APIs play an important role in today’s apps, making it easy for different systems to connect and work together smoothly. However, as their use grows, APIs have also become attractive targets for hackers.
Protecting your business means staying on top of potential vulnerabilities in your APIs.
This blog breaks down the top 5 API security risks and shows how API Vulnerability Assessment and Penetration Testing (VAPT) can help you address these threats effectively.
List of Top 5 API Vulnerabilities and How API VAPT Can Address Them

Here is the List of the Top 5 API Vulnerabilities and How API VAPT Can Address Them:
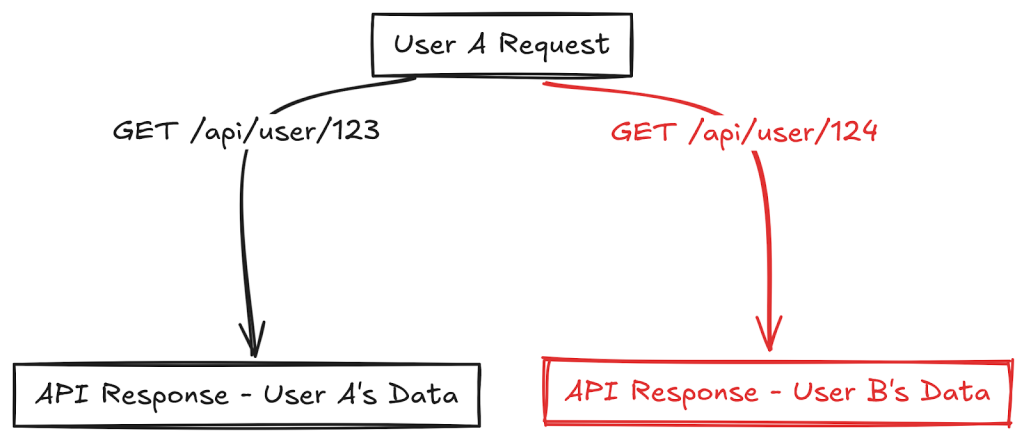
1. Broken Object Level Authorization (BOLA)
Broken Object Level Authorization, or BOLA, is a serious issue with APIs. It happens when an API doesn’t properly control access to specific pieces of data.
This means that if an attacker can figure out how to change object IDs (like user or item numbers), they might be able to view information they’re not supposed to see.
How API VAPT Addresses It?
API Vulnerability Assessment and Penetration Testing (VAPT) tackles BOLA by putting the API through a series of tests. Testers try to access data they shouldn’t be able to by messing with object IDs.
This simulates real attacks to uncover any weak spots in how the API manages access. When these vulnerabilities are found, VAPT helps fix them, ensuring that only the right people can access the right data and keeping sensitive information secure.
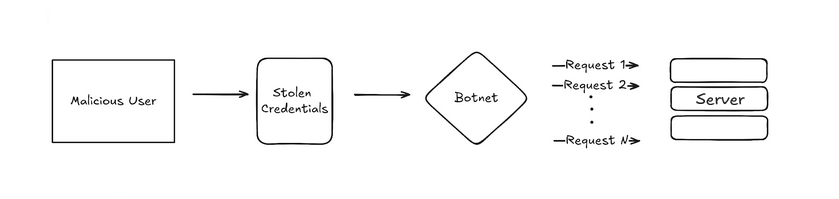
2. Broken Authentication
Broken Authentication is a major security flaw that happens when an API or application doesn’t handle user login and authentication properly. This can let attackers take over user accounts, gain unauthorized access, or even bypass security measures.
For example, if passwords are not stored securely or if there are weaknesses in the login process, it can be easier for hackers to guess or steal credentials.
How API VAPT Addresses It?
API Vulnerability Assessment and Penetration Testing (VAPT) tackles Broken Authentication by thoroughly testing how an API manages user logins and sessions. Testers will try to exploit weaknesses, like using weak or default passwords or trying to bypass authentication altogether.
By mimicking real-world attack techniques, VAPT identifies where authentication systems might be failing. Once these issues are found, VAPT helps to fix them, making sure that user accounts stay secure and that only legitimate users can access sensitive data.
3. Excessive Data Exposure
Excessive Data Exposure happens when an API or application shares more information than it should.
Imagine you’re only supposed to see your profile details, but the system shows you everyone’s data or unnecessary details that could be sensitive. This can lead to privacy breaches and data leaks, putting users at risk if too much information is accessible.

How API VAPT Addresses It?
API Vulnerability Assessment and Penetration Testing (VAPT) deals with Excessive Data Exposure by testing how much information an API reveals.
Testers will check if the API is giving away too much data, either accidentally or due to poor configuration. They might try different scenarios to see if they can access extra details, but they should not be able to.
Once they find these issues, VAPT helps data access controls, ensuring that only the necessary information is exposed and protecting user privacy.
