In today’s technology-driven world, security is a top priority for businesses and organizations of all sizes. As the number of cyber-attacks continues to rise, ensuring that applications and software are secure and protected from potential threats is becoming increasingly important. One of the most effective ways to achieve this is through Dynamic Application Security Testing (DAST).
In this article, we’ll explore the concept of DAST, its benefits, and how it can be integrated into the software development lifecycle to strengthen application security.
What is Dynamic Application Security Testing (DAST)?
Dynamic Application Security Testing (DAST) is black-box testing that analyzes an application’s security by simulating real-world attacks.
Unlike static application security testing (SAST), which reviews an application’s code for vulnerabilities, DAST tests an application’s behaviour and response to external inputs, such as user inputs, network traffic, and APIs.
DAST involves using automated tools to simulate attacks on an application, identifying weaknesses and vulnerabilities in the process. The goal of DAST is to uncover the “unknown unknowns” – the vulnerabilities that are not visible through other testing methods.
How Does DAST Work?
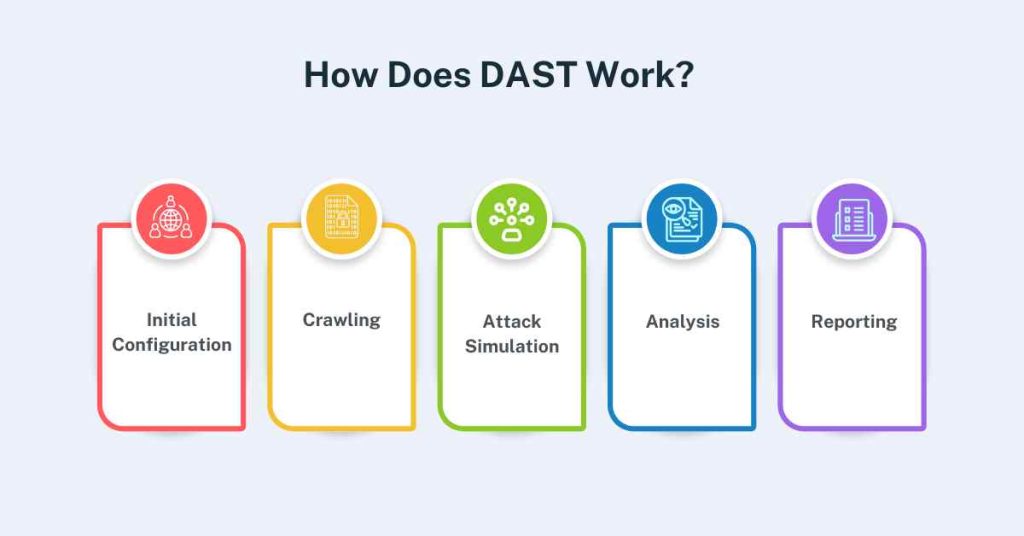
The DAST process typically involves the following steps:
1. Initial Configuration
Configuration is the first phase of the testing process that is conducted to set up the DAST tool and highlight the precise test objectives such as organizational user ID and password to perform an attack and the area that is chosen for the testing process.
2. Crawling
The DAST tool maps the application and lists all the pages, inputs, and APIs that have to be tested.
3. Attack Simulation
The DAST tool works by emulating various attacks against the application and it includes; SQL injection, cross-site scripting attacks also known as XSS, and cross-site request forgery also known as CSRF.
4. Analysis
The DAST tool tests whether an attack poses a risk, which if realized, presents the weakest areas of the application.
5. Reporting
The findings of the test are presented in a report where the detailed findings together with recommendations are presented.
Top 5 Benefits of DAST
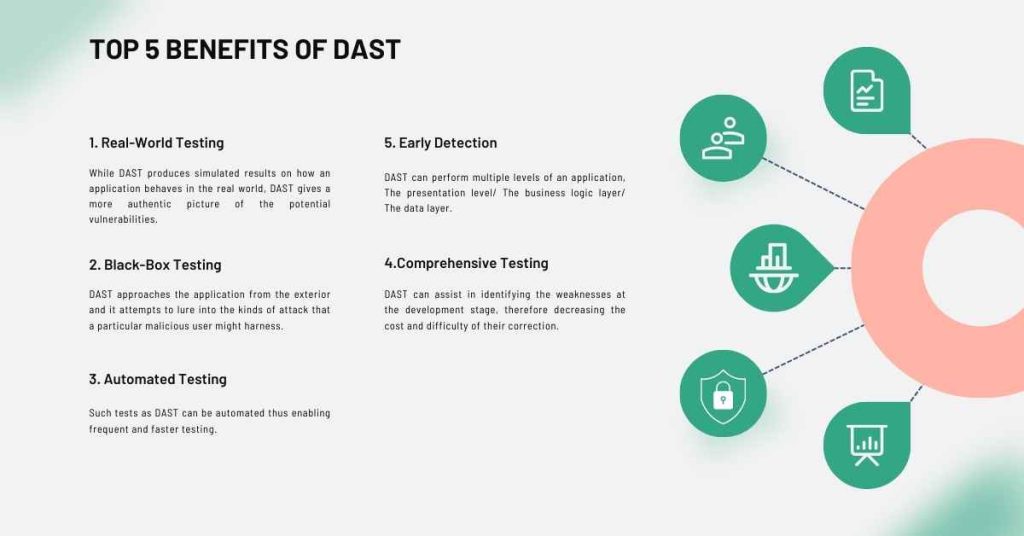
DAST offers several benefits over other testing methods, including:
1. Real-World Testing
While DAST produces simulated results on how an application behaves in the real world, DAST gives a more authentic picture of the potential vulnerabilities.
