This is very, very important for understanding that now with the help of Artificial intelligence (AI) and Machine learning (ML), many things in the cyber security space have changed.
Among the most interesting innovations in this domain, one should mention the emergence of the new conversational AI model ChatGPT that can take input in the form of a message and process it in an almost human-like manner.
Although ChatGPT mainly aims to synthesize text, it can be used for cybersecurity tasks such as vulnerability identification and bug finding. Specifically, this article aims to demonstrate How to use ChatGPT for Cyber Security and how to find vulnerabilities or bugs using ChatGPT.
What is ChatGPT?
Before moving further let’s understand what ChatGPT is.
ChatGPT is a conversational AI model developed by OpenAI, a research organization focused on developing and promoting friendly AI. It is a variant of the GPT (Generative Pre-trained Transformer) model, which is a type of neural network designed to process and generate human-like text. It is trained on a massive dataset of text from the internet and can understand and respond to a wide range of questions and prompts.
How to use ChatGPT for Cyber Security?
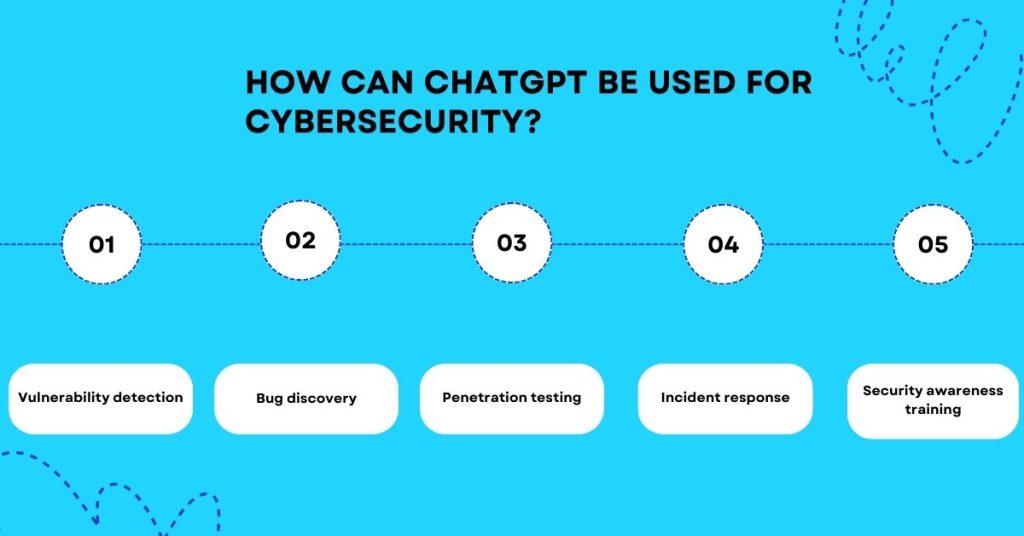
ChatGPT can be used for various cybersecurity applications, including:
1. Vulnerability detection
ChatGPT can be used to detect weak points in the software code since potential threats and risks can be detected about the peculiarities of the code.
2. Bug discovery
ChatGPT can find and report bugs in the code since it can analyze the code and find any possible issues in it.
3. Penetration testing
ChatGPT can be exploited to replicate different scenarios of penetration testing and thus the security teams can assess their readiness levels to handle potential threats.
4. Incident response
The function enabled is to gain insights and the recommendation given by using ChatGPT in analyzing incident response data in the case of security incidents.
5. Security awareness training
ChatGPT can be applied to engage the users in elaborate security-awareness training that describes conditions similar to real situations and gives a response to the user’s action.
Can we find vulnerabilities or bugs using ChatGPT?
