When a new year begins, cybersecurity remains as active as ever with more advanced threats continuing to pose a challenge to organizations. Hackers are becoming smarter and more innovative in compromising organisations and defeating security workers.
At the centre of this article is a consideration of the major cyber security threats of 2024 focusing on the risk and repercussions of the threats as well as an analysis of a professional person’s opinion on how to avoid them.
So why late let’s explore the list of Top Cybersecurity Threats of 2024.
List of Top Cybersecurity Threats of 2024

After consulting with our team of 100+ cybersecurity professionals we were able to create the following list of Top Cybersecurity Threats of 2024:
1. Increased Ransomware Attacks
Ransomware is a type of malware that locks the data and asks for a ransom to restore access to it and it has been actively targeting organizations for a long time.
According to researchers in the year 2024, ransomware attacks are likely to spike with the targeted segments of industries like healthcare and finance.
‘Ransomware is a very profitable business for cybercriminals and they are always on the lookout for new ways to get past firewalls.
Thus, the threat can be neutralized only by the regular schedule of data backup and disaster recovery planning together with the increased level of security awareness among the employees, which will help to avoid phishing emails containing links to the download of the ransomware.
Attack Rates:
- In Q1 of 2024, there were 63 confirmed ransomware attacks, affecting 17.1 million records globally.
These attacks broke down as follows:
- 32 attacks on businesses, impacting 17,059,205 records.
- 7 attacks on schools and education, affecting 8,797 records.
- 17 attacks on government agencies, impacting 48,949 records (higher than the 10,592 breached in Q1 2023)
2. Cloud-Based Threats
When more businesses switch to corporate cloud solutions, the exposure increases, and the criminals change tactics and targets. In 2024, cloud security threats like misconfigured cloud services, unauthorized access to the cloud environment, and cloud-native malware are expected to be more common.
According to Cloud security expert Jane Doe, It said that cloud security is a shared model and added that organizations should ensure they are using cloud services that are secure enough for their company and are using some security measures such as access control, encryption, and monitoring to avoid the cloud-based threats.

Top Security Threats in Public Clouds:
Organizations ranked the following as the biggest security threats in public clouds:
- Misconfiguration (68%)
- Unauthorized access (58%)
- Insecure interfaces (52%)
- Hijacking of accounts (50%)2.
Cloud Data Breaches:
- In the past 12 months, 45% of businesses experienced a cloud-based data breach or failed audit, up 5% from the previous year.
- Protecting sensitive data from cybercriminals remains a significant concern
3. IoT and AI-Driven Attacks
IoT gadgets that are installed in almost every home and office, and AI technology that is present in every industry, have new opportunities for hackers. IoT and AI-based cyber-attacks will rise to a new level in 2024 and hackers will utilize AI tools to properly target all the units that can be easily penetrated by their attacks.
’Thus, organizations must be active in protecting IoT devices, making sure they receive patches as they are released and using end-to-end secure communications,
IoT Attacks:
- In 2022, there were over 112 million Internet of Things (IoT) cyber-attacks worldwide. This figure has significantly increased from around 32 million detected cases in 2018. The year-over-year increase in the number of IoT malware incidents was 87%1.
- Specifically, in December 2022, there were 10.54 million IoT attacks globally. Interestingly, the highest number of monthly attacks was detected in June 2022, with approximately 13 million attacks
4. Nation-State Attacks
Cyber spoofing is another threat that we will still experience in the year 2024 where nation-state attacks on the organization wantonly undertake destruction of the organizations’ properties or steal their intellectual property.
Supply chain attacks and social engineering attacks are usually applied and quite hard to mitigate since they are complicated.
To enhance their cybersecurity, organizations have to be ready for nation-state attacks with investment in Threat Intelligence programs, constant look for signs of advanced threats and Incident Response planning.
They should also make sure that the duties have been well segregated and access rights granted to the employees are minimal in cases of a breach to avoid lateral movement.