2. Black-Box Testing
DAST approaches the application from the exterior and it attempts to lure into the kinds of attack that a particular malicious user might harness.
3. Automated Testing
Such tests as DAST can be automated thus enabling frequent and faster testing.
4. Comprehensive Testing
DAST can perform multiple levels of an application, The presentation level/ The business logic layer/ The data layer.
5. Early Detection
DAST can assist in identifying the weaknesses at the development stage, therefore decreasing the cost and difficulty of their correction.
Advantages Over SAST
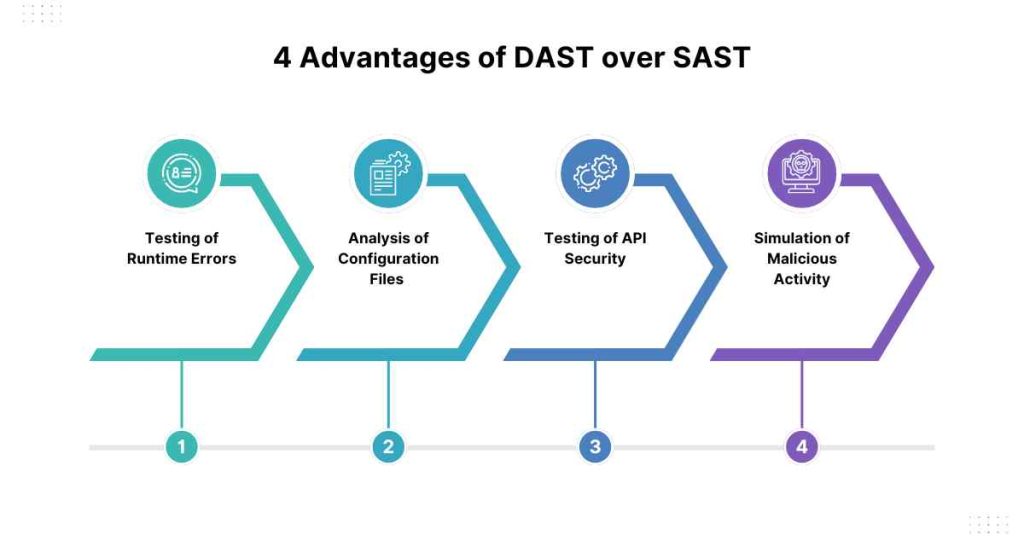
While SAST is an essential part of the application security testing process, it has some limitations. Here are some advantages of DAST over SAST:
1. Testing of Runtime Errors
There is a difference between Dynamic Analysis for SoftwareTesting and SAST because DAST can identify runtime errors that SAST cannot, for example, errors due to an unexpected input from the user.
2. Analysis of Configuration Files
During the Vulnerability Scan, it is possible to analyze such files as config files; on the web. config, for example, to find out if there are any deficiencies.
3. Testing of API Security
Using DAST it is possible to assess the security of APIs such as the authentication and authorization procedures.
4. Simulation of Malicious Activity
DAST is capable of mimicking vandals, for example, SQL injection and cross-site scripting.
