In today’s interconnected world, authentication is a key pillar of security. From logging into websites to accessing remote servers, authentication ensures that only the right people have access to resources. However, there are cases where users can connect without entering any credentials — this is called anonymous authentication. While it’s convenient in certain scenarios, it can also open up systems to serious vulnerabilities.
In this blog, we’ll break down the practical testing guide for anonymous authentication, why it matters, and how you can test it. By understanding and testing these vulnerabilities, you’ll gain insights into how they can be exploited and how to protect against them.
What Is Anonymous Authentication?

Anonymous authentication allows users to access services or resources without providing credentials like usernames or passwords. It’s like having a guest account that anyone can use — no identification needed. This type of authentication is often used in:
- Public Services: Where user identity doesn’t matter, such as open Wi-Fi networks or public FTP servers.
- Legacy Systems: Older systems where authentication wasn’t a priority or modern security practices hadn’t been adopted yet.
- Ease of Access: Where the focus is more on convenience rather than security, like publicly available content or files on a server.
While it serves a purpose, anonymous authentication can be risky. Anyone can access resources, including unauthorized users who might exploit this maliciously. To ensure security, it’s essential to test anonymous access to verify that sensitive data or services aren’t exposed unnecessarily.
Testing Anonymous Authentication
Below, we’ll walk through some services on Metasploitable2 and demonstrate how you can test for anonymous authentication.
FTP (File Transfer Protocol) Port: 21
Step 1:
1. Connect to FTP Service:
Use an FTP client or command-line tool to connect to the FTP server:
ftp <target-ip>When prompted for login credentials, use anonymous as the username, leave the password blank, or use a generic password like password.
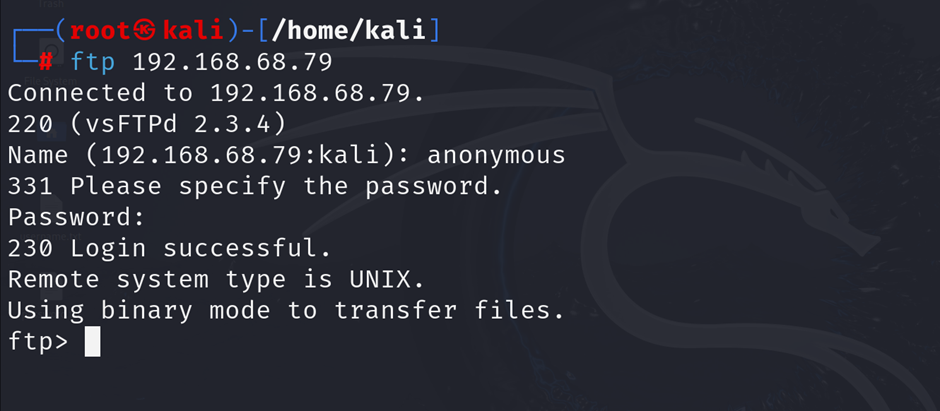
Alt text: FTP client connecting to an FTP server on Metasploitable2 using anonymous credentials.
- Check for Vulnerabilities:
Look for sensitive files or directories that are accessible without proper authentication.
SMB (Server Message Block) Port: 445
Steps:
- Enumerate SMB Shares:
Use smbclient to list available shares and test for anonymous access:
smbclient -L <target-ip> -U ""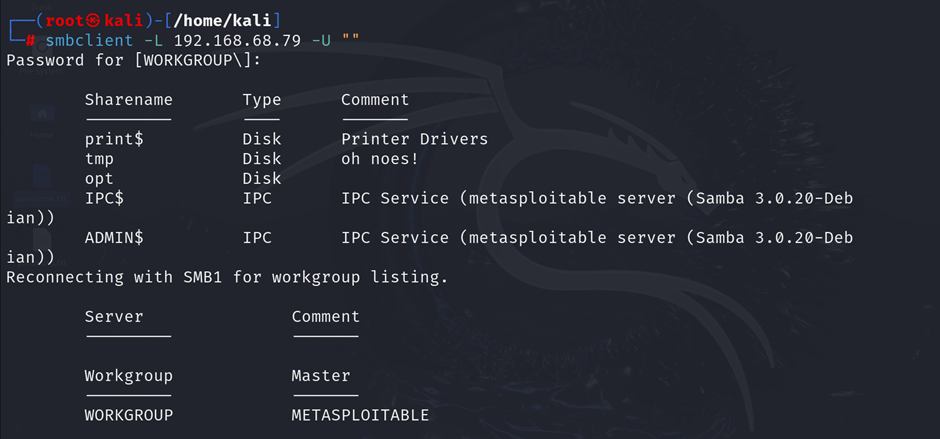
Alt text: Enumeration of SMB shares on Metasploitable2, showing accessible directories with anonymous login.
