In the current cybersecurity environment, establishing a well-organized Security Operations Center (SOC) is vital for organizations aiming to safeguard their assets and respond to threats effectively.
A SOC playbook serves as a crucial element of this framework, offering a standardized method for managing security incidents and enabling SOC teams to react promptly and efficiently.
This blog will lead you through the steps of How to Develop a SOC Playbook, highlighting important factors you should consider and offering templates to help you begin.
Introduction to SOC Playbooks
A Security Operations Center (SOC) playbook is a vital tool designed to guide security teams in effectively managing and responding to cybersecurity incidents.
In an era where cyber threats are increasingly sophisticated and prevalent, having a structured approach to incident response is no longer optional; it is essential for maintaining the integrity and security of an organization’s assets.
A SOC playbook acts as the operational framework for your security team, detailing step-by-step procedures for detecting, analyzing, and responding to various security incidents.
With a comprehensive playbook in place, your SOC can maintain consistency in its responses, minimize the time required to tackle threats and enhance the overall security posture of the organization.
This structured approach not only streamlines decision-making but also ensures that every team member is clear on their roles and the actions to take before, during, and after a security incident
Key Considerations in Developing a SOC Playbook
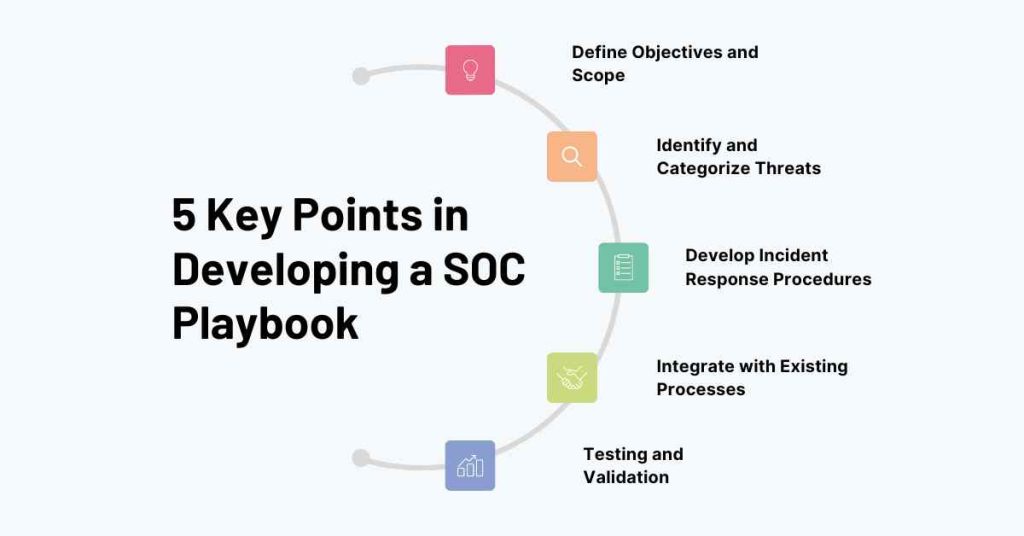
1. Define Objectives and Scope
- Purpose: Clearly define what the SOC playbook aims to achieve. Is it to standardize responses, ensure compliance, or improve incident response times?
- Scope: Determine the scope of the playbook. Will it cover all possible incidents, or will it focus on specific areas such as malware detection, phishing, or insider threats?
2. Identify and Categorize Threats
- Threat Identification: List the types of threats your organization is most likely to face. Use threat intelligence sources to understand the current threat landscape.
- Categorization: Group these threats into categories such as malware, phishing, DDoS attacks, insider threats, etc. This categorization will help in developing targeted response procedures.
3. Develop Incident Response Procedures
- Step-by-Step Process: For each threat category, outline a step-by-step response process. This should include detection, analysis, containment, eradication, recovery, and post-incident review.
- Roles and Responsibilities: Clearly define the roles and responsibilities of each team member during an incident. This ensures that everyone knows their part in the response process.
4. Integrate with Existing Processes
- Alignment: Ensure that the SOC playbook aligns with existing security policies, compliance requirements, and business continuity plans.
- Automation: Where possible, integrate automated tools and processes into the playbook. Automation can significantly reduce response times and minimize human error.
5. Testing and Validation
- Tabletop Exercises: Regularly conduct tabletop exercises to test the effectiveness of the playbook. This will help identify gaps and areas for improvement.
- Continuous Improvement: The threat landscape is constantly evolving, and so should your playbook. Regularly review and update the playbook to ensure it remains relevant.
