The vast array of potential attacks and the complexity of modern cybersecurity landscapes have made it imperative for organizations to establish robust security measures to protect their digital assets. This is where a Security Operations Center (SOC) comes into play.
A SOC is a centralized unit that brings together various security teams, technologies, and processes to detect, prevent, and respond to security incidents. However, the effectiveness of a SOC is heavily dependent on the use of playbooks.
A SOC playbook, also known as a security operations playbook or a threat response playbook, is a comprehensive, living document that outlines the processes, procedures, and practices to be followed by a SOC in response to various security incidents. But what is the purpose of a SOC playbook, and how does it contribute to the overall success of a SOC? In this article, we will explore the purpose of a SOC playbook and its benefits for organizations.
Purpose of a SOC Playbook
A SOC playbook serves as a guiding document that outlines the roles, responsibilities, and actions required to respond to and contain security incidents. The primary purpose of a SOC playbook is to provide a structured approach to incident response, ensuring consistency, efficiency, and effectiveness in the way security teams handle various types of security incidents.
Here are some of the key purposes of a SOC playbook:
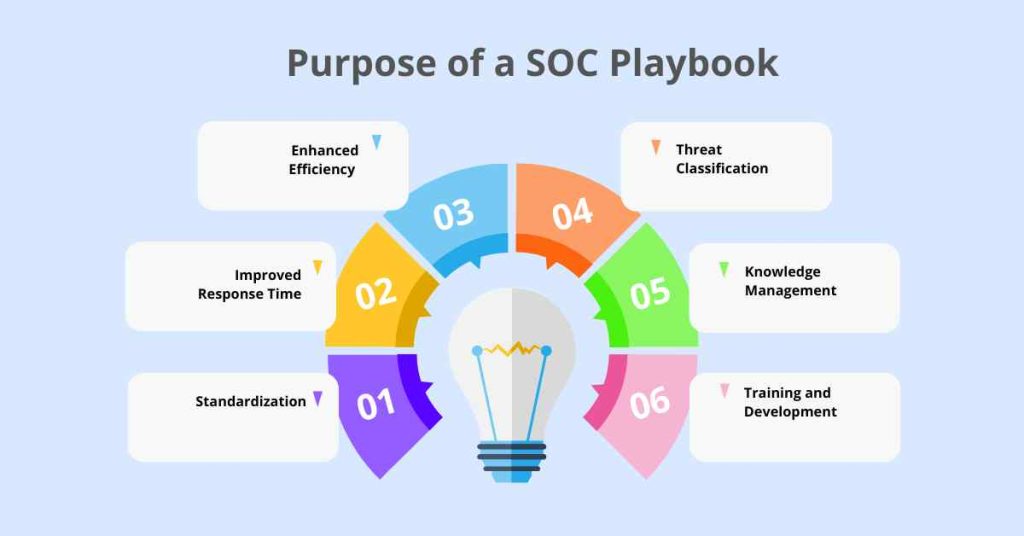
1. Standardization
A SOC playbook standardizes the incident response process across the organization, ensuring that all security teams follow a consistent approach when responding to security incidents. This standardization helps to minimize human error and ensures that the best practices are followed.
2. Improved Response Time
A SOC playbook contains pre-defined procedures and steps to be taken in response to specific types of security incidents. This enables security teams to respond quickly and effectively to security incidents, reducing the mean time to detect (MTTD) and mean time to respond (MTTR).
3. Enhanced Efficiency
By outlining the roles, responsibilities, and actions to be taken by security teams, a SOC playbook helps to streamline the incident response process, reducing confusion, and decreasing the likelihood of mistakes.
4. Threat Classification
A SOC playbook typically includes a threat classification system that allows security teams to categorize and prioritize security incidents based on their severity and impact on the organization.
5. Knowledge Management
A SOC playbook serves as a centralized knowledge repository that captures information about different types of security incidents, the root causes of these incidents, and the most effective methods of mitigating them. This knowledge is then used to refine and update the playbook, ensuring that the playbook stays current and effective.
6. Training and Development
A SOC playbook is an essential tool for training and developing security teams. By documenting processes, procedures, and best practices, a playbook provides security personnel with a comprehensive resource that can help to improve their skills and knowledge.