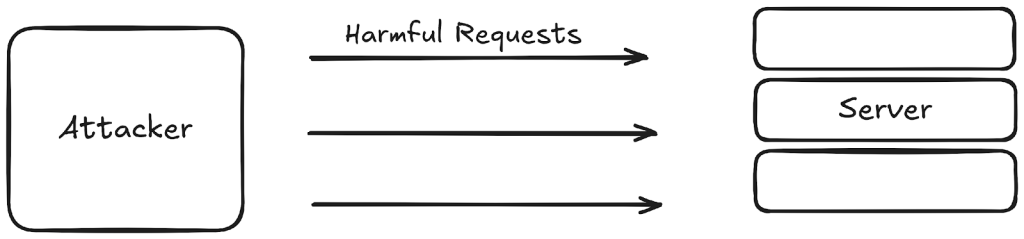
4. Lack of Rate Limiting
Lack of Rate Limiting is like leaving a gate open with no control over how many people can come through at once. When an API doesn’t limit how many requests a user or system can make in a short period, it can easily get overwhelmed.
This might slow things down, cause errors, or even crash the service entirely.
How API VAPT Addresses It?
To address this issue, API Vulnerability Assessment and Penetration Testing (VAPT) looks at how the API handles lots of requests at once. Testers will purposely send an excessive number of requests to see if the API can handle the load or if it starts to slow down or fail.
They also check to make sure there are rules in place to prevent anyone from overloading the system, such as limits on how often a user can make requests.
By identifying and fixing these potential problems, VAPT helps keep the API running smoothly, even when it’s under heavy use.
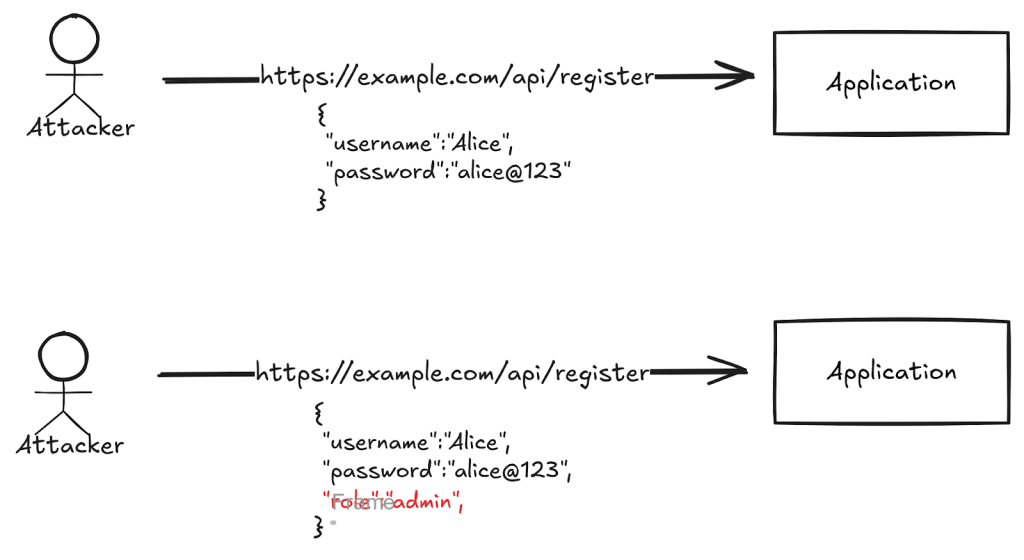
5. Mass Assignment
Mass assignment occurs when an API indiscriminately binds input from clients (like form data) to data models, allowing attackers to manipulate or update unintended fields.
If sensitive fields such as user roles or permissions are exposed in this way, attackers could potentially escalate privileges or make unauthorized changes.
How API VAPT Addresses It?
API VAPT identifies and tests for mass assignment vulnerabilities by attempting to inject unexpected or unauthorized parameters into API requests.
It ensures that only explicitly allowed and validated fields are processed by the API, preventing attackers from exploiting this flaw.
Testers also review input validation mechanisms to ensure that sensitive fields are adequately protected from unauthorized modifications.