Here is the Sample SOC Playbook Template
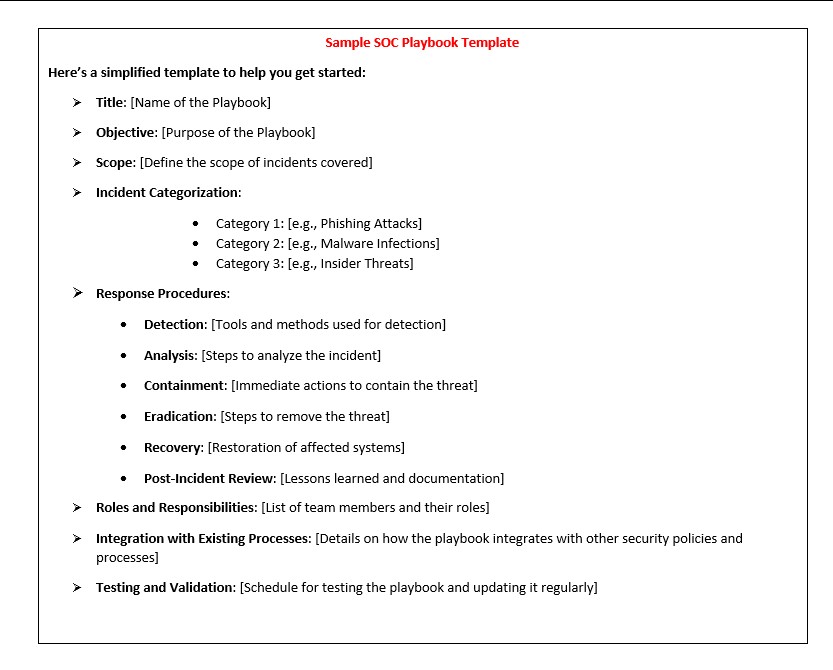
Here is the description of the sample soc playbook template:
1. Title: [Name of the Playbook]
- Purpose: The title should reflect the purpose of the playbook, such as the “SOC Incident Response Playbook” or “Phishing Incident Response Playbook.” This helps quickly identify the specific playbook needed for different incident types.
2. Objective: [Purpose of the Playbook]
- Explanation: Define the overarching goal of the playbook. For example, the objective could be to provide a standardized approach for detecting, analyzing, and responding to phishing attacks. The objective should align with the organization’s overall security strategy and business objectives.
3. Scope: [Define the Scope of Incidents Covered]
- Explanation: Clearly outline the types of incidents that the playbook will address. Specify the environments (e.g., cloud, on-premise, hybrid) and systems (e.g., email servers, web applications) covered by the playbook. For example, “This playbook covers all incidents related to phishing attempts targeting corporate email accounts.”
4. Incident Categorization
- Category 1: [e.g., Phishing Attacks]: Define what constitutes a phishing attack in the context of your organization. Include specific indicators of compromise (IOCs) such as suspicious email addresses, unexpected attachments, or abnormal login attempts.
- Category 2: [e.g., Malware Infections]: Describe different types of malware (e.g., ransomware, spyware) and how they might manifest in your environment. Detail the common vectors for infection, such as email attachments or compromised websites.
- Category 3: [e.g., Insider Threats]: Provide a definition for insider threats, including both malicious and unintentional actions by employees that could harm the organization. Outline how to identify such threats, including unusual access patterns or data exfiltration attempts.
5. Response Procedures
- Detection: [Tools and Methods Used for Detection]: Explanation: List the tools (e.g., SIEM, IDS/IPS) and techniques (e.g., log analysis, anomaly detection) used to detect each type of incident. Detail how alerts are generated and the thresholds for triggering a response.
- Analysis: [Steps to Analyze the Incident]: Explanation: Provide a step-by-step guide for analyzing the incident. This might include examining logs, identifying affected systems, and assessing the potential impact. Include the use of forensic tools and techniques to gather evidence.
- Containment: [Immediate Actions to Contain the Threat]: Explanation: Describe the actions to be taken immediately after detecting an incident to prevent it from spreading. For example, isolating affected systems, disabling compromised accounts, or blocking malicious IP addresses. Emphasize the importance of acting swiftly to minimize damage.
- Eradication: [Steps to Remove the Threat]: Outline the steps to eliminate the threat from the environment. This could involve removing malware, patching vulnerabilities, or conducting a thorough cleanup of compromised systems. Include verification steps to ensure the threat has been fully eradicated.
- Recovery: [Restoration of Affected Systems]: Detail the process for restoring systems to normal operation after the threat has been eradicated. This might include restoring from backups, rebuilding systems, and validating that they are secure. Consider the need for additional security measures to prevent a recurrence.
- Post-Incident Review: [Lessons Learned and Documentation]: Conduct a post-incident analysis to review what happened, how it was handled, and what can be improved. Document all findings, including timelines, actions taken, and any gaps in the response. Use this review to update the playbook and improve future incident responses.
6. Roles and Responsibilities: [List of Team Members and Their Roles]
- Explanation: Clearly define who is responsible for each aspect of the incident response process. For example, the SOC manager might be responsible for overseeing the entire response, while specific analysts might handle detection and analysis. Include contact information and backup personnel to ensure continuity in case of unavailability.