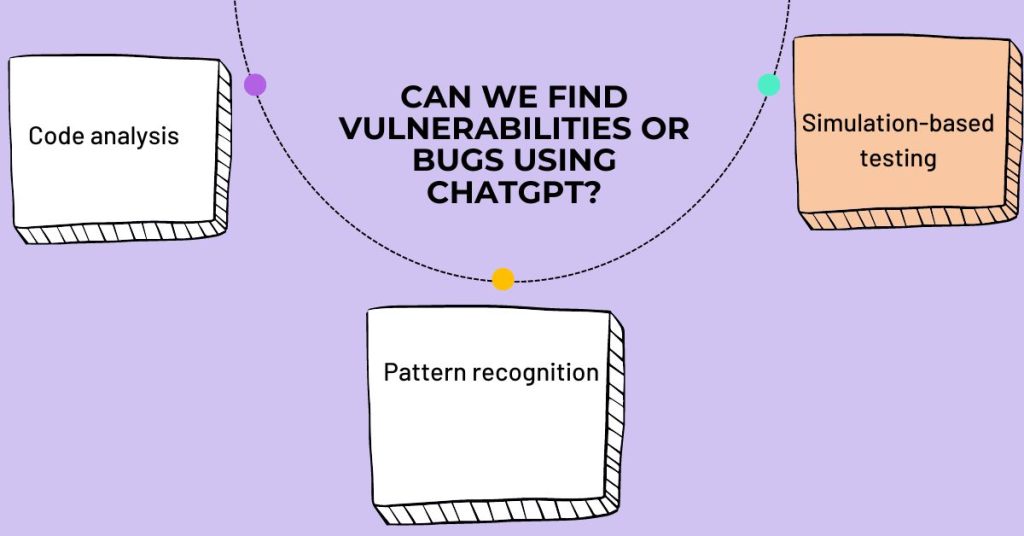
Yes, ChatGPT can be used to identify potential vulnerabilities and bugs in software code. Here are a few ways to use ChatGPT for vulnerability detection and bug discovery:
1. Code analysis
ChatGPT can be used to analyze software code and identify potential vulnerabilities or bugs. For example, you can provide ChatGPT with a piece of code and ask it to identify potential vulnerabilities or bugs.
2. Pattern recognition
ChatGPT can be used to detect the factors that characterize the code and that may lead to a vulnerability or bug in the system. For instance, one can input a set of code
snippets to ChatGPT and request it to find typical, or, on the contrary, atypical, patterns.
3. Simulation-based testing
ChatGPT can be used in realistic interactions, testing the software code for potential vulnerabilities or bugs. For instance, you can submit a piece of code to ChatGPT and request it to generate a demonstration of a certain form of attack.
Limitations of using ChatGPT for Cyber Security
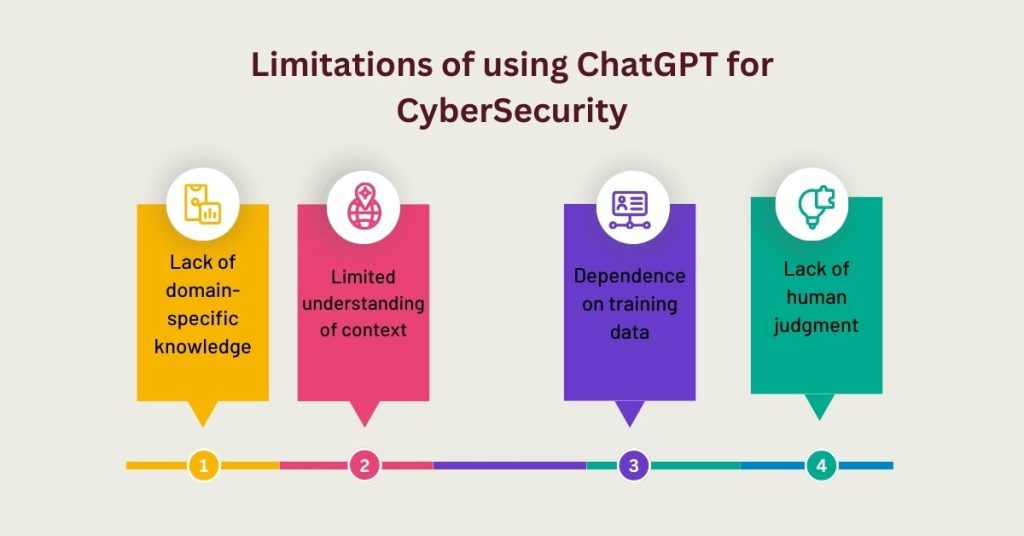
While ChatGPT has the potential to be a valuable tool for cybersecurity, there are several limitations to consider:
1. Lack of domain-specific knowledge
ChatGPT is a generalist model for the conversation, so it might not be as specific in cybersecurity as a human with that specialist background.
2. Limited understanding of context
ChatGPT in general may not capture the context that is associated with a particular piece of code or a particular script which sometimes may lead to a false positive or false negative case.
