Penetration testing pen testing or ethical hacking is a form of software testing that attempts to overlook weaknesses in a computer system or network with the consent of the computer system’s owner. Penetration testing plays an especially significant role in the area of cybersecurity, as it allows for the definition of the main threats and risks an organization faces and thus helps prevent real-world attacks by increasing security.
Here we will describe the list of Top 50 Best Penetration Testing Tools segregated according to categories. These tools are important for security professionals, IT ethic hackers, and pen testers to employ dummy attacks that aid in strengthening network security.
Why Penetration Testing Tools are useful?
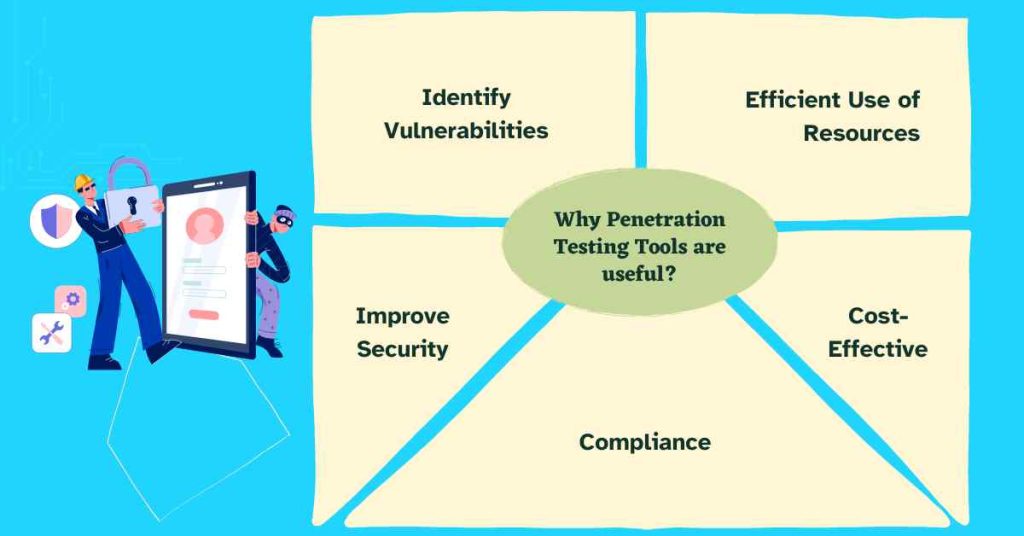
So, Before going into the main topic first, let’s see why these Penetration Testing Tools are useful:
1. Identify Vulnerabilities
Automated security tools used in a penetration testing process provide necessary information about an organization’s security weaknesses of their PC, networks, and applications to eliminate potential threats by potential invaders as early as possible.
2. Improve Security
Penetration testing tools describe real-world attacks that make an organization’s security better by discovering and explaining vulnerabilities and how to fix them.
3. Compliance
PCI DSS, HIPAA, and GDPR guidelines are some of the regulations that recommend organizations perform penetration testing from time to time in a bid to protect the data.
4. Cost-Effective
The use of penetration testing tools can prevent organizations from suffering terrible costs, including notification, remedial measures, and reputation loss.
5. Efficient Use of Resources
Automated tools in pen testing should avoid providing solutions so that the IT experts can search for other ways to solve the dilemma and focus on more productive work.
List of Top 50 Best Penetration Testing Tools

The wait is over after so much hectic research from our cybersecurity professional here is the list of the Top 50 Penetration Testing Tools:
1. Nmap
Nmap is a free and open-source tool that allows for comprehensive network exploration. It performs port scanning, operating system (OS) detection, and service version. Nmap is a favourite among open-source network discovery tools, OS identification, and checks on ports.
2. Masscan
A high-speed and highly configurable TCP port scanner.
3. Angry IP Scanner
A tool for network discovery using IP address recognition and scan that is very fast and easy to use.

4. NetScan
A security tool used in network mapping, identification of operating systems and vulnerability of the host’s ports.
5. OpenVAS
A complete and free vulnerability scanner and mentioned network security testing tool.
6. Metasploit Framework
A software tool that is free and can be modified by anyone for testing security loopholes.
7. Nessus
An open-source software that works as a commercial vulnerability scanner and penetration testing tool.