- Access Shares:
If anonymous shares are available, connect and browse the contents:
smbclient //target-ip/share -U ""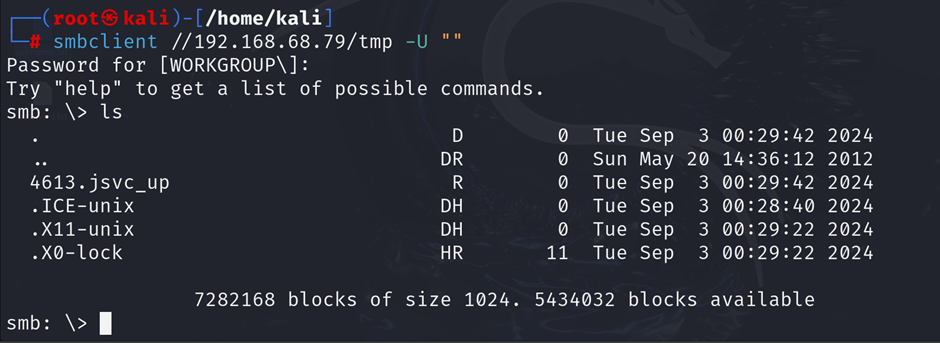
Alt text: SMB client accessing a shared directory on Metasploitable2 using anonymous authentication.
- Check for Sensitive Information:
Explore accessible files and directories for any sensitive or critical data that shouldn’t be publicly available.
SSH (Secure Shell) Port: 22
Steps:
Attempt Login:
SSH typically requires credentials, but you can try connecting with common usernames and passwords:
ssh user@<target-ip> 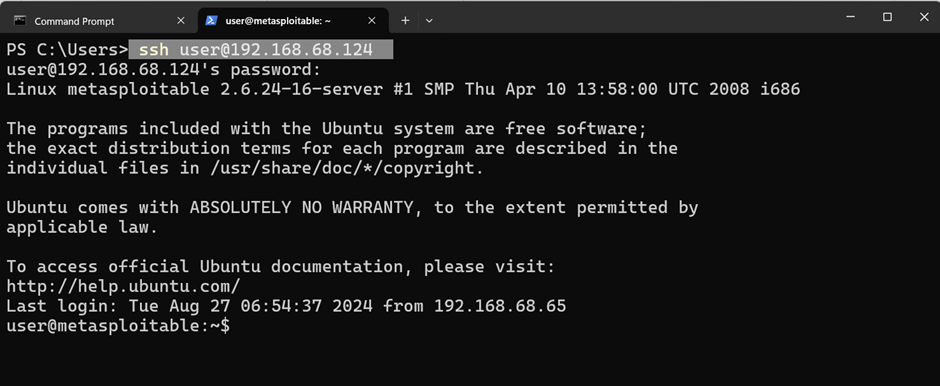
Alt text: Command-line showing an SSH login attempt to a server on Metasploitable2 using default credentials.
- Brute-Force Testing:
While SSH doesn’t support anonymous authentication, weak or default credentials are often the culprit. You can test for vulnerabilities by attempting weak passwords, such as root:toor or admin:admin.
