Mobile applications are currently integrated into businesses in Australia due to technological advancements.
Due to the enhanced usage of smartphones in the market, companies are launching mobile applications to connect with customers and offer them improved interfaces.
However, the available opportunities for mobile applications have another side and they can be exposed to cyber enemies and hackers and, as a result, can suffer from cyber attacks and data leakage.
Mobile Application Vulnerability Assessment and Penetration Testing (VAPT), solves all these problems.
Mobile Application VAPT therefore involves appraisal and practical subjugation of a mobile application’s susceptibilities to enhance its security and prevent it from being prone to cyber-crashes.
In this article, we will discuss about “Top 15 Reasons Why Mobile Application VAPT is Important for Businesses in Australia”.
Understanding Mobile Application VAPT
But before going into the main topic let’s understand what Mobile Application VAPT is?
In essence, it is an extensive security procedure for evaluating the strengths and flaws of the application launched on mobile platforms.
This also entails automated auditing and penetrating testing to identify risks that may include; Insecure storage of data, Inadequate authentication, and injection of nasty code among others.
List of Top 15 Reasons Why Mobile Application VAPT is Important for Businesses in Australia

Here comes our main topic let’s delve into the List of Top 15 Reasons Why Mobile Applications VAPT are Important for Businesses in Australia:
1. Protection of Sensitive Data
Mobile applications contain user data, which sometimes can be considered confidential like credit card data, personal data, and login details.
VAPT assist in pinpointing various loopholes that a hacker may use to gain unauthorized access to the data which must be secure.
2. Prevention of Data Breaches
The impacts of data breaches for the companies are financial losses, harm to the public image and possible legal penalties.
organisations can avoid data leakages through the use of VAPT since any weaknesses that can be exploited by hackers are first exposed by the process.

3. Compliance with Regulations
Some types of regulations that are mandatory for Australian businesses include the Payment Card Industry Data Security Standard (PCI DSS) and Australian Privacy Principles (APPs).
By using VAPT, businesses are in a position to meet such regulations by ascertaining the level of security of business’s mobile applications.
4. Protection of Brand Reputation
Data loss is a major concern because it compromises the image of a firm as well as the trust of its clients.
VAPT also play a major role in identifying vulnerabilities of applications and securing the business’s reputation that its mobile applications are safe and capable of defending from different forms of attacks securely.
5. Identification of Vulnerabilities
VAPT requires the identification of threats that could be present in the mobile applications and the ones that are currently unknown or not exploited by black hats.
This aids a business in avoiding risks and guarantees that their applications are shielded.
6. Prioritization of Vulnerabilities
It assists corporations in categorizing risks relative to the risks’ consequentiality and their likelihood of being subjected to VAPT.
Such systems make sure the most severe threats are dramatically met first, thereby decreasing the likelihood of a security breach.
7. Improvement of Application Security
VAPT is used to enhance the protection of business mobile applications by not only scanning and resolving potential security issues but also adhering to the proper standards in coding and programming.
8. Reduction of Risk
This makes VAPT crucial in lowering the probability of experiencing security breaches since besides pointing out the weaknesses, measures to address the issues and prevent the attacks are also outlined.
9. Protection of Customer Trust
Business corresponds to their customer’s expectations in terms of privacy and guaranteeing that their mobile applications are free from threats.
Anyway, knowing that their applications are secured according to the standard set there by VAPT assists a business in regaining the trust of its customers.
10. Compliance with Industry Standards
It also enables businesses to conform to such standardized guidelines as the OWASP Mobile Security Framework which lays down the best practices for mobile applications security.
11. Identification of Zero-Day Vulnerabilities
VAPT works to discover zero-day vulnerability, that is a vulnerability that has not been recognized or exploited by cybercriminals.
This assists business organizations to be in a position to prevent future risks and guarantee the safety of their applications.
12. Protection of Business Assets
Mobile applications can be a good addition to the company’s tool kit as they allow the customer to interact with the brand and make a purchase.
VAPT also assists in safeguarding these resources by checking the system to find out whether it is capable of challenging different attacks.
13. Reduction of Costs
A security breach involves a loss of time and money in fixing the problem as well as the possibility of a legal suit or loss of clients’ trust.
VAPT is useful for these activities since it can minimize such expenditures by finding out areas with deficits that could be manipulated by hackers.
14. Improvement of Application Performance
Transcending this, the efficiency of the application can also be boosted to close earlier the various loopholes that may affect the performance of the mobile applications.
15. Protection of Business Continuity
That is why the violation of security can influence business sustainability, and it means lost time and potential losses.
