Hacking and Scamming are often used interchangeably, but they have distinct meanings and connotations. While both involve deceitful activities aimed at exploiting vulnerabilities or tricking individuals, the methods, intentions, and outcomes are quite different.
In this article, we will delve into the Difference Between Hacking and Scamming, exploring their definitions, techniques, and consequences.
What is Hacking?
Hacking, in its purest form, is the practice of finding and exploiting vulnerabilities in computer systems, networks, or applications. Hackers use various techniques to bypass security measures, gain unauthorized access, or disrupt systems to demonstrate flaws or test defences. Initially, hacking was seen as a form of artistic expression, with pioneers like John Draper (aka “Captain Crunch”) using their skills to expose weaknesses and push the boundaries of computer security.
However, as the dark side of hacking emerged, the term took on a negative connotation. Malicious hackers, also known as “black-hat” hackers, began to use their skills for financial gain, espionage, or sabotage. They compromised systems, stole sensitive data, and disrupted online services, often for personal enrichment or to advance malicious agendas.
Types of Hacking
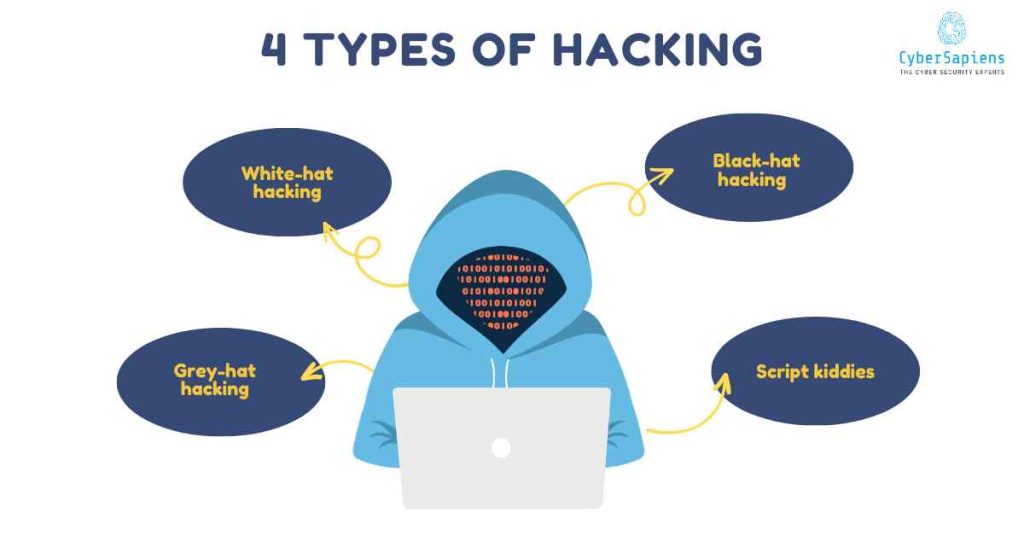
There are various types of hacking, including:
1. White-hat hacking
An ethical hacker may perform an exercise such as penetration testing, vulnerability Analysis and security auditing to increase the level of security and find the chinks in the armour.
2. Black-hat hacking
Cybercriminals on the other hand want to take advantage of these openings for ill intentions, often as a way of enriching themselves or as a means of stealing stuff.
3. Grey-hat hacking
Grey-hat hackers are a combination of white and black-hat hackers in that they find weaknesses and very often will use those weaknesses, but then report it back to the owner of the system, possibly for a fee.
4. Script kiddies
Script kiddies are new to the hacking world and therefore, use tools and exploit weaknesses of systems crusade without comprehending the system’s fundamentals.
What is Scamming
Scamming, on the other hand, is the practice of deceiving individuals or organizations into divulging sensitive information, revealing vulnerabilities, or surrendering valuable assets. Scammers use psychological manipulation, social engineering, and clever tactics to trick their targets into revealing confidential information or performing actions that compromise their security.
Types of Scamming
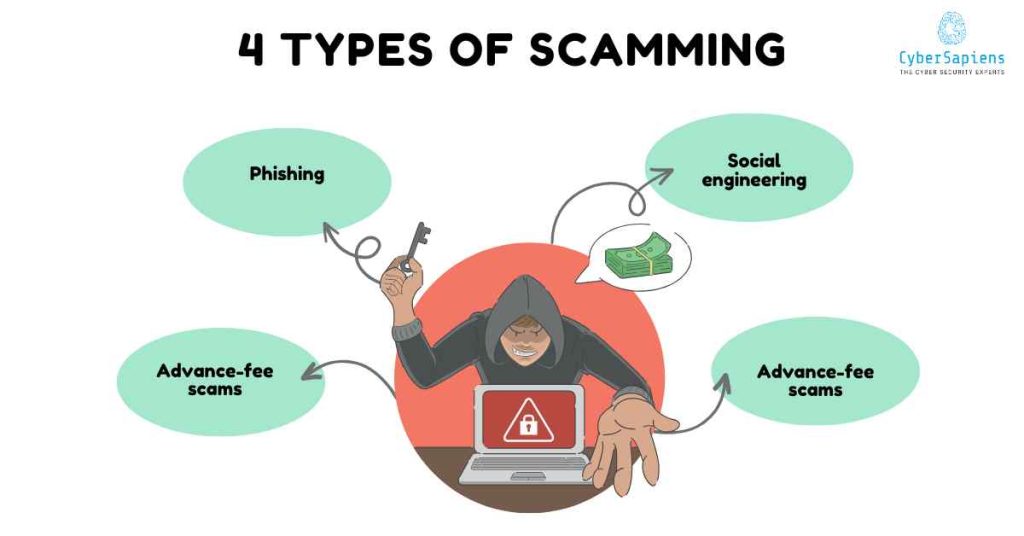
Scamming encompasses a wide range of techniques, including:
1. Phishing
It occurs when criminals use the identity of a well-known person in the recipient’s network to mail, message, or call the target in an effort to get them to disclose personal details.