Nation-State Attacks:
- Nearly 80% of nation-state attacks were directed against government agencies, think tanks, and non-government organizations (NGOs)
- There was a 100% rise in significant nation-state incidents between 2017 and 2021.
5. Insider Threats
Insider threats, those arising from employees or contractors who either purposely or inadvertently act in a manner that compromises security, remain a significant issue in 2024.
End-user threats are a lot more dangerous than external threats because insiders are likely to possess access to the organization’s information technology resources.
Insider threats are a major concern and have a technical and a non-technical side,’ Catching and tracking of insider threats should be assisted by access control, monitoring, tracking and logging Systems.
The organizations should also engage in the development of training programs for the employees because of the security inconvenience and the need to have integrity and confidence retention.
Insider threats:
- US businesses face approximately 2,200 internal security breaches every day 1.
- Globally, 34% of businesses deal with insider threats annually.
- 66% of organizations prioritize insider attacks over external ones.
- Insider incidents have surged by 47% in the last two years
6. Zero-Day Exploits
Malicious code that is unique and not covered in existing signature databases will remain a major threat in 2024 through what is known as zero-day attacks.
Such staking activities entail complex approaches, which include memory corruption and sandbox evasion thereby making the strategies hard to counter.
Organizations need to prioritize vulnerability management, ensuring they’re patching software and systems regularly and investing in advanced security tools to detect and respond to zero-day exploits,” advises Kevin White, cybersecurity consultant at MNO Consulting.
“They should also implement a culture of continuous improvement, staying up-to-date with the latest threat intelligence and security research.”
7. Phishing and Social Engineering
Phishing and social engineering attacks remain high in 2024 in which the attackers employ tricks to make the targets yield to provide sensitive information.
Spear phishing and whaling are typical for these attacks, and it is rather difficult to identify and prevent such incidents.
Employees and providing them with training that can help to avoid phishing and social engineering attacks. ‘They should also also use technical measures for instance email filtering and use of sandbox especially in identification of and blocking of the phishing attacks.’
98% of Cyber Attacks Involve Social Engineering:
- Nearly all cyber attacks (98%) rely on some form of social engineering. This includes tactics like phishing, baiting, and impersonation.
- Social engineering tricks users into revealing sensitive information or taking harmful actions.
Data on Phishing Attacks:
- 84% of Organizations Fell Victim to a Phishing Attack in 2022.
- 36% of All Data Breaches Involve Phishing.
- Phishing remains one of the most popular social engineering techniques.

8. DDoS Attacks
This is because DDoS attacks which are considered to be some of the oldest and most potent forms of attacks where perpetrators seek to overwhelm systems/networks with traffic will remain a threat in 2024.
This can be especially damaging with DDoS attacks being able to harm the availability of specific services and bring a lot of revenue loss.
Traffic filtering and rate limiting are two more recommendations that organizations have to put into practice to protect from DDoS”
Overall Increase:
- Cloudflare observed a 10% decline in application-layer DDoS attacks from Q2 to Q3 of 2022.
- However, there have already been twice as many attacks compared to last year, with a 67% rise in ransom DDoS attacks.
- The pandemic-induced shift to remote work likely contributed to this sustained increase
Attack Types:
- Ransom DDoS attacks surged by 67% year-on-year and 24% quarter-on-quarter.
- Online industries faced a 131% increase in application-layer DDoS attacks quarter-on-quarter.
- Gaming and gambling companies were heavily targeted by network-layer attacks, with a 405% rise in Mirai botnet attacks
9. Cryptjacking and Cryptojacking
Cryptjacking, where attackers secretly use victims’ computing resources to mine cryptocurrency, and cryptojacking, where attackers steal cryptocurrency, will remain significant threats in 2024.
These attacks often involve sophisticated techniques, such as drive-by downloads and lateral movement, making them challenging to detect and mitigate.
