Let me start with this- Cybercrime is not just a technical problem, it’s a psychological problem; it’s a people’s problem.
Computers are the weapons, but the perpetrators as well as the victims are the humans.
The term ‘social engineer’ was first coined in 1894 by Van Marken, in order to highlight the idea that for handling human problems, professionals were needed. Just like you can’t solve technical issues without the proper skills training, you can’t solve social issues without similar skills.
Although, the term was popularized in the IT niche by Kevin Mitnick, a world-famous attacker, active in the 90s, and later-day security researcher and author of the book ‘The Art of Deception’; from where I have extracted and gained various insightful tips in writing this article.
In simple terms, ‘Social engineering’ is a tactic used by attackers to manipulate individuals into giving away sensitive information or performing actions that compromise their data or security.
It mainly involves psychological manipulation and deception, often using social media, email, or phone calls to gain access to personal or confidential data. These attacks can take many different forms, and they are often very effective because they exploit the natural trust that people have in others.
Examples. include phishing scams, tech support scams, social media scams, CEO Fraud scams, lottery scams, etc.
An alternative definition of social engineering, by CSO, is that of the art of gaining access to buildings, systems, or data by exploiting human psychology, rather than by breaking in or using technical hacking techniques.
Table of Contents
SO, WHO ARE THE PEOPLE BEHIND THESE ATTACKS?
In the most generic sense, any common manipulators or fraudsters could be regarded as ‘Social Engineers’ as their sole motive is to deceive, influence and exploit others while preying on their weakness.
But in recent years, “crime-as-a-service” has become the most popular source.
Cybercriminals frequently operate in organizations that resemble businesses. They have an arrangement similar to a quality control system, a supply chain, and occasionally even customer assistance.
As a result, if you find yourself attacked, the likelihood of it coming from a call center-like organization is higher.
Threat actors use social engineering techniques to conceal their true identities and motives, presenting themselves as trusted individuals or information sources.
Attacks using social engineering conceal danger while giving the impression of safety.
The objective is to influence, manipulate or trick users into releasing sensitive information or access within an organization.
Knowing who and what to trust is key to security. It is critical to understand when to take someone at their word and when the person you are speaking with is who they claim to be. The same may be said for online interactions and website usage: When do you trust that the website, you’re using is real or secure to share your information?
HOW DOES IT WORK?
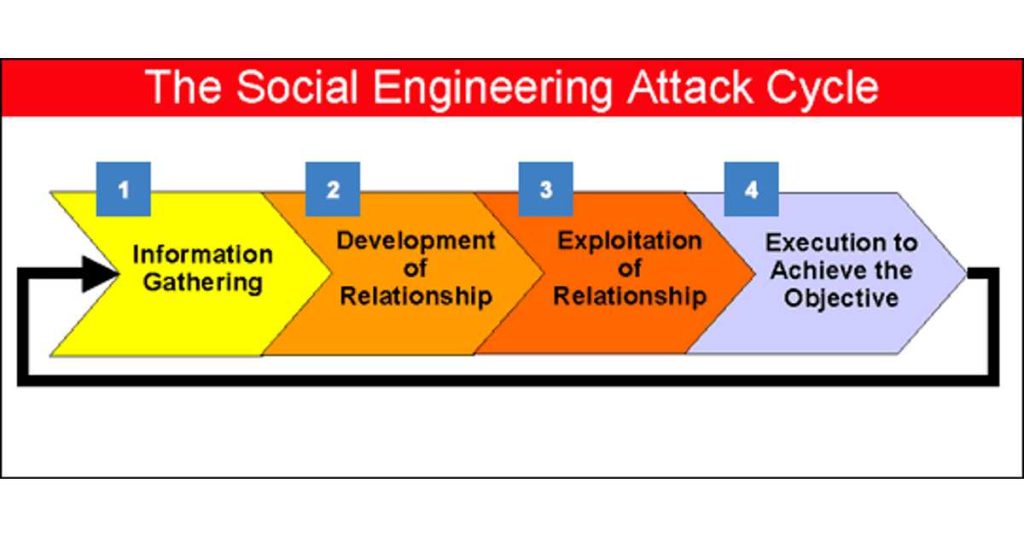
1. Gather Information
The first step in most social engineering attacks is for the attacker to gather information, and perform research and reconnaissance on the target. For instance, if the target is a corporate entity, the attacker might learn about the company’s organizational structure, internal processes, terminology related to the industry, potential business partners, and other details.
2. Infiltrate
As a next step, the attacker tries to infiltrate & develop a relationship with the victim; This is when the attacker approaches you and attempts to gain your trust by creating an understanding with you.
