to expand, IoT device VAPT will become increasingly important for businesses in the UAE. By prioritizing IoT device VAPT, businesses can ensure a secure and resilient IoT ecosystem, ultimately driving growth and innovation.
Summary
Here is the summary for the bog title ” Top 15 Reasons Why IoT Device VAPT is Important for Businesses in UAE “.
- Protecting Sensitive Data
- Preventing Data Breaches
- Ensuring Compliance with UAE Regulations
- Safeguarding Against Ransomware Attacks
- Protecting Against DDoS Attacks
- Ensuring Business Continuity
- Reducing Financial Losses
- Protecting Reputation
- Ensuring Conformity with International Standards
- Identifying Unknown Vulnerabilities
- Protecting Against Insider Threats
- Ensuring Secure Communication
- Safeguarding Against Physical Attacks
- Ensuring Secure Deployment
- Enhancing Customer Trust
FAQs: Top 15 Reasons Why IoT Device VAPT is Important for Businesses in UAE
1. What is IoT Device VAPT?
Ans: IoT Device VAPT stands for Internet of Things (IoT) Device Vulnerability Assessment and Penetration Testing. It is a security testing process that identifies vulnerabilities and weaknesses in IoT devices, allowing businesses to take proactive measures to prevent attacks and ensure secure communication.
2. Why is IoT Device VAPT important?
Ans: IoT Device VAPT is important because it helps protect sensitive data from unauthorized access, prevents data breaches and other security incidents, and ensures compliance with regulations and international standards.
3. What are the benefits of IoT Device VAPT?
Ans: The benefits of IoT Device VAPT include identifying vulnerabilities and weaknesses in devices, preventing data breaches and other security incidents, ensuring compliance with regulations and international standards, and protecting reputation and customer trust.
4. How often should IoT Device VAPT be performed?
Ans: IoT Device VAPT should be performed regularly, ideally quarterly or bi-annually, depending on the device type and the business’s security requirements.
5. What types of devices are assessed during IoT Device VAPT?
Ans: IoT Device VAPT includes assessing a wide range of devices, such as smart home appliances, industrial automation systems, wearables, and other IoT devices.
6. What is the difference between Vulnerability Assessment and Penetration Testing?
Ans: Vulnerability Assessment identifies potential vulnerabilities and weaknesses in devices, while Penetration Testing simulates real-world attacks to test the device’s defences and identify potential entry points.
7. Is IoT Device VAPT a one-time process or an ongoing process?
Ans: IoT Device VAPT is an ongoing process that requires continuous monitoring and testing to identify new vulnerabilities and weaknesses in devices.
8. Can IoT Device VAPT be performed in-house or should it be outsourced?
Ans: IoT Device VAPT can be performed in-house by a team of experts or outsourced to a reputable cybersecurity provider. Outsourcing can be beneficial as it provides access to specialized skills and expertise.
9. What are the common vulnerabilities identified during IoT Device VAPT?
Ans: Common vulnerabilities identified during IoT Device VAPT include weak passwords, outdated software, insufficient encryption, and insecure communication protocols.
10. How can businesses ensure the effectiveness of IoT Device VAPT?
Ans: Businesses can ensure the effectiveness of IoT Device VAPT by implementing a comprehensive security strategy that includes regular VAPT, threat intelligence, and incident response, and by training employees on IoT security best practices and ensuring they understand the importance of security and data protection.