8. OpenVAS
An open-source tool with the features of a vulnerability scanner as well as a penetration testing tool.
9. Burp Suite
A tool that can be used to test web applications for security breaches.And Hack a particular web application to find out areas that require security
10. ZAP (Zed Attack Proxy)
An application that scans web applications for vulnerabilities and is released under the open source licence.
11. John the Ripper
A Linux, Windows, and macOS fast password cracker.
12. Aircrack-ng
A full set of possible nifty wireless network hacking and penetration testing apparatus.
13. Hydra
A faster and very flexible form of password cracking mechanism.
14. Medusa
Medusa is a fast and path password breaker.
15. THC-Hydra
t is a network-authenticated parallelized login cracker meaning you can use it to parallel cracked login tcp-ip authentication.
16. OWASP ZAP (Zed Attack Proxy)
This is an open-source scanner that is used to check the security of web applications.
17. W3af
A WAAF is a framework for a web application attack and audit.
18. BeEF (Browser Exploitation Framework)
BeEF (Browser Exploitation Framework) is An open-source penetration testing tool suitable for web browsers.
19. SQLMap
SQL Map is an open-source tool that automizes SQL injection.
20. Wifite
Wifite is an Auditing and cracking wireless networks tool.

21. Reaver
A tool for attacking and recovering WPA/WPA2 passwords of Wi-Fi networks through opening WPS.
22. SET (Social-Engineer Toolkit)
A tool that can be used in social engineering and given that it is open source, penetration testing.
23. Phishing Tank
This is a phishing framework for both testing the companies’ penetration vulnerability and training their workers on how to deal with these threats.
24. StegHide
Stegano is a Python application for concealing information into image files.
CryptoCat: An end-to-end encrypted and an open source instant messaging and communication application.
25. TrueCrypt
An abandoned, but still effective, encryption utility.
26. Wireshark
This is a commonly used network protocol analyzer for sniffing and analysis of protocol traffic on the network.
27. Tcpdump
It is a command-line-based network protocol analyzer.
28. Tshark
A terminal-based network protocol analyzer and a clone of Wireshark.
29. Meterpreter
A malware tool designed to operate on the target systems that have been infected by a previous stage of the attack.
30. Cobalt Strike
A professional program is used after gains have been extracted for lateral movement and data exfiltration.
31. Empire
A framework for post-exploitation on the three OSes: Windows, Linux and macOS.
OllyDbg: Software tool – debugger specifically for Windows operating system that is 32-bit.
32. Immunity Debugger
A Windows-based debugger with a primary focus on exploits.
33. x64dbg
A Windows debugger is a 64-bit tool that combines debugging architecture and runtime analysis.
34. Binary Ninja
A binary-level tool for both reversing as well as debugging.
35. Kali Linux
A Linux distribution for computers, also known as digital, forensics and ethical hacking or penetration testing.
36. Parrot Security OS
A specific kind of Linux distribution is used for penetration testing and digital forensics.
37. BlackArch Linux
An operating system based on Linux for penetration testing and security analysis.
38. Maltego
A network exploration and mapping tool and also an information-gathering tool.
39. Recon-ng
A previously described and well-known web reconnaissance framework.
40. DNSRecon
A DNS OSINT reconnaissance tool.
41. Nmap Scripting Engine
Nmap add-on for scripting more elaborate checks.
42. Splunk
A data analysis and control system for security information.
43. ELK Stack (Elasticsearch, Logstash, Kibana)
A security information data analysis and monitoring system.
44. Weevil
A free and open-source social engineering framework that can be used to create phishing attacks and other social engineering campaigns.
45. RainbowCrack
This tool precomputes hashes for a large set of passwords, enabling rapid password cracking when the hash of a stolen password is available.
46. Phishing Frenzy
This cloud-based platform allows for creating and launching targeted phishing simulations, enabling organizations to train employees on identifying and avoiding phishing scams.
47. Hashcat
Another powerful password-cracking tool, Hashcat utilizes various cracking techniques (including GPU acceleration) to crack complex passwords.
48. Kismet
This wireless network detector and sniffer allows for network reconnaissance, identifying access points (APs), capturing wireless packets, and analyzing network traffic for vulnerabilities.