Organizations need to implement robust endpoint security controls, including anti-virus software and intrusion detection systems,” They should also be on the lookout for Cryptjacking and crypto-jacking which are crypto-mining malware that causes increased network traffic and system crashes.”
Global Trends:
- Cyberattacks have increased by 600% since the start of the COVID-19 pandemic.
- The annual cost of cybercrime is estimated to reach $6 trillion by the end of 2022, representing 1% of global GDP.
- Cryptojacking attacks rose by 28% globally in Q3 2022 compared to the same period in 2021.
Financial Impact:
- Cybercriminals managed to steal approximately $3.2 billion worth of cryptocurrency in 2021, marking a concerning 516% increase compared to the previous year.
- Monthly cryptocurrency theft by cybercriminals amounts to around $46 million
10. Supply Chain Attacks
Third-party risk management, which involves the action of being vulnerable to supply chain attacks because the opponent targets third-party vendors or suppliers to attain access to the targeted organization, will remain a common threat in the year 2024.
Such style of attacks therefore result in conditions such as spear phishing and malware hence hard to prevent.
The third-party risk should be managed effectively by the organizations which should conduct verification of the fourth parties, for instance, the vendors,”
Supply Chain Attack Statistics:
- In 2023, there were 242 claimed supply chain attacks in the United States, which is the highest reported number since 2017.
- These attacks saw a year-over-year increase of 115 per cent between 2022 and 2023.
- Additionally, approximately 138,000 customers worldwide were affected by supply chain cyberattacks in 2023, a significant decrease from the annual peak of over 263 million impacted customers in 20192.
- Interestingly, supply chain attacks surpassed the number of malware-based attacks by 40 per cent in 2022, impacting more than 10 million people
How to Avoid These Cyber Threats?
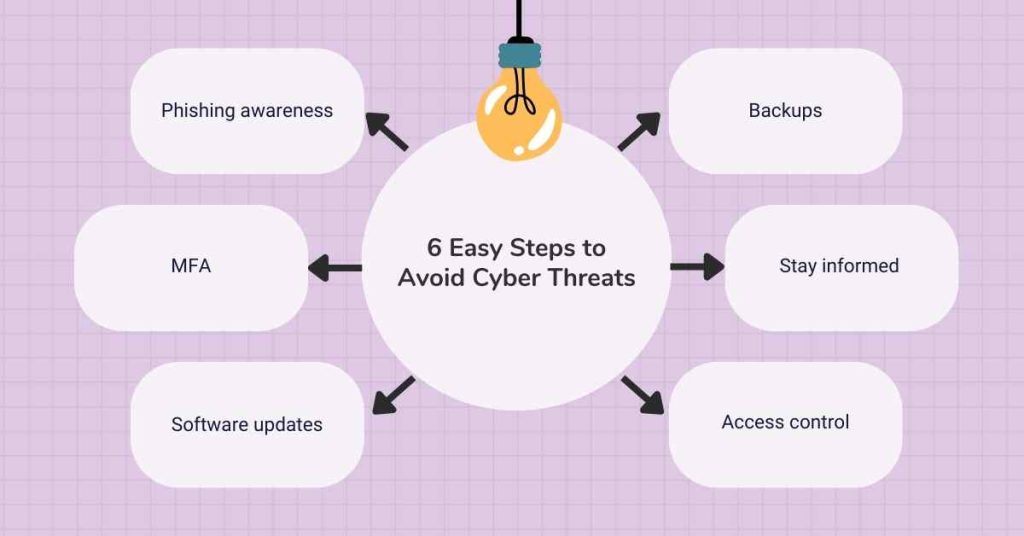
In the above paragraph, we have discussed the list of Top Cybersecurity Threats of 2024, Let’s see how to avoid those threats, with the opinions and suggestions of our cybersecurity professionals we have covered all the possible topics
1. Phishing awareness
Due to its impact, the major threat type is phishing emails. Essentially avoid emails from unknown senders and those with elements of fear, spelling mistakes, or attachments that are not expected.