3. Exploitation
Then, the attacker tries to exploit the victim once the relationship is developed and, enough information has been collected. Now the attacker tries to exploit it by gaining confidential information, such as Social Security numbers and credit card or bank account information; makes money off the targets; or gains access to protected systems or networks.
4. Clearing the tracks
Finally, once the intended operation has been carried out, the attacker disengages and deletes his tracks, making it challenging for the victim to trace back any information relating to this specific individual or the action that he executed.
TYPES OF SOCIAL ENGINEERING ATTACKS:

They use various techniques to acquire the information. The popular types will be discussed below.
1. Phishing
It is the practice of sending fake, but often convincing, emails or messages or different media types to thousands of potential victims with the aim of obtaining personal information such as passwords, social security numbers, and credit card details.
Spear Phishing:
It is a type of phishing attack with specific intent. This is similar to phishing, but the attack is personalized to a specific person or organization. Vishing – Vishing, also referred to as voice phishing, is the practice
Smishing:
Smishing, also referred to as SMS phishing is an attack that is carried out over text messaging or short message service (SMS).
2. Baiting
Baiting attacks, as the name implies, use a false promise to spark a victim’s desires or curiosity. They trick people into falling into a trap that takes their personal information or infects their computers with malware.
For example, Tempting offers or emails; These emails urge recipients to purchase a product at a reduced cost or even for nothing. Instead of directing to products, the link leads to malware.
3. Pretexting
Scammers will fabricate a story or lie about who they are while employing pretexts (cover stories) to obtain sensitive personal data.
For example, this is when someone sends an email pretending to be a CEO or other executive from a company and asks for information like a mobile phone number that could be used for password recovery or financial information such as OTP for money transfer, etc.
They will frequently use urgency to make the target feel under pressure.
4. Pharming
The term “pharming” is derived from the words “phishing” and “farming.” In a pharming attack, Scammers go out of their way to keep the URL of their fake website the same as the actual one. As a result, the fraud occurs in the background and is unnoticed by most people. Pharming attacks do not require you to click on a malicious link (as with other types of phishing). Instead, these “pharms” exist online, ready for you to visit them and provide your personal information.
For example, In 2018, scammers moved the MyEtherWallet.com domain to a Russian server hosting an identical replica page.
Before the attack was identified, scammers emptied the accounts of internet users who submitted their login information on the fake site, collecting thousands of dollars in Ether cryptocurrency.
5. Quid Pro Quo
The hacker provides a service or benefit in exchange for information or access in a quid pro quo attack scenario. The most frequent quid pro quo attack happens when a hacker poses as an IT employee of a large company.
For example, The most prevalent scenario for a quid pro quo attack is scammers posing as IT employees. The attacker calls claiming to provide IT support. Again, the scammer will offer to look at the system for bugs & troubleshooting. In exchange for deactivating the antivirus program, the hacker will promise to repair a problem immediately. Once disabled, the fake technician can install malware on the victims’ machines under the mask of software updates.
6. Whaling
Whaling attacks, a particular kind of phishing, target high-profile employees, including the chief financial officer or chief executive officer, in an effort to deceive the targeted person into providing confidential data.
e.g.,
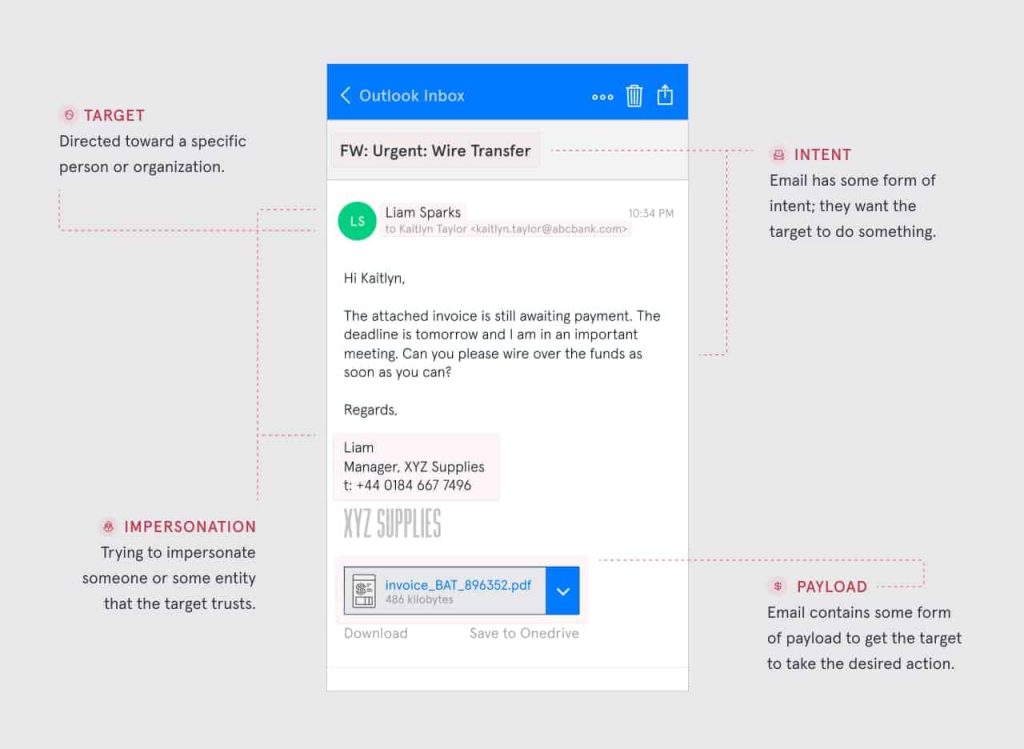
(Source: www.tessian.com)
7. Honey Trap
In this attack, the social engineer pretends to be an attractive person in order to communicate with a person online, fabricate an online relationship, and obtain sensitive information through that relationship.
