In the field of cybersecurity, many concepts and words can be unfamiliar or even misleading, even for a professional. Two terms are often used interchangeably when they are not; these are Vulnerability Assessment and Penetration Testing.
Even though both are employed in the process of establishing the vulnerabilities within an organization’s security structure, they have different approaches, coverage, and goals.
In this article, we will provide simple explanations for the following: What is the difference between VA and PT in simple words?
But before going into the differences let’s see what is vulnerability assessment and Penetration Testing.
What is a Vulnerability Assessment?
A Vulnerability Assessment is a structured approach to identifying, categorizing and ranking weaknesses in an organization’s information technology systems, networks, and applications.
A Vulnerability Assessment is a process of identifying and ranking weaknesses in an organization’s system that an attacker can use. This process entails the evaluation of an organization’s technological framework to determine the possible avenues of infiltration by malicious activities.
Think of a Vulnerability Assessment as a thorough health check-up for your organization’s security systems. Just as a doctor conducts a series of tests to diagnose health issues, a Vulnerability Assessment is a diagnostic process that helps identify security vulnerabilities that need to be addressed.
A Vulnerability Assessment typically involves:
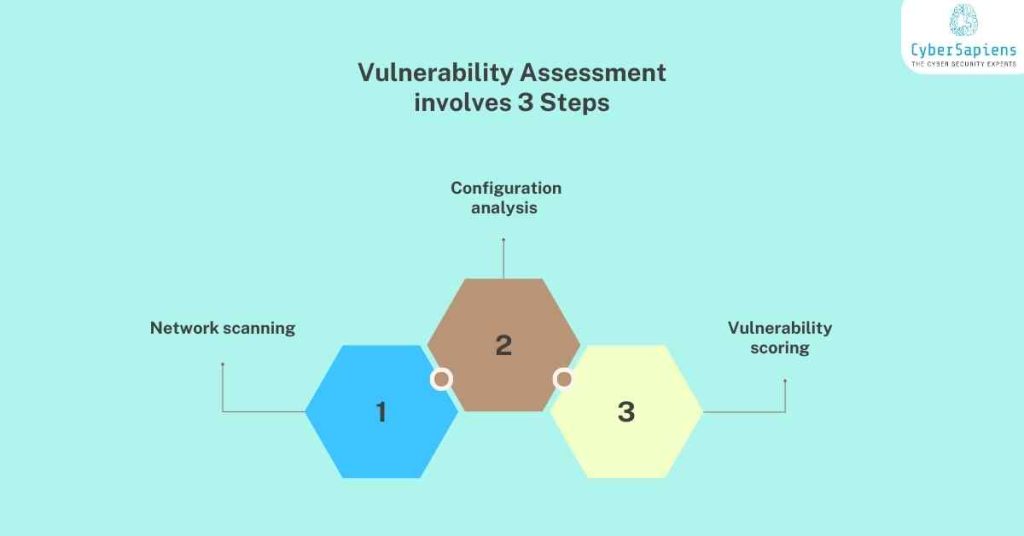
1. Network scanning
Automated tools are used to scan the network for open ports, services, and potential vulnerabilities.
2. Configuration analysis
System configurations, patch levels, and software versions are reviewed to identify potential weaknesses.
3. Vulnerability scoring
Identified vulnerabilities are scored based on their severity, likelihood of exploitation, and potential impact.
What is Penetration Testing?
Penetration testing is also known as Pen Test or Ethical Hacking, which is a method that involves imitating an attack on the organization’s IT systems, networks or applications to ascertain their security weaknesses. The main purpose of Penetration Testing is to challenge an organization’s defences by trying to penetrate its security measures.
Consider Penetration Testing as a form of exercising the weaknesses of your organization’s security systems just as you would in a fire drill. This is to establish areas that can be vulnerable to attacks so that they are corrected before an actual attack happens.
What Does a Penetration Test Typically Involve?
