Both tech enthusiasts and businesses alike are showing enthusiasm for the iPhone 16.
Be it personal usage or ways through which it will further enhance productivity, new features are what modern-day attention-seekers across the world get attracted to. In contrast, with any big release regarding technology, there’s also a rise in malicious activity. Cybercriminals keep on seeking openings to make the most of such situations, and the release of the iPhone 16 has proved no exception.
While the iPhone 16 is secured, phishing attacks where cybercriminals disguise themselves as legitimate entities to trick users into revealing sensitive information are on the rise. This blog will explain how such phishing attacks leverage events like the iPhone 16 launch to deceive employees and how your business can stay protected using our PhishCare phishing simulation services.
So, In this article, we are going to discuss how cybercriminals leverage the launch of the iPhone 16 to attack businesses with phishing attacks
How Cybercriminals Use the iPhone 16 Launch to Phish Users?

Whenever a major tech product launches, cybercriminals see it as a golden opportunity to exploit people’s excitement and urgency. The release of the iPhone 16 is no different. Attackers use clever tactics to mimic legitimate communications related to the device, hoping to lure users into clicking malicious links or sharing sensitive information.
Here are some common ways they exploit this event:
1. Phishing Emails from Apple
Phishing emails may appear to be real communications sent by Apple with fake account updates, security alerts, or software updates for your brand-new iPhone 16. Those employees who use their iPhones for work may be specifically easy to scam with such phishing emails.
2. Fake Delivery Notifications
Since many users order iPhone 16 devices online, scammers send fake delivery notifications from carriers like Amazon, Flipkart, or other delivery services. These emails ask the user to click on a malicious link for tracking or provide personal information.
3. Exclusive Offers for new iPhone Owners
Attackers come up with phishing campaigns offering fake promotions or exclusive offers targeted at iPhone 16 buyers. These phishing emails can offer discounts on accessories, free app subscriptions, and special services to target recipients and make them click on malicious links.
4. App Store Scams
These are fake emails that redirect users to download the so-called “must-have apps” for the iPhone 16; these lead to phishing sites where credentials and financial information are compromised.
These kinds of phishing emails may appear valid, particularly when workers are very excited to try using their new gadgets. That’s why PhishCare has become important in helping your workforce be more aware and careful.
The Growing Threat to Businesses
Phishing attacks don’t affect just people; it’s becoming more and more oriented toward businesses.
When any employee clicks on phishing emails, it opens the door to potential data breaches, financial loss, and even access to sensitive company information. This may be highly debilitating for an organization of any size, especially for those organizations working remotely or using hybrid models which may be more susceptible to such targeted phishing attacks.
Events like the launching of the iPhone 16 mean businesses cannot afford to be complacent. Cybercriminals change their modus operandi now and then, so your employees will have to be ahead of them at every turn.
How PhishCare Can Protect Your Business?
PhishCare is a new flagship product solely by CyberSapiens. To stop phishing in its infancy.
With PhishCare you get benefits like:
- End-to-End Tracking Capability
- Fully Customized Templates
- In-Depth Reporting
- Spear-Phishing
- Follow-Up Training
- Security Checkpoint
and a lot more.
PhishCare assists an organization in understanding and improving its defence against phishing. Through the simulation of phishing attacks in real life, we can gauge the level of vulnerability regarding your employees and train them on how to recognise suspicious emails.
What sets PhishCare apart?
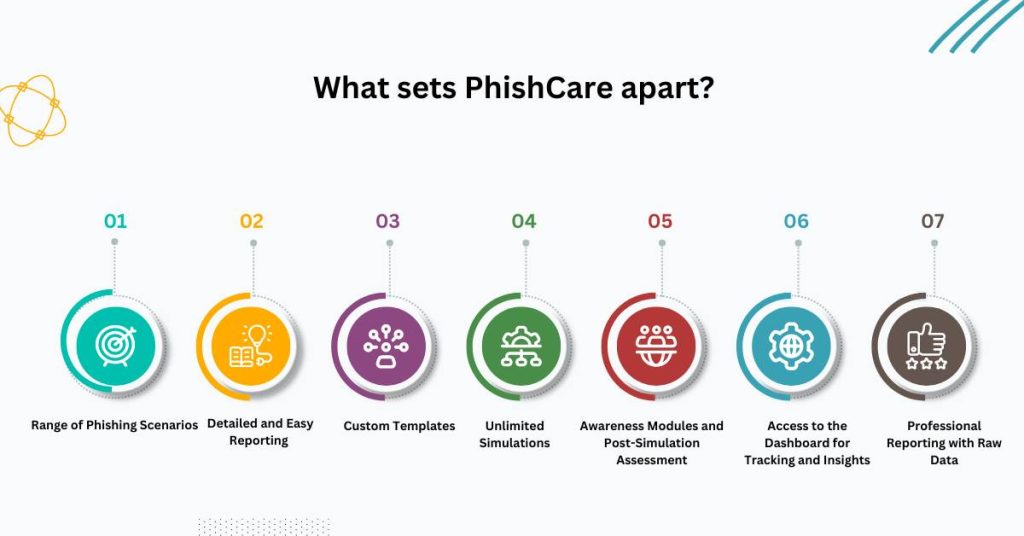
1. Range of Phishing Scenarios
Our simulations model all types of phishing scenarios, including real-world situations such as the launch of the iPhone 16. Such tailor-made simulations would give your staff the experience of receiving emails of the type they are most likely to receive.