49. Ettercap
A powerful suite for network sniffing and man-in-the-middle attacks, Ettercap enables pen testers to capture network traffic, modify packets on the fly, and potentially steal sensitive information.
50. IDA Pro
Another powerful debugger, known for its advanced features and support for various architectures.
Summary
- Nmap
- Masscan
- Angry IP Scanner
- NetScan
- OpenVAS
- Metasploit Framework
- Nessus
- OpenVAS
- Burp Suite
- ZAP (Zed Attack Proxy)
- John the Ripper
- Aircrack-ng
- Hydra
- Medusa
- THC-Hydra
- OWASP ZAP (Zed Attack Proxy)
- W3af
- BeEF (Browser Exploitation Framework)
- SQLMap
- Wifite
- Reaver
- SET (Social-Engineer Toolkit)
- Phishing Tank
- StegHide
- TrueCrypt
- Wireshark
- Tcpdump
- Tshark
- Meterpreter
- Cobalt Strike
- Empire
- Immunity Debugger
- X64dbg
- Binary Ninja
- Kali Linux
- Parrot Security OS
- BlackArch Linux
- Maltego
- Recon-ng
- DNSRecon
- Nmap Scripting Engine
- Splunk
- ELK Stack (Elasticsearch, Logstash, Kibana)
- Weevil
- RainbowCrack
- Phishing Frenzy
- Hashcat
- Kismet
- Ettercap
- IDA Pro
Conclusion
In conclusion, penetration testing provides an effective solution in cyber security and correct tools must be used due to replications of real threats and weaknesses.
Above is the list of the top 50 best penetration testing tools that will give a general understanding of the most effective tools currently in use. It is important to emphasize that all the mentioned tools should be used legally and ethically with permission and within the given scope.
FAQs: Top 50 Best Penetration Testing Tools
1. What are penetration testing tools?
Ans: Penetration testing tools are specialized software applications used to simulate cyberattacks and identify vulnerabilities in systems, networks, and applications. These tools empower pen testers to discover weaknesses before malicious actors exploit them.
2. Why are there different categories of pen testing tools?
Ans: Pen testing tools are categorized based on their functionalities. Network vulnerability scanners identify broad security weaknesses, while web application security scanners focus on vulnerabilities specific to web applications. Enumeration tools gather information about target systems, and password-cracking tools attempt to crack weak passwords. Each category plays a vital role in a comprehensive pen test.
3. Are there free and open-source pen testing tools available?
Ans: Absolutely! While some powerful tools are commercial, there’s a wide range of free and open-source options available. Popular examples include OpenVAS (vulnerability scanner), Burp Suite (web application security scanner), and Nmap (network scanner).
4. Is a single tool enough for a pen test?
Ans: No. Pen testing is a multi-faceted process, and different tools address various aspects. A combination of tools from different categories is typically used for a thorough assessment.
5. What factors should I consider when choosing a pen testing tool?
Ans: The “best” tool depends on your specific needs. Consider factors like the scope of your pen test, budget constraints, technical expertise, and the target system’s nature.
6. Is it legal to use pen testing tools?
Ans: Using pen testing tools is legal only with explicit permission from the owner of the system or network being tested. Conducting unauthorized pen testing is considered illegal hacking.
7. Do I need to be a security expert to use pen testing tools?
Ans: While advanced tools require specialized knowledge, some beginner-friendly options are available. However, for effective pen testing, a strong understanding of cybersecurity concepts and vulnerabilities is recommended.
8. How can I learn more about pen testing tools?
Ans: Many online resources offer tutorials, documentation, and training courses specifically for pen testing tools. Additionally, online communities of pen testers can provide valuable insights and answer specific questions.
9. Are there any ethical considerations when using pen testing tools?
Ans: Yes. Pen testing tools should only be used for authorized engagements and within the agreed-upon scope. It’s crucial to maintain confidentiality and avoid causing any disruption to the target system.
10. What’s the future of pen testing tools?
Ans: The pen testing landscape is constantly evolving. As cyberattacks become more sophisticated, so too will pen-testing tools. We can expect advancements in automation, cloud-based solutions, and integration with artificial intelligence for even more efficient and effective vulnerability detection.