HTTP/HTTPS (Web Services) Port: 80 (HTTP)
Steps:
- Explore the Web Application:
Use a web browser or command-line tool to access the web application:
curl http://<target-ip>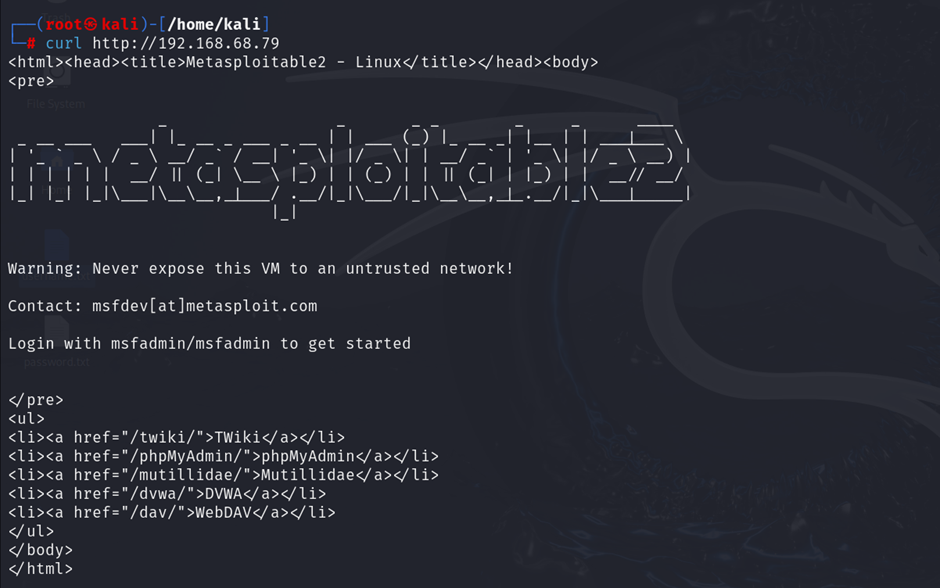
Alt text: HTTP web page displayed in a browser, part of Metasploitable2’s vulnerable services.
- Test for Anonymous Access:
Look for pages or functionality that can be accessed without login credentials. For example, directories or forms that allow users to upload or view files without authentication.
- Check Hidden Resources:
Use tools like directory brute-forcers to discover hidden resources that may be exposed:
gobuster dir -u http://<target-ip> -w /path/to/wordlist.txt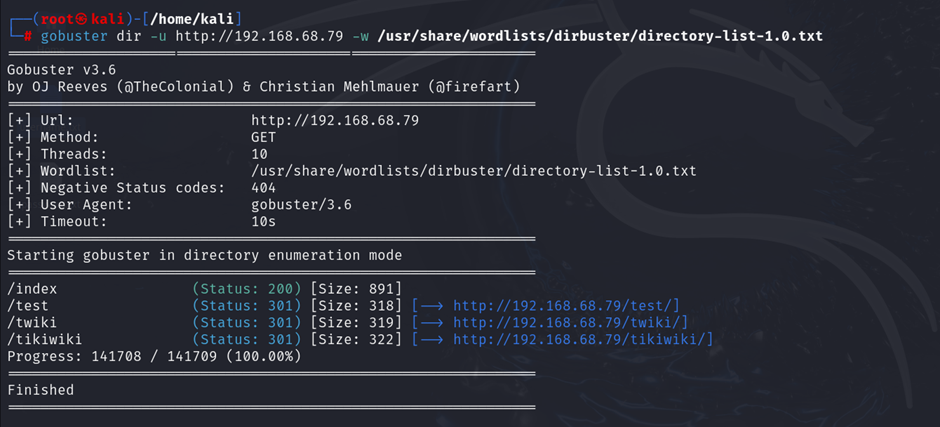
Alt text: Directory brute-forcing result showing hidden directories on Metasploitable2.
MySQL (Database Service) Port: 3306
Steps:
- Test for Default Credentials:
Use the MySQL client to attempt a connection with default credentials:
mysql -h <target-ip> -u root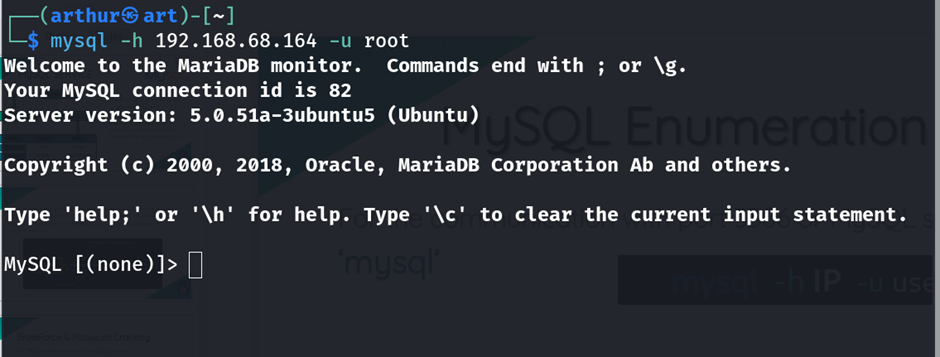
Alt text: MySQL client connected to a database on Metasploitable2 using default credentials.