8. Dumpster Diving
In this case, cybercriminals take the saying “one man’s trash is another man’s treasure” to a whole new level.
In cybersecurity, ‘dumpster diving’ refers to the process of researching an individual’s or organization’s trash in order to recover information that could be used to compromise network resources or plot a cyberattack.
Cyber-criminals use malware to look for recyclable or electronic waste bins for critical information that could jeopardize your company’s security or even lead to data theft.
9. Diversion Theft
This type of attack is also known as the “corner game”.
Scammers attempt to obtain information about items you ordered online. This information may contain the delivery date, address, and item to be delivered. Using this information, attackers pretend as deliver people to give false goods, then wait for the genuine parcels to arrive.
For example, If you order a laptop, the attacker can deliver a malware-infected one. This can be a double profit for the scammer—they get a new laptop and can spy on the victim to steal sensitive data.
10. Scareware
In this type of attack, the victims are bombarded with false alarms and false threats. It involves persuading the victim that their computer is infected with malware or that they have unwittingly downloaded unlawful content. The attacker then offers the victim a remedy to the fake problem; in reality, the victim is tricked into downloading and installing the attacker’s malware.
For example, In 2009, Mac users began receiving scareware to purchase or download fake antivirus software such as Mac Security and MacDefender. This scam was later tied to the Russian online payment system ChronoPay.
11. Watering hole
The term “watering hole attack” comes from hunting. Rather than following its prey over great distances, the hunter predicts where the prey will go, most typically to a body of water (the watering hole), and waits there. When the victim comes to its own accord, typically with its guard down, the hunter attacks.
In this type of attack, the attacker compromises a site likely to be visited by a particular target group, rather than attacking the target group directly.
The purpose is to infect the computer of a targeted person and get access to the network at the target’s workplace.
12. Tailgating
Tailgating, also known as “piggybacking”, occurs when an attacker follows or trails a person with a valid access card into a secured building.
For example, An individual pretends as a delivery driver and waits outside a building. When an employee receives security approval and opens their door, that attacker requests that the employee ‘hold the door’. As a result, access to the company is gained through an authorized person.
13. Rogue Attacks
Rogue attacks trick their victims into purchasing fake and malicious security software, in order to install ransomware, which prevents access to a system or data until a ransom is paid.
This type of malware tricks targets into paying for the fake removal of malware.
14. Third-party attacks
Attackers go after targets outside of the intended target organization, or through a third party. The objective is to infect a person’s phone or computer with malware, which will then connect to the network of the target company.
For example, an online dating or social networking site could be a third party.
15. Artificial Intelligence (AI)
As AI becomes smarter, Morawietz warns, a social engineering “epidemic” is mounting.
Deepfakes use artificial intelligence (AI)-generated audio or video that is capable of being able to impersonate politicians, celebrities, or even the co-workers, friends, or family of an ordinary individual. Deepfakes, which are currently legal, but unregulated, will soon be simpler to create, harder to detect, and widely spread. For example, In 2019, fraudsters cloned the voice of a chief executive and successfully tricked a CEO into transferring a substantial sum of money. Similar crimes have emerged using the same technology.
Do Read the Second Part of this Blog By Clicking Here!
About the Author!