3. Dependence on training data
Unfortunately, conversing with ChatGPT reveals that it is only as good as the data it learned from, which is based on machine learning. Before using it, ChatGPT must be trained using some data, and, if the training data set is poor or not representative, then ChatGPT would also be equally useless in searching for those vulnerabilities or bugs.
4. Lack of human judgment
Being a machine learning model, ChatGPT has no decision-making capacity of its own but operates on other people’s decisions. While it can often identify, for example, a weak link or a bug it can fail to look for or investigate like a human cybersecurity analyst.
Best practices for using ChatGPT for Cyber Security
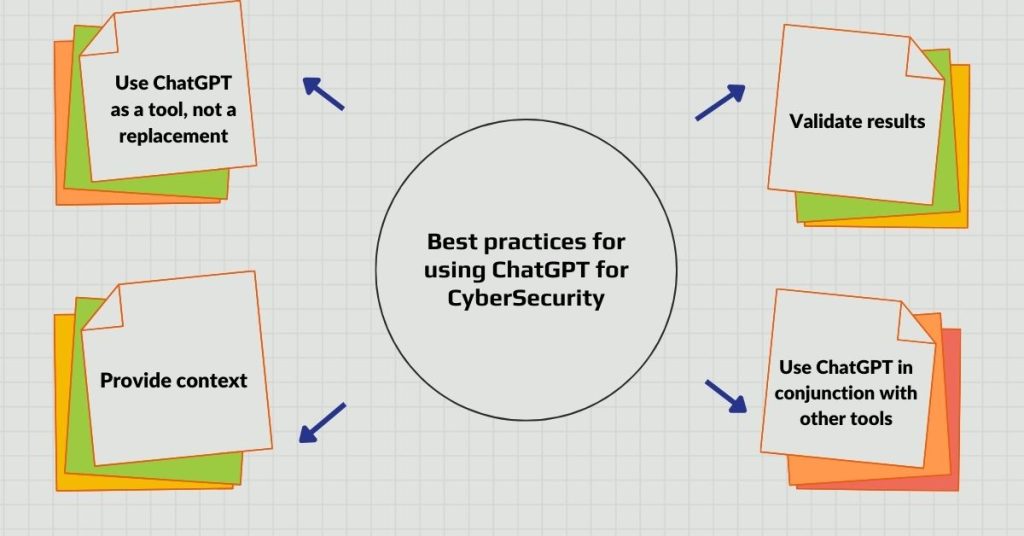
To get the most out of ChatGPT for cybersecurity, follow these best practices:
1. Use ChatGPT as a tool, not a replacement
ChatGPT should be used as a tool to augment human cybersecurity expertise, not replace it.
2. Provide context
Provide ChatGPT with as much context as possible when asking it to analyze code or simulate scenarios.
3. Validate results
Validate the results of ChatGPT’s analysis or simulation to ensure accuracy and relevance.
4. Use ChatGPT in conjunction with other tools
Use ChatGPT in conjunction with other cybersecurity tools and techniques to get a more comprehensive view of potential vulnerabilities or bugs.
Real-world examples of using ChatGPT for Cyber Security
Here are a few real-world examples of using ChatGPT for Cyber Security:
1. Vulnerability detection
A security researcher used ChatGPT to analyze a piece of code and identify a potential vulnerability. The researcher then validated the result using other tools and techniques and reported the vulnerability to the software vendor.
2. Bug discovery
A developer used ChatGPT to analyze a piece of code and identify a potential bug. The developer then fixed the bug and tested the code to ensure it was working correctly.
3. Penetration testing
A security team used ChatGPT to simulate a penetration testing scenario and identify potential vulnerabilities in a web application. The team then used the results to inform their penetration testing efforts.
10 Best Prompts that Cyber Security Specialists can use to find Vulnerabilities

Here are the 10 best prompts that cybersecurity specialists can use to find vulnerabilities with their uses
– Prompt 1
Explain the most common types of vulnerabilities found in web applications and how they can be exploited. Provide examples and mitigation strategies.
Use: Helps specialists understand different vulnerabilities and their implications.
– Prompt 2
Describe how SQL injection attacks work and what coding practices can be implemented to prevent them. Can you provide examples of SQL injection vulnerabilities in PHP or JavaScript?
Use: Offers insights into preventing SQL injection, a common web vulnerability.
– Prompt 3
What is Cross-Site Scripting (XSS), and how can it be detected in a web application? Suggest methods to mitigate XSS vulnerabilities.