2. Detailed and Easy Reporting
Immediately after a simulation, you will receive in-depth reports of how employees reacted. Who clicked the link? Who reported the e-mail? Our intuitive reports provide great insight into the readiness of your organization.
3. Custom Templates
We provide customizable phishing templates for specific industries and risks that your business faces. Whether it be finance, healthcare, or retail, our phishing simulations mimic real-world threats associated with your sector.
4. Unlimited Simulations
Since the threats are ever-evolving, PhishCare does allow for an unlimited amount of phishing simulations to be done, creating a new opportunity to keep your team sharp and alert with the latest arsenal that attackers use.
5. Awareness Modules and Post-Simulation Assessment
Whenever an employee gets phished by our simulated phishing, we train them through awareness modules to educate them on how to prevent being phished. Once they have gone through the module, a post-assessment of the staff will be done to ensure they can identify phishing emails and know how to avoid them.
6. Access to the Dashboard for Tracking and Insights
We provide a single-point dashboard where you can track your team’s performance, current simulations running, and get an overview of your company’s overall phishing risk level. This helps you keep up to date with your cybersecurity strategy.
7. Professional Reporting with Raw Data
Once the simulation exercise is over, you will get raw data which you can use for further analysis. This is particularly helpful for internal audits and tightening security measures.
Benefits Our Clients Have Reaped!
Numerous businesses with whom we have conducted PhishCare have reportedly witnessed a realistic increase in the capability of their employees to identify phishing attempts. Following is what one satisfied customer has to say
Why Does Every Business Need PhishCare?
Phishing attacks can happen to any business at any time, and the stakes are high. The release of the iPhone 16 brings new excitement and activity; cybercriminals will surely use this event to their advantage in targeting businesses and individuals alike.
Don’t wait until an attack is successful. Safeguard your organization through employee education and proactive defence against phishing threats now. Our PhishCare simulation tool is designed to keep your team one step ahead of cybercriminals.
Conclusion: Protect Your Business Today
At CyberSapiens United LLP, we’re here to help safeguard your organization from phishing attacks. For more on our PhishCare-phishing simulation services or to schedule a simulation with your business, visit our page. Let’s protect your business together and build a stronger, more resilient cybersecurity posture for your company.
FAQs
1. What are phishing attacks, and how do they relate to the iPhone 16 launch?
Ans: Phishing attacks are a type of cyberattack where attackers send fake emails, messages, or communications that appear to be legitimate, aiming to trick victims into divulging sensitive information. With the launch of the iPhone 16, cybercriminals are leveraging the excitement and anticipation surrounding the event to launch phishing attacks against businesses.
2. How can I identify phishing emails or messages related to the iPhone 16?
Ans: To identify phishing emails or messages related to the iPhone 16, look out for spelling and grammar mistakes, generic greetings, and emails or messages that create a sense of urgency. Be cautious of links or attachments from unknown sources, and never provide sensitive information without verifying the authenticity of the email or message.
3. What are the most common types of phishing attacks related to the iPhone 16?
Ans: Some common types of phishing attacks related to the iPhone 16 include pre-order scams, fake contests and giveaways, malicious accessories, iPhone 16 pre-order delays, and emails or messages claiming to offer new features or updates.
4. How can I protect my business from phishing attacks related to the iPhone 16?
Ans: To protect your business from phishing attacks related to the iPhone 16, educate your employees on the risks of phishing attacks, implement security software, establish a robust security policy, and encourage employees to report suspicious emails or messages.
5. What is the impact of phishing attacks on businesses?
Ans: Phishing attacks can lead to data breaches, financial losses, reputation damage, and system compromise. It is essential to take proactive measures to protect your business from these types of attacks.
6. How can I report suspicious emails or messages related to the iPhone 16?
Ans: If you receive a suspicious email or message related to the iPhone 16, report it to your IT department or the relevant authorities. You can also forward the email to Apple’s security team to help prevent further phishing attacks.
7. What are the best practices for avoiding phishing attacks?
Ans: Best practices for avoiding phishing attacks include being cautious with links, verifying the source of emails and messages, watching for spelling and grammar mistakes, and being wary of urgency. It is also essential to use two-factor authentication, regularly update software, and use strong, unique passwords.
8. How can I verify the authenticity of emails or messages related to the iPhone 16?
Ans: To verify the authenticity of emails or messages related to the iPhone 16, check the sender’s email address, look for the Apple logo, and be cautious of generic greetings. You can also contact Apple’s customer support directly to verify the authenticity of the email or message.
9. What should I do if I have already provided sensitive information in response to a phishing attack?
Ans: If you have already provided sensitive information in response to a phishing attack, immediately change your passwords and notify your bank or credit card company. You should also report the incident to your IT department and the relevant authorities.
10. How can I stay up-to-date on the latest phishing attacks and security threats related to the iPhone 16?
Ans: To stay up-to-date on the latest phishing attacks and security threats related to the iPhone 16, follow reputable sources, such as Apple’s security blog, and keep an eye on cybersecurity news and updates. Regularly review your business’s security policies and procedures to ensure you are prepared to respond to emerging threats.