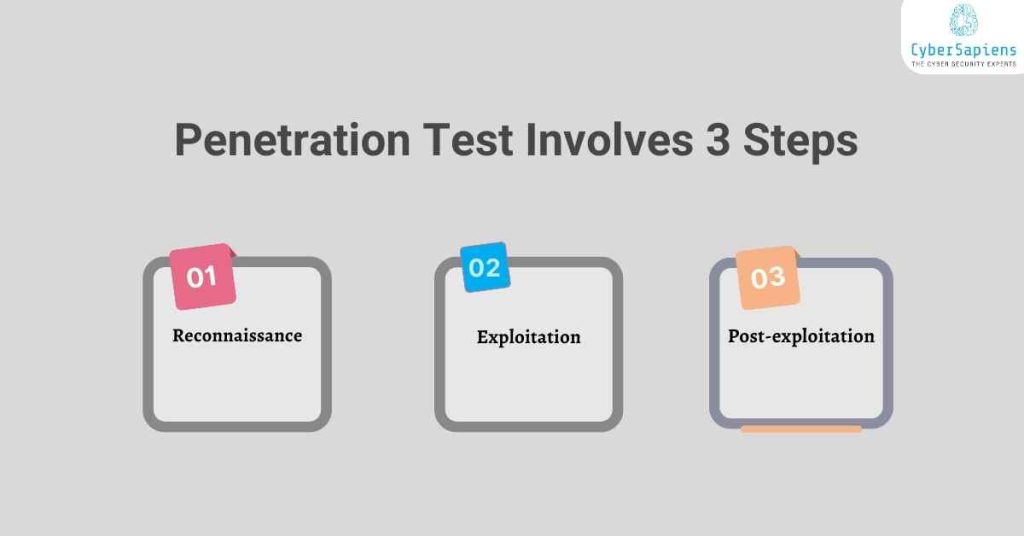
1. Reconnaissance
Gathering information about the target system, network, or application.
2. Exploitation
Attempting to exploit identified vulnerabilities to gain access to the system.
3. Post-exploitation
Analyzing the system, extracting data, and determining the extent of access gained.
Top Key Differences between Vulnerability Assessment and Penetration Testing
Now that we have understood the definitions and processes involved in Vulnerability Assessment and Penetration Testing, let’s highlight the key differences between the two:
Vulnerability Assessment (VA)
1. Focuses on identifying potential weaknesses
VA scans systems and applications for the presence of known vulnerabilities. It is like an examination to determine parts of an organization that can be easily vulnerable to threats.
2. Automated process
VAs frequently use automated tools to perform a quick assessment of a large number of systems.
3. Provides a risk assessment
VA reports sort the results by severity and possible consequences so that you can concentrate on the most severe problems.
4. Less expensive and more frequent
VAs are a good method to receive the common view of your security state at a reasonable price.
Penetration Testing (Pen Testing)
1. Exploits vulnerabilities
Pen testing is not just about finding vulnerabilities. It is the process of imitating attacking to ascertain whether or not the vulnerabilities can be used to penetrate the systems or gain information.
2. Manual process
Pen testers are professionals who are well-trained in the art of penetration testing, this means they can use their minds to look for possible weaknesses.
3. Shows how attackers could compromise your systems
Penetration testing reports do not only include the vulnerabilities but also describe how the attacker can leverage such vulnerabilities to compromise the security of your organization.
4. More expensive and less frequent
Penetration testing is a more detailed and hence, time-consuming process than VA which makes it costlier than VA.
Here is a Table Summarizing the Key Differences
We know what you are thinking—you need a simpler way to understand the differences between Vulnerability Assessment and Penetration Testing, right? We’ve got you! Here is a simple table to make it easier to understand:
| Feature | Vulnerability Assessment | Penetration Testing |
| Approach | Automated scanning | Simulated attacks by ethical hackers |
| Focus | Identifying potential weaknesses | Exploiting vulnerabilities to assess impact |
| Cost | More affordable | More expensive |
| Frequency | Can be done regularly | Done periodically for deeper analysis |
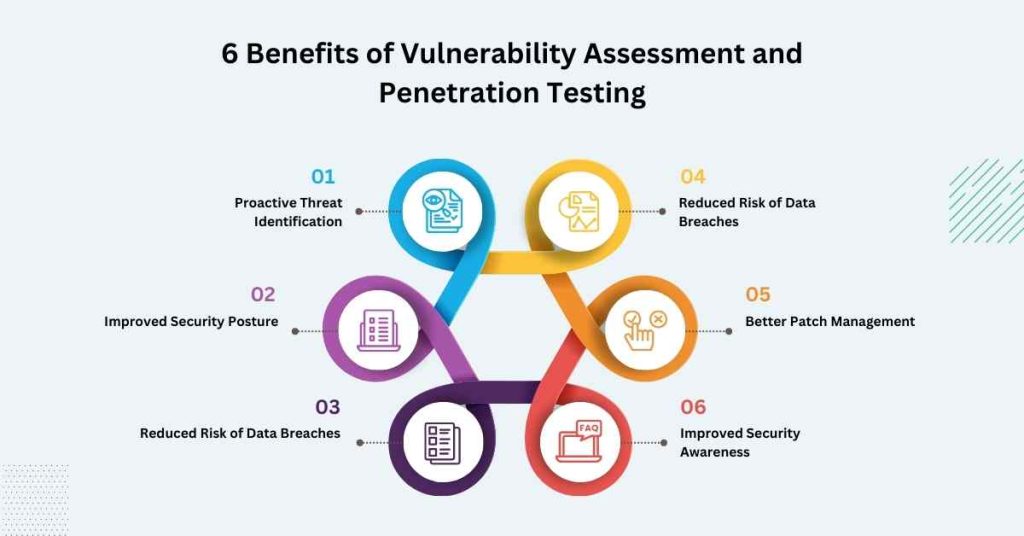
6 Benefits of Vulnerability Assessment and Penetration Testing
In the above, you will see the definition and difference between vulnerability assessment and penetration testing. Now let’s see the benefits of Vulnerability Assessment and Penetration Testing:
1. Proactive Threat Identification
VAPT is an attempt to find out the loopholes in the system and the applications to prevent hackers from exploiting them. This way, organizations can anticipate and fix the holes that could lead to security breaches.