- Check for Anonymous Access:
If connected, explore the database and run queries to see if you can access or modify data without proper authentication.
PostgreSQL Port: 5432
Steps:
- Attempt Connection:
Use the PostgreSQL client psql to connect with default or weak credentials:
psql -h <target-ip> -U postgres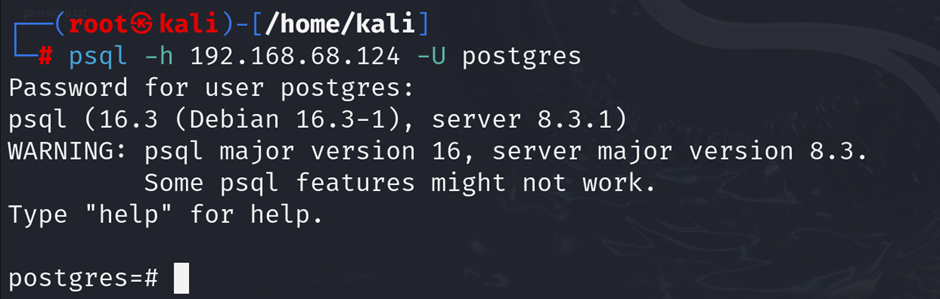
Alt text: PostgreSQL client attempting to connect to a database on Metasploitable2 using default credentials.
- Test Access:
Once connected, check whether you can access sensitive data without proper credentials.
Telnet Port: 23
Steps:
- Connect to Telnet:
Use the telnet command to connect and try default or weak credentials:
telnet
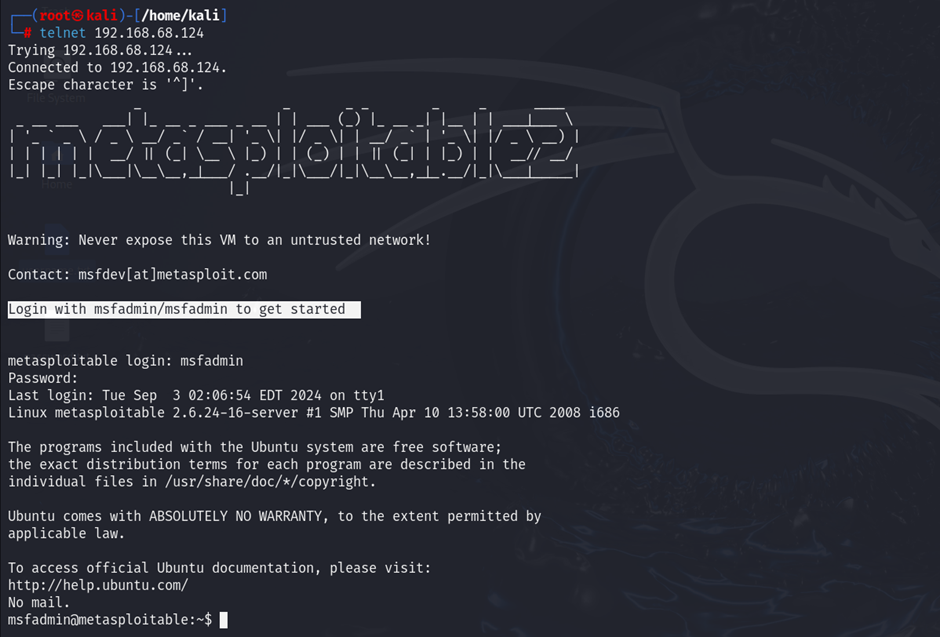
Alt text: Telnet connection attempt to a server on Metasploitable2 using default credentials.
- Test for Access:
If login is successful with default or no credentials, explore the system and investigate what commands are available to the anonymous user.