This is regarding business continuity since VAPT assists in preventing loss through escrow via confirmation of the security and robustness of mobile applications to different types of attacks.
How to Conduct Mobile Application VAPT?
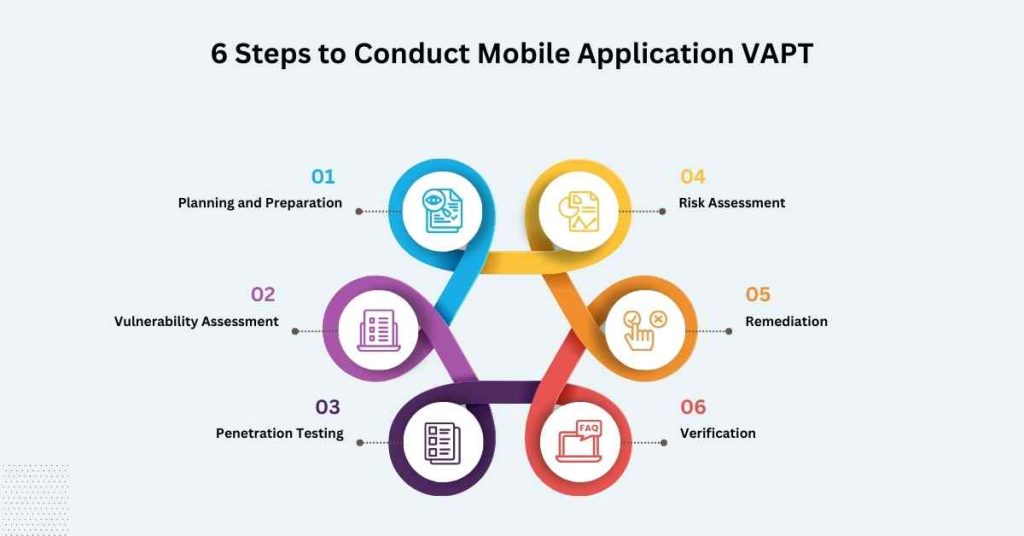
In the above section, you have read about the top 15 reasons for this section let’s see how to conduct Mobile Application VAPT :
1. Planning and Preparation
List down the application, network, and data that will be subjected to the VAPT.
2. Vulnerability Assessment
Find out weaknesses that may exist in the given application through tool-based security testing and manual testing.
3. Penetration Testing
Cybersecurity testing should be performed to enable the application to mimic actual cyber-attacks so that flaws can be distinguished.
4. Risk Assessment
Evaluate the threats related to the risks that were discovered and sort them according to their significance.
5. Remediation
Ensure that set changes for remediation and fix identified vulnerabilities are affected correctly.
6. Verification
It needs to confirm that ineffective remediations have been rectified and check that identified vulnerabilities have not been exploited.
6 Benefits of Conducting Mobile Application VAPT
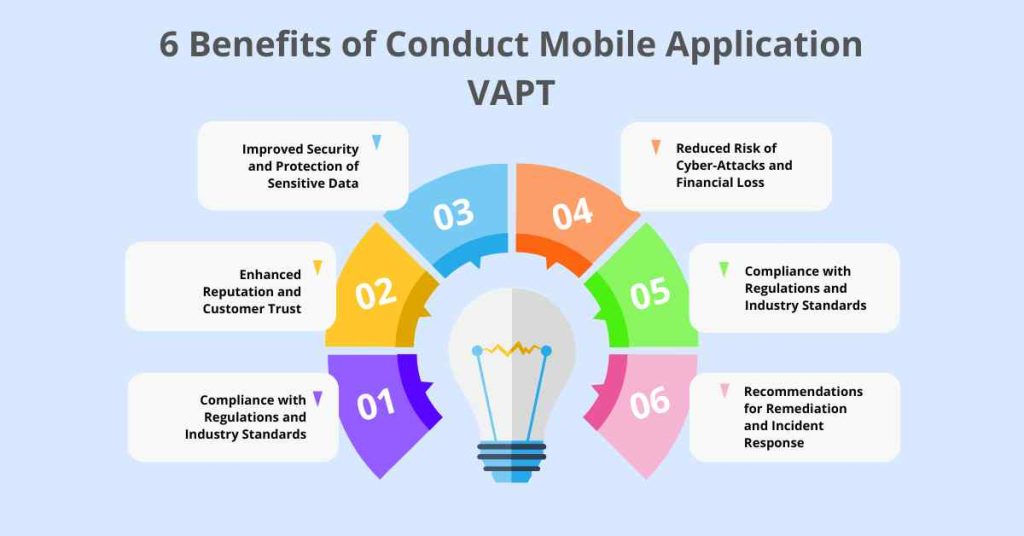
Do you know there are many benefits of conducting Mobile Application VAPT, Here are some:
1. Improved Security and Protection of Sensitive Data
Mobile application vulnerabilities are hereby identified and solved through VAPT to prevent unauthorized access to such information.