Use: Provides information on detecting and mitigating XSS vulnerabilities.
– Prompt 4
Explain what a buffer overflow attack is and how it can be identified in C or C++ code. What are the best practices to avoid such vulnerabilities?
Use: Useful for identifying and preventing buffer overflow attacks in software.
– Prompt 5
What are some common security misconfigurations in server environments, and how can they be prevented? Provide a checklist for securing server configurations.
Use: Assists in identifying and fixing security misconfigurations in server setups.
– Prompt 6
Describe common access control vulnerabilities in web applications. How can role-based access control (RBAC) be implemented to minimize these risks?
Use: Helps in understanding access control vulnerabilities and implementing RBAC.
– Prompt 7
What are the OWASP Top 10 security risks, and how can developers mitigate these risks in web applications? Provide practical examples for each.
Use: Guides specialists through the OWASP Top 10 and mitigation strategies.
– Prompt 8
How can automated tools be used to identify security vulnerabilities in software development? Suggest some tools and explain their strengths and limitations.
Use: Helps in selecting and using automated tools for security testing.
– Prompt 9
Discuss the best practices for password security and authentication mechanisms to protect against vulnerabilities such as brute force attacks and credential stuffing.
Use: Offers advice on securing authentication mechanisms and passwords.
– Prompt 10
Outline the steps in a vulnerability management lifecycle. How can an organization effectively prioritize and remediate discovered vulnerabilities?
Use: Provides a roadmap for managing and addressing vulnerabilities systematically.
Conclusion
The ChatGPT can be effectively used in the aspect of cybersecurity as a tool for vulnerability identification as well as bug search.
However, it cannot be said that ChatGPT can be leveraged to go over a code base and pinpoint potential vulnerabilities or bugs directly, but it can be utilized in conjunction with other tools and methodologies in which one would obtain a broad view of possible problems that may arise.
While leveraging the described approaches and using ChatGPT as the assistant of human specialists in cybersecurity, it is possible to enhance organizational cybersecurity and limit security threats.
FAQs: How to use ChatGPT for CyberSecurity | Can we find vulnerabilities or bugs using ChatGPT?
1. What are the biggest advantages of using ChatGPT for cybersecurity?
Ans: ChatGPT can help identify potential vulnerabilities and bugs in code, simulate real-world attack scenarios, and analyze large amounts of security data. It can also help with understanding and researching complex security concepts.
2. What are the main limitations of using ChatGPT for cybersecurity?
Ans: ChatGPT lacks real-world experience, human judgment, and context. It can be biased by its training data, and its output should always be validated by human experts.
3. Can ChatGPT replace human cybersecurity professionals?
Ans: No, ChatGPT is a tool that can augment human expertise but cannot replace it. Human cybersecurity professionals are essential for critical thinking, decision-making, and ethical considerations.
4. How can I effectively use ChatGPT for code analysis?
Ans: Provide clear and specific instructions, including the code snippet and the type of vulnerability you’re looking for. Validate the results with additional tools and human expertise.
5. Can ChatGPT be used for penetration testing?
Ans: Yes, ChatGPT can be used to simulate attack scenarios and identify potential vulnerabilities. However, it’s important to use it alongside other penetration testing tools and techniques.
6. Is ChatGPT suitable for analyzing security logs and incident reports?
Ans: Yes, ChatGPT can be used to analyze large amounts of security data, identify patterns, and extract relevant information. But it’s vital to have human experts review and interpret the results.
7. How can I ensure that ChatGPT is using accurate information?
Ans: It’s crucial to use ChatGPT with up-to-date security knowledge and to be aware of its limitations. Always validate its information with reliable security resources.
8. Can ChatGPT be used for phishing detection?
Ans: Yes, ChatGPT can be used to identify phishing emails by analyzing their content and patterns. It can also be used to create realistic phishing simulations for training purposes.
9. Is ChatGPT secure to use for cybersecurity purposes?
Ans: While ChatGPT itself is a language model, it’s crucial to use it securely. Avoid sharing sensitive information with it and always use it on secure platforms.
10. What are the future possibilities for using ChatGPT in cybersecurity?
Ans: ChatGPT can be integrated with other AI and ML models, trained on specific security datasets, and used for human-AI collaboration, leading to even more advanced cybersecurity solutions.