2. Social engineering
Most fraudsters rely on actual influence to get their targets to compromise by earning their confidence.
3. Advance-fee scams
Fraudsters then claim a given return or a given benefit that will be received in future once certain charges are paid or else a given information is disclosed.
4. Malware distribution
Cybercriminals fool people into downloading Malware or viruses that affect the owner of the device.
Key Differences Between Hacking and Scamming
While hacking and scamming often overlap, the following key differences distinguish them:
1. Technical expertise
In general, hacking entails inputting unauthorized code into systems which usually calls for a certain level of programming skill. Consequently, while scamming targets individuals, they use social engineering, psychology, and persuasion.
2. Goals
In most cases, hacking is mainly used to investigate the weaknesses of the defences, stealing information and then selling it. Frauding makes one’s goal to elicit personal information, money and/or property from another.
3. Tactics
Usually, hacking refers to the logical way of gaining access to the system by using tools, techniques, and algorithms. They are an exercise in societal manipulation, and psychological coercion, and employ a wide variety of tricks with their targets.
4. Target audience
Hacking is a more random activity that is aimed at an organization, a company or network or a system, while scamming is a more direct form of attack that is aimed at a person normally through social engineering or phishing.
Please find the table below for a clear understanding
| Characteristics | Hacking | Scamming |
| Technical Expertise | Requires programming skills and technical knowledge | Uses social engineering, psychology, and persuasion |
| Goals | Investigate weaknesses, steal information, disrupt systems | Elicit personal information, money, and/or property |
| Tactics | Uses tools, techniques, and algorithms to gain unauthorized access | Employs tricks, deception, and psychological coercion |
| Target Audience | Organizations, companies, networks, or systems | Individuals, often through social engineering or phishing |
| Outcome | Exploits vulnerabilities, compromises systems | Tricks individuals into revealing sensitive information or performing compromising actions |
| Method | Involves finding and exploiting vulnerabilities in systems or networks | Relies on deceiving individuals or organizations into divulging sensitive information |
| Intent | Exploits vulnerabilities, compromise systems | Typically malicious, with the intention of personal gain or exploitation |
Useful Resources:
Here are some useful resources:
Conclusion
In conclusion, hacking and scamming are distinct concepts, each with its own motivations, techniques, and outcomes. Hacking involves the exploitation of vulnerabilities in systems or networks, often with technical expertise.
Scamming, on the other hand, relies on social engineering, persuasion, and deception to trick individuals into revealing sensitive information or performing compromising actions.
FAQs: Difference Between Hacking and Scamming
1. What is the main difference between hacking and scamming?
The main difference between hacking and scamming is that hacking involves the exploitation of vulnerabilities in systems or networks to gain unauthorized access while scamming relies on social engineering, persuasion, and deception to trick individuals into revealing sensitive information or performing compromising actions.
2. Is all hacking malicious?
No, not all hacking is malicious. While some hackers have malicious intentions, others, known as “white-hat” hackers, use their skills to test defences and identify vulnerabilities to strengthen security. However, “black-hat” hackers use their skills for malicious purposes, such as financial gain or sabotage.
3. What are the most common types of scams?
The most common types of scams include phishing, social engineering, and advance-fee scams. Phishing scams involve emails or messages that appear to be from trusted sources, attempting to trick individuals into revealing sensitive information. Social engineering involves manipulating individuals into divulging confidential information or performing compromising actions.
4. How can I protect myself from hacking and scamming?
To protect yourself from hacking and scamming, keep your software up-to-date, use strong passwords, and verify the authenticity of emails, messages, or calls. Use anti-malware and anti-virus software, back up your data, and stay informed about common hacking and scamming techniques.
5. What is the difference between a hacker and a scammer?
A hacker uses technical expertise to exploit vulnerabilities in systems or networks, while a scammer relies on social engineering, persuasion, and deception to trick individuals into revealing sensitive information or performing compromising actions.
6. Can I get hacked through social media?
Yes, you can get hacked through social media. Hackers often target social media platforms to gather sensitive information, distribute malware, or trick individuals into revealing confidential data.
7. What is phishing?
Phishing is a type of scam that involves sending emails or messages that appear to be from trusted sources, attempting to trick individuals into revealing sensitive information, such as login credentials or financial information.
8. How can I identify a phishing email or message?
To identify a phishing email or message, look for spelling or grammatical errors, suspicious URLs, or requests for sensitive information. Be cautious of unsolicited messages or emails claiming to be from trusted sources.
9. Can I report hacking and scamming incidents?
Yes, you can report hacking and scamming incidents to the relevant authorities. If you’re a victim of hacking or scamming, report the incident to your local police department, the Federal Trade Commission (FTC), or the Internet Crime Complaint Center (IC3).
10. Is there any way to prevent hacking and scamming completely?
While no one can completely prevent hacking and scamming, you can minimize the risk by staying informed, implementing security measures, and being cautious when online. Regularly update your software, use strong passwords, and be vigilant of suspicious activity to protect yourself from hacking and scamming.