If there is a link or an attachment in the message never click, and never open unless you can ascertain beyond doubt that it is from a legitimate source.
2. Strong passwords and Multi-Factor Authentication (MFA)
It may be shocking, but the recommendation is to create one powerful password for every account and, if possible, activate the MFA system. MFA enhances the protection in that once your password is entered you will need the code that is sent to your phone or email.
3. Software updates
Update your operating system and applications including firmware which have new patches to these areas.
4. Backups
Always make sure that vital information is backed up daily to another backup system. It enables you to keep the copies that can be used in the event of a cyber attack to regain your lost data.
5. Stay informed
Learn new entrant threats by reading cybersecurity blogs from credible sources.
Employee training: Educate the employees to reduce the risks of cybersecurity threats which involve giving numerous examples of how phishing is carried out and ways in which information can be secured.
6. Access control
Tighten user access to the systems as well as safeguard other forms of data that are considered to be more critical by enforcing strict security measures.
Summary
Here is the summary of the “Top Cybersecurity Threats of 2024” :
- Increased Ransomware Attacks
- Cloud-Based Threats
- IoT and AI-Driven Attacks
- Nation-State Attacks
- Insider Threats
- Zero-Day Exploits
- Phishing and Social Engineering
- DDoS Attacks
- Cryptjacking and Cryptojacking
- Supply Chain Attacks
Conclusion
Therefore, the above-mentioned ten threats are regarded as risks to the organization within the current context of cyber risks. Ransomware, Advanced AI-based threats, and threats targeting the Internet of Things and others can cause critical consequences: loss of data, money, and the reputation of a company.
To avoid such risks, organizations must be vigilant, and therefore implement security procedures and educate people in the organization about cyber crimes. With this knowledge, organizations will be able to avoid Organizational cyber dangers and protect exclusive Information and Systems.
FAQs:
1. What is the most common type of cyber attack?
Ans: The most common type of cyber attack is phishing, which involves tricking individuals into divulging sensitive information or providing access to systems.
2. How can I protect my organization from ransomware attacks?
Ans: To protect your organization from ransomware attacks, implement robust backup systems, keep software up-to-date, and use antivirus software. Also, educate employees on the risks of ransomware and the importance of reporting suspicious activity.
3. What is the difference between a virus and malware?
Ans: A virus is a type of malware that replicates itself by attaching to other programs or files, while malware is a broader term that includes viruses, trojans, spyware, and other types of malicious software.
4. How can I prevent IoT security threats?
Ans: To prevent IoT security threats, implement robust security protocols for IoT devices, including secure communication protocols and regular software updates. Also, conduct regular security audits and penetration testing to identify vulnerabilities.
5. What is the role of AI in cybersecurity?
Ans: AI can be used to detect and respond to cyber threats, including identifying patterns and anomalies, and responding to attacks in real-time. However, AI can also be used by attackers to launch more sophisticated attacks.
6. How often should I update my software and systems?
Ans: It’s recommended to update your software and systems regularly, ideally at least once a month, to ensure you have the latest security patches and features.
7. What is a zero-day exploit?
Ans: A zero-day exploit is a cyber attack that exploits a previously unknown vulnerability in software or hardware. Zero-day exploits can be particularly devastating as there is no patch or fix available to protect against the attack.
8. How can I prevent insider threats?
Ans: To prevent insider threats, implement robust access controls, including multi-factor authentication and least privilege access. Also, conduct regular security audits and monitor employee activity for suspicious behaviour.
9. What is the difference between a firewall and antivirus software?
Ans: A firewall is a network security system that monitors and controls incoming and outgoing network traffic, while antivirus software is designed to detect and remove malware from a computer system.
10. How can I report a cyber attack?
Ans: If you suspect a cyber attack, report it immediately to your organization’s incident response team or law enforcement agency. Also, notify your employees and stakeholders of the attack, and take steps to contain and mitigate the damage.