2. Enhanced Reputation and Customer Trust
Successful implementation of VAPT enables businesses in the following ways, The businesses can prove to the customers that they consider their security hence protecting the image and trust of the business among the customers.
3. Compliance with Regulations and Industry Standards
VAPT also helps businesses to ensure they meet regulatory and industrial requirements, including; requirements on the security of mobile applications.
4. Reduced Risk of Cyber-Attacks and Financial Loss
This is possible because VAPT helps in removing possible weaknesses that make the attacked organizations incur higher losses.
5. Identification and Prioritization of Vulnerabilities
VAPT is effective in assessing and ranking the risks so that it is easier to manage the important issues first.
6. Recommendations for Remediation and Incident Response
Because VAPT entails the identification of flaws and risks within an organization’s system, it offers suggestions concerning how they can be rectified and methods to be taken during and after a cyber-attack.
Summary
Here is the summary of the blog titled “Top 15 Reasons Why Mobile Application VAPT is Important for Businesses in Australia“
- Protection of Sensitive Data
- Prevention of Data Breaches
- Compliance with Regulations
- Protection of Brand Reputation
- Identification of Vulnerabilities
- Prioritization of Vulnerabilities
- Improvement of Application Security
- Reduction of Risk
- Protection of Customer Trust
- Compliance with Industry Standards
- Identification of Zero-Day Vulnerabilities
- Protection of Business Assets
- Reduction of Costs
- Improvement of Application Performance
- Protection of Business Continuity
Conclusion
Mobile Application VAPT is essential for businesses in Australia to ensure the security and integrity of their mobile applications. By conducting VAPT, businesses can identify and fix vulnerabilities, reduce the risk of cyber-attacks, and protect sensitive data.
Businesses need to prioritize VAPT and make it a part of their overall cybersecurity strategy.
FAQs: Top 15 Reasons Why Mobile Application VAPT is Important for Businesses in Australia
1. What is the Mobile Application VAPT?
Ans: Mobile Application VAPT (Vulnerability Assessment and Penetration Testing) is a process of identifying and exploiting vulnerabilities in mobile applications to ensure their security and integrity.
2. Why is the Mobile Application VAPT important?
Ans: Mobile Application VAPT is important because it helps to identify and fix vulnerabilities in mobile applications, reducing the risk of cyber-attacks and protecting sensitive data.
3. What are the benefits of conducting the Mobile Application VAPT?
Ans: The benefits of conducting Mobile Application VAPT include improved security and protection of sensitive data, enhanced reputation and customer trust, and reduced risk of cyber-attacks and financial loss.
4. How does the Mobile Application VAPT work?
Ans: Mobile Application VAPT involves automated and manual testing to identify vulnerabilities in mobile applications. The process includes vulnerability assessment, penetration testing, risk assessment, and remediation.
5. What types of vulnerabilities are identified during Mobile Application VAPT?
Ans: Mobile Application VAPT identifies various types of vulnerabilities, including SQL injection, cross-site scripting (XSS), and buffer overflow vulnerabilities.
6. How long does Mobile Application VAPT take?
Ans: The Mobile Application VAPT’s duration depends on the application’s complexity and the scope of the test. Typically, it can take anywhere from a few days to several weeks.
7. Do I need to have a physical device to conduct Mobile Application VAPT?
Ans: No, you don’t need to have a physical device to conduct Mobile Application VAPT. The test can be conducted on a virtual device or in a simulated environment.
8. Can I conduct Mobile Application VAPT on my own?
Ans: While it’s possible to conduct Mobile Application VAPT on your own, it’s recommended to hire a professional security testing company to ensure that the test is conducted thoroughly and effectively.
9. How often should I conduct Mobile Application VAPT?
Ans: It’s recommended to conduct Mobile Application VAPT regularly, ideally every 3-6 months, to ensure that your application remains secure and up-to-date.
10. What are the most common types of mobile application vulnerabilities?
Ans: The most common types of mobile application vulnerabilities include:
1. SQL injection
2. Cross-site scripting (XSS)
3. Buffer overflow
4. Authentication and authorization vulnerabilities
5. Data storage and encryption vulnerabilities