Top 5 Best Practices for API Security
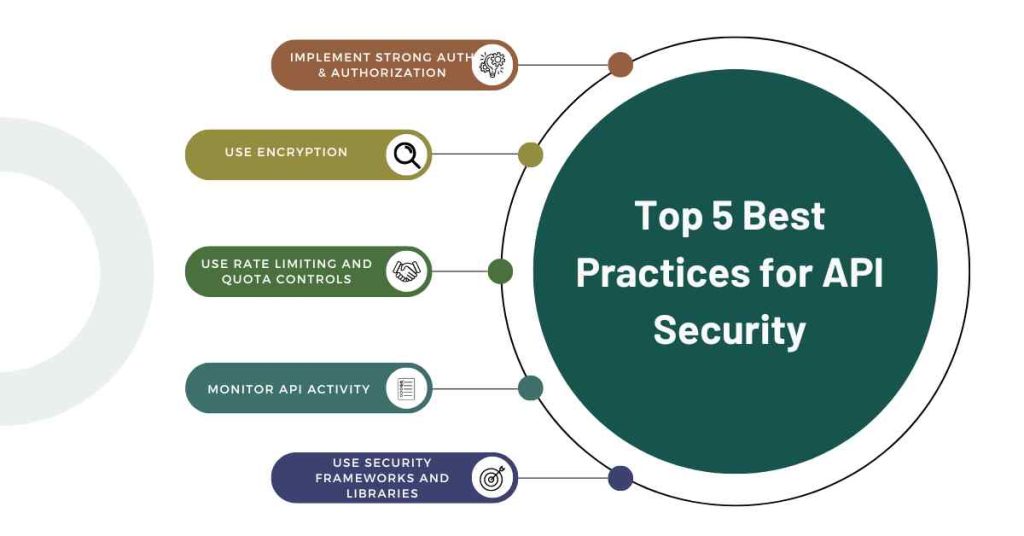
In addition to API VAPT, here are some best practices for API security:
1. Use Strong Authentication and Authorization Mechanisms
Implement strong authentication and authorization mechanisms to ensure only authorized access to the API.
2. Use Encryption
Encrypt sensitive data both in transit and at rest.
3. Use Rate Limiting and Quota Controls
Implement rate limiting and quota controls to prevent abuse and DDoS attacks.
4. Monitor API Activity
Monitor API activity to detect potential security issues.
5. Use Security Frameworks and Libraries
Use security frameworks and libraries to enhance API security.
Special thanks
Fakruddin Rahif, Senior Security Analyst at CyberSapiens, for contributing his expertise to this content.
Conclusion
APIs are incredibly useful, giving us powerful features and integrations. But they can also bring about serious security risks if not handled properly.
That’s why it’s so important to tackle these vulnerabilities with a solid API Vulnerability Assessment and Penetration Testing (VAPT) strategy.
At CyberSapiens, we’re experts in running thorough API VAPT assessments.
We help find and fix security issues before they can be exploited. Keep your business safe and your APIs secure. Reach out to us today to find out more about how our API VAPT services can help you.
FAQs: Top 5 API Vulnerabilities and How API VAPT Can Address Them
1. What is API VAPT, and why is it important?
Ans: API VAPT (Vulnerability Assessment and Penetration Testing) is a security testing process designed to identify and address vulnerabilities in APIs. It is essential to ensure the security and integrity of your APIs, protecting sensitive data and preventing security incidents.
2. What are the top API vulnerabilities that I should be concerned about?
Ans: The top API vulnerabilities you should be concerned about include injection vulnerabilities, broken object-level authorisation (BOLA), security misconfiguration, excessive data exposure, and lack of rate limiting. These vulnerabilities can be exploited by attackers to access sensitive data, disrupt critical operations, or cause reputational damage.
3. How often should I perform API VAPT on my APIs?
Ans: It is recommended to perform API VAPT regularly, such as quarterly or bi-annually, to stay on top of evolving security threats and vulnerabilities. This frequency allows you to identify and address vulnerabilities before they can be exploited by attackers.
4. What is the difference between automated and manual API VAPT testing?
Ans: Automated API VAPT testing uses automated tools to identify vulnerabilities, while manual testing involves human testers simulating real-world attacks to validate findings and identify complex vulnerabilities. Both methods are essential for comprehensive API security testing.
5. Can I use API VAPT to comply with regulatory requirements?
Ans: Yes, API VAPT can help you comply with regulatory requirements and industry standards, such as PCI-DSS, HIPAA, and GDPR. Regular API VAPT exercises can demonstrate your organization’s commitment to security and compliance.
6. How do I prioritize remediation efforts for identified vulnerabilities?
Ans: Prioritize remediation efforts based on the severity and potential impact of the vulnerability. Address high-risk vulnerabilities first, and ensure that remediation efforts are comprehensive and effective.
7. What are the benefits of involving development teams in API VAPT efforts?
Ans: Involving development teams in API VAPT efforts can ensure that vulnerabilities are addressed promptly and effectively. Development teams can provide valuable insights into the API design and functionality, making it easier to identify and address vulnerabilities.
8. Can I use API VAPT to improve my organization’s security posture?
Ans: Yes, API VAPT can help improve your organization’s security posture by identifying vulnerabilities and weaknesses in APIs. By addressing these vulnerabilities, you can reduce the risk of security incidents and reputational damage.
9. How long does an API VAPT exercise typically take?
Ans: The duration of an API VAPT exercise can vary depending on the complexity of the API, the number of APIs being tested, and the scope of the exercise. Typical API VAPT exercises can take anywhere from a few days to several weeks.
10. Can I perform API VAPT in-house, or do I need to outsource it to a third-party provider?
Ans: You can perform API VAPT in-house, but it’s recommended to outsource it to a third-party provider who has the necessary expertise and experience in API security testing. Third-party providers can provide independent and unbiased testing, ensuring that your APIs are thoroughly tested and vulnerabilities are identified and addressed.