Best Practices for Implementing DAST
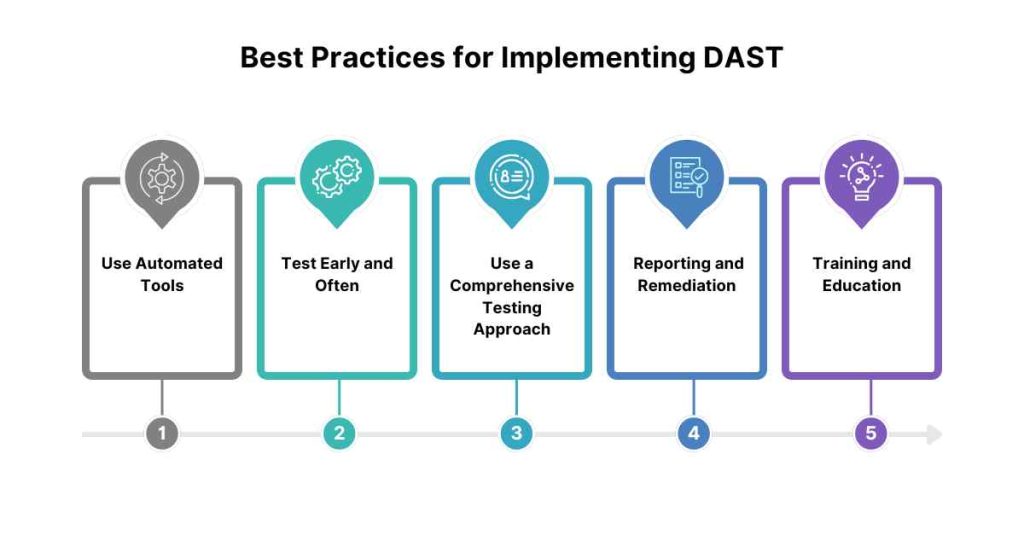
Here are some best practices for implementing DAST:
1. Use Automated Tools
Leverage on automated DAST too to lower the overheads and costs associated with testing.
2. Test Early and Often
Testing should be performed in the early stage possible, or better yet during unit testing, integration testing and system testing.
3. Use a Comprehensive Testing Approach
Implement an integrated model of testing that will include more than one level of testing, for instance, SAST and DAST.
4. Reporting and Remediation
In this context, make sure that the identified vulnerability incidents occur and are addressed effectively and without undue delay.
5. Training and Education
Motivate developers to enhance their code security through educating and training them in issues of code and application security testing.
Conclusion
In conclusion, Dynamic Application Security Testing (DAST) is an essential part of the application security testing process. DAST tests an application’s behaviour in a real-world environment, providing a more accurate picture of potential vulnerabilities.
By integrating DAST into the software development lifecycle, application developers can identify and remediate vulnerabilities early, reducing the cost and complexity of remediation. While DAST has its limitations, it offers several benefits over other testing methods, including real-world testing, black-box testing, and automated testing.
By using DAST in conjunction with other testing methods, such as SAST, application developers can strengthen application security and protect against potential threats.
FAQs: What Is Dynamic Application Security Testing?
1. What are the different types of DAST tools available?
Ans: There are various types of DAST tools available, including open-source tools, commercial tools, and cloud-based tools. Some popular DAST tools include OWASP ZAP, Burp Suite, and Veracode.
2. How is DAST different from Static Application Security Testing (SAST)?
Ans: DAST is a black-box testing method that tests an application’s behaviour in a real-world environment, while SAST is a white-box testing method that reviews an application’s code for vulnerabilities. DAST simulates attacks on an application, while SAST analyzes the application’s code for potential vulnerabilities.
3. Can DAST be used to test for compliance with security regulations?
Ans: Yes, DAST can be used to test for compliance with security regulations, such as PCI-DSS, HIPAA, and GDPR. DAST can help identify vulnerabilities and weaknesses that could lead to non-compliance, ensuring that applications meet regulatory requirements.
4. Can DAST be used in conjunction with other testing methods?
Ans: Yes, DAST can be used in conjunction with other testing methods, such as SAST, penetration testing, and vulnerability scanning. Using multiple testing methods is recommended to ensure comprehensive application security.
5. How often should I use DAST?
Ans: DAST should be used during various stages of the software development lifecycle, including unit testing, integration testing, and system testing. Ideally, DAST should be used early and often to ensure that vulnerabilities are detected and remediated early.
6. What are the challenges of implementing DAST?
Ans: Some of the challenges of implementing DAST include high false positive rates, high cost, skillset requirements, limited visibility, and testing requirements. However, these challenges can be mitigated by using automated tools, implementing a comprehensive testing approach, and providing training and education to developers.
7. Can DAST be used for web applications, mobile applications, and APIs?
Ans: Yes, DAST can be used for web applications, mobile applications, and APIs. In fact, DAST is particularly effective at testing API security, including authentication and authorization mechanisms.
8. How do I choose a DAST tool?
Ans: When choosing a DAST tool, consider factors such as automation capabilities, scalability, ease of use, and compatibility with your application and infrastructure. You should also evaluate the tool’s ability to simulate real-world attacks and identify vulnerabilities.
9. Can DAST be integrated into Continuous Integration/Continuous Deployment (CI/CD) pipelines?
Ans: Yes, DAST can be integrated into CI/CD pipelines to automate testing and ensure that vulnerabilities are detected and remediated early. This can help streamline the testing process and reduce the overhead and cost of testing.
10. Is DAST a replacement for other application security testing methods?
Ans: No, DAST is not a replacement for other application security testing methods. In fact, using multiple testing methods is recommended to ensure comprehensive application security. DAST should be used in conjunction with other testing methods, such as SAST, penetration testing, and vulnerability scanning, to ensure that all potential vulnerabilities are identified and remediated.