RPC (Remote Procedure Call) Using rpcclient Port: 135 (typically for RPC services, but RPC can use dynamic ports)
Steps:
- Connect Using rpcclient:
Use rpcclient to connect to the target and test for anonymous access:
rpcclient -U "" <target-ip>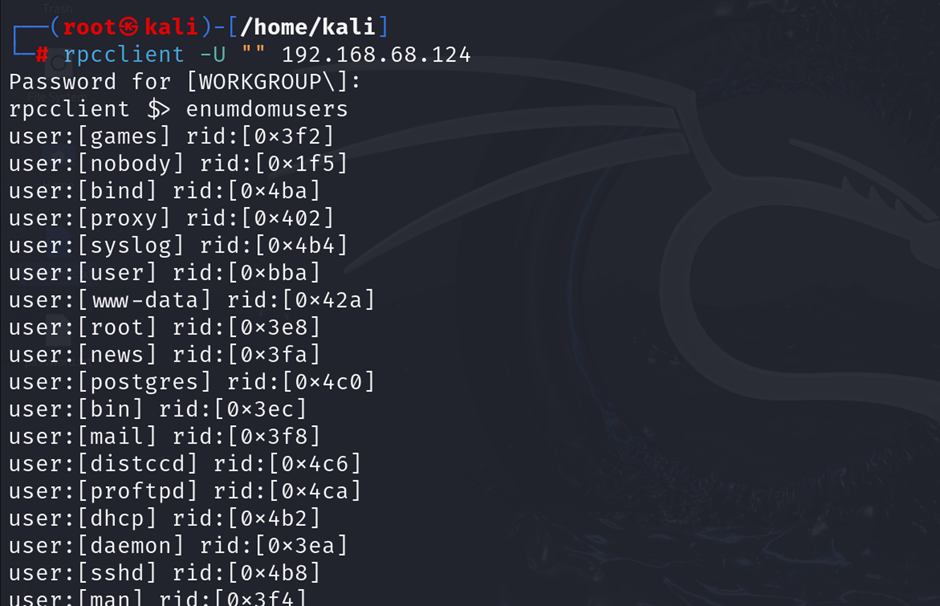
Alt text: RPC client connecting to an RPC service on Metasploitable2 using anonymous credentials.
- Enumerate Information:
Once connected, you can run commands to enumerate users or list shares:
rpcclient -U "" <target-ip> -c "enumdomusers"
rpcclient -U "" <target-ip> -c "netshareenum"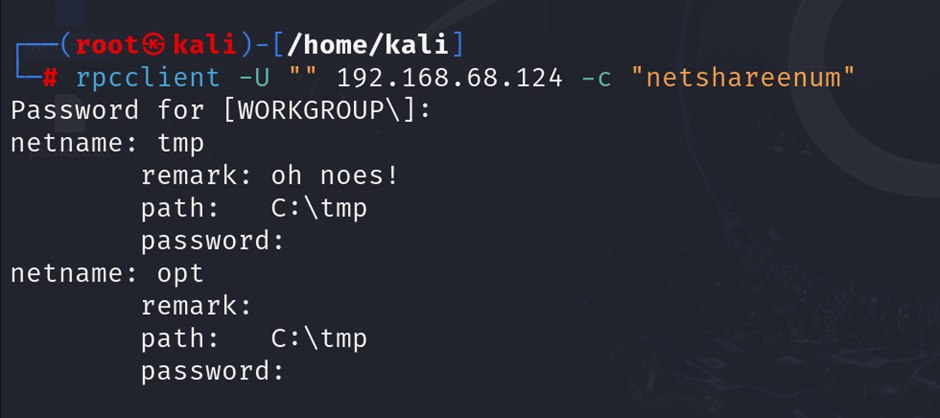
Alt text: Output of rpcclient showing enumerated domain users and available shares on Metasploitable2.
- Test Access to RPC Services:
Explore other actions to determine whether sensitive information or services can be accessed without proper authentication.
Special thanks
Dheeraj Prabhu K, Senior Security Analyst at CyberSapiens, for contributing his expertise to this content.
Conclusion
Anonymous authentication provides convenience by allowing access without credentials, but it also introduces significant security risks. This unrestricted access can lead to unauthorized users viewing or manipulating sensitive data, potentially resulting in serious breaches or system compromises.
From a technical perspective, anonymous authentication can create vulnerabilities that need regular monitoring and assessment. While it may simplify certain processes, it also requires stringent security measures to prevent exploitation. Understanding and managing these risks effectively is essential to safeguarding valuable data and maintaining robust cybersecurity.
By following these steps across different services such as FTP, SMB, SSH, and databases like MySQL and PostgreSQL, you can improve your knowledge of network security and the importance of authentication in protecting sensitive resources.