7. Integration with Existing Processes
- Alignment with Security Policies: Ensure that the playbook aligns with the organization’s existing security policies, such as data protection, access control, and incident response policies.
- Compliance Requirements: Detail how the playbook complies with relevant regulations and standards (e.g., GDPR, PCI DSS, ISO 27001). This might include specific reporting requirements, data handling procedures, or audit trails.
- Business Continuity and Disaster Recovery Plans: Describe how the SOC playbook integrates with the organization’s broader business continuity and disaster recovery plans. This ensures that security incidents are managed in a way that minimizes disruption to business operations.
8. Testing and Validation
- Tabletop Exercises: Schedule regular tabletop exercises to test the effectiveness of the playbook. These exercises simulate real-world scenarios to ensure that the team can follow the procedures effectively.
- Red Team/Blue Team Drills: Incorporate red team (attack) and blue team (defence) exercises to test the SOC’s ability to detect and respond to sophisticated threats. Use these drills to identify weaknesses and refine the playbook.
- Continuous Improvement: Establish a process for regularly reviewing and updating the playbook. This might include incorporating lessons learned from actual incidents, updates to tools and technologies, or changes in the threat landscape.
By expanding on each section of the SOC playbook template, you create a comprehensive guide that not only standardizes incident response procedures but also enhances the overall effectiveness of your SOC.
A well-developed playbook ensures that your team is prepared to handle a wide range of security incidents efficiently and consistently, ultimately strengthening your organization’s security posture. Regular testing, validation, and updates will keep the playbook relevant and effective in the face of evolving threats.
Conclusion
Developing a SOC playbook is not just about documenting procedures; it’s about creating a dynamic guide that evolves with the threats your organization faces.
By focusing on key considerations such as defining objectives, categorizing threats, and integrating with existing processes, you can create a playbook that ensures your SOC operates efficiently and effectively.
Implementing this guide and utilizing the provided template will position your organization to respond to security incidents with greater confidence and precision, ultimately strengthening your overall security posture.
FAQs: How to Develop a SOC Playbook
1. What is a SOC Playbook and why is it important?
Ans: A SOC (Security Operations Center) playbook is a comprehensive document that outlines the procedures and guidelines for responding to various types of security incidents. It is important because it provides a systematic approach to incident response, ensuring that all stakeholders are aware of their roles and responsibilities and reducing the mean time to detect and respond to security incidents.
2. What are the key considerations for developing a SOC Playbook?
Ans: The key considerations for developing a SOC playbook include identifying threats, defining roles and responsibilities, outlining incident response procedures, defining communication plans, and establishing metrics for measuring incident response effectiveness.
3. Who should be involved in developing a SOC Playbook?
Ans: The development of a SOC playbook should involve a team of stakeholders including SOC analysts, response teams, management, and other relevant stakeholders. This ensures that the playbook is comprehensive and addresses the needs of all stakeholders.
4. How often should a SOC Playbook be reviewed and updated?
Ans: A SOC playbook should be reviewed and updated regularly to ensure that it remains relevant and effective. This can be done on a quarterly or annual basis, or as needed to address changes in the threat landscape or organizational requirements.
5. What are some best practices for implementing a SOC Playbook?
Ans: Best practices for implementing a SOC playbook include providing training and awareness to all stakeholders, using real-world scenarios to test and refine the playbook, and continuously improving the playbook and incident response process.
6. How can a SOC Playbook help improve incident response times?
Ans: A SOC playbook can help improve incident response times by providing a systematic approach to incident response, outlining the steps for containment, eradication, recovery, and post-incident activities, and establishing clear roles and responsibilities for stakeholders.
7. What are some common mistakes to avoid when developing a SOC Playbook?
Ans: Common mistakes to avoid when developing a SOC playbook include failing to involve all relevant stakeholders, not defining clear roles and responsibilities, not establishing communication plans, and not continuously reviewing and updating the playbook.
8. How can a SOC Playbook help with compliance and regulatory requirements?
Ans: A SOC playbook can help with compliance and regulatory requirements by outlining procedures for incident response and ensuring that all stakeholders are aware of their roles and responsibilities. This can help demonstrate compliance with regulatory requirements and reduce the risk of fines and penalties.
9. How can a SOC Playbook be tailored to a specific organization’s needs?
Ans: A SOC playbook can be tailored to a specific organization’s needs by taking into account the organisation’s threat landscape, incident response requirements, and existing policies and procedures.
10. What are some additional resources for learning more about SOC Playbooks?
Ans: Additional resources for learning more about SOC playbooks include industry guidelines and best practices, such as NIST Special Publication 800-62 and the SANS Institute’s Incident Response Playbook, as well as online training and awareness programs.