2. Improved Security Posture
Thus, an organization can use a VAPT to get an overall view of its security weaknesses through a vulnerability assessment and a penetration test. This holistic view enables the identification of areas of need and the chalking up of resources to specific areas to address the weaknesses that are currently present in the security architecture.
3. Regulatory Compliance
There are so many industries that have laid down rules that demand frequent testing of security. This is because VAPT assists in adherence to the following regulations thus preventing penalties that may arise from non-adherence.
4. Reduced Risk of Data Breaches
A data breach can be disastrous cause monetary loss and harm the company’s image. VAPT prevents these breaches by pointing out and correcting the system’s holes that the attackers may use.
5. Better Patch Management
It is common to identify certain vulnerabilities that require patches to be applied. This data is useful in determining areas that need attention and management concerning patching, and hence keep the systems up to date with security patches.
6. Improved Security Awareness
So the very process of VAPT can contribute to the increase of the security culture within an organization. This can result in employees being more conscious of the dangers that exist in the cyber world.
Conclusion
In conclusion, vulnerability assessment and penetration testing are crucial for cybersecurity, but they differ in approach, scope, and objectives. Assessments identify potential weaknesses, while testing simulates real-world attacks to test defences. Understanding these differences helps organizations make informed cybersecurity investment decisions, ultimately improving their security posture.
FAQs: What is the difference between VA and PT in simple words?
1. What’s the difference between a vulnerability and a threat?
Ans: Here are the 2 major differences between a vulnerability and a threat:
1. A vulnerability is a weakness in your system that could be exploited by an attacker. It’s like a loose lock on your door.
2. A threat is someone who might try to exploit those weaknesses, like a burglar.
2. Do I need both a vulnerability assessment and a pen test?
Ans: Not necessarily. Vulnerability assessments are a good starting point for regular checkups, while pen tests provide a deeper dive.
3. How often should I do a vulnerability assessment?
Ans: It depends on your needs, but regular scans (e.g., monthly) are a good practice. More frequent scans might be needed if you make frequent system changes.
4. How long does a pen test take?
Ans: Pen tests can range from a few days to several weeks, depending on the scope and complexity of your system.
5. Can’t I just fix the vulnerabilities found in a scan and be secure?
Ans: Fixing vulnerabilities is crucial, but pen tests can find unexpected weaknesses that scans might miss. They also show how attackers might exploit them, helping you prioritize your defences.
6. Is penetration testing disruptive to my systems?
Ans: Ethical hackers take precautions to minimize disruption, but some tests might require taking a system offline for a short period. It’s important to communicate the testing plan beforehand.
7. What happens if a pen tester finds a critical vulnerability?
Ans: A good pen tester will report the vulnerability immediately and work with you to develop a remediation plan. This is why pen tests are done with permission!
8. Can I do my vulnerability assessments or pen tests?
Ans: There are free and paid tools available for vulnerability assessments, but they might require some technical expertise. Penetration testing, on the other hand, should be done by experienced professionals.
9. What qualifications should I look for in a pen tester?
Ans: Look for certifications like Certified Ethical Hacker (CEH) or Offensive Security Certified Professional (OSCP). Experience and a good understanding of your industry are also important factors.
10. Are there any legal implications of penetration testing?
Ans: Absolute penetration testing should only be done with the express written consent of the system owner. This ensures everyone is on the same page and avoids any legal trouble.