Benefits of a SOC Playbook
A well-crafted SOC playbook offers numerous benefits for organizations, including:
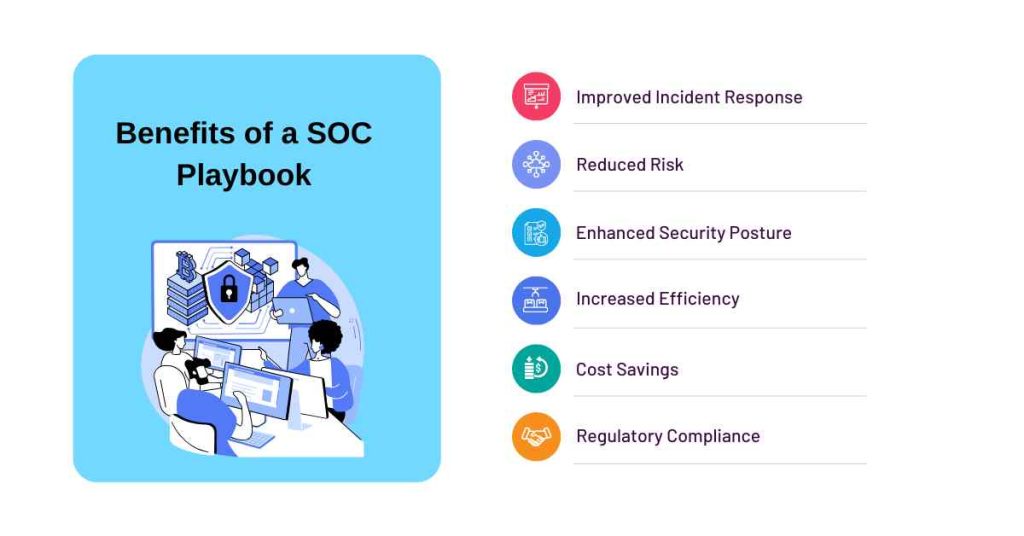
1. Improved Incident Response
By outlining standard procedures and steps to be taken in response to security incidents, a SOC playbook ensures that security teams respond quickly and effectively to security incidents.
2. Reduced Risk
By standardizing incident response processes and procedures, a SOC playbook helps to minimize the risk of human error and reduces the likelihood of mistakes that can exacerbate a security incident.
3. Enhanced Security Posture
A SOC playbook contributes to the overall security posture of an organization by documenting and enforcing best practices and procedures for responding to security incidents.
4. Increased Efficiency
A SOC playbook streamlines the incident response process, reducing the time and effort required to respond to security incidents.
5. Cost Savings
By reducing the time and effort required to respond to security incidents, a SOC playbook can help to minimize the financial impact of a security incident.
6. Regulatory Compliance
A SOC playbook can help organizations demonstrate compliance with various regulations and standards, such as PCI DSS, HIPAA, and GDPR.
Creating a SOC Playbook
Creating a SOC playbook is a challenging task that requires meticulous planning, careful consideration, and input from various stakeholders across the organization. Here are some steps to follow when creating a SOC playbook:
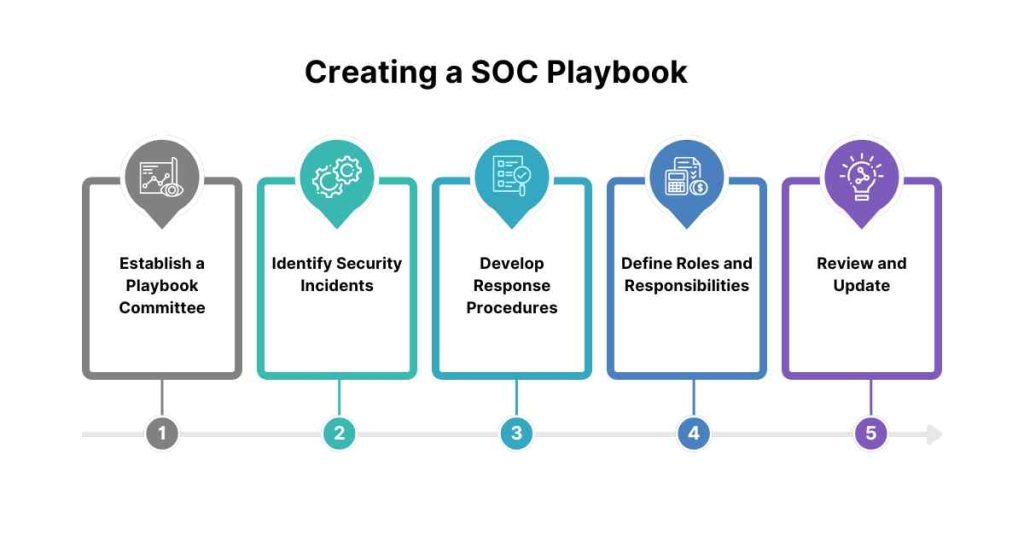
1. Establish a Playbook Committee
Assemble a committee of stakeholders from various security teams, including security analysts, incident responders, and security managers.
2. Identify Security Incidents
Identify the types of security incidents that the playbook should cover, including threat types, risk categories, and attack vectors.
3. Develop Response Procedures
Develop procedures and steps to be taken in response to each type of security incident, including containment, eradication, recovery, and post-incident activities.
4. Define Roles and Responsibilities
Define the roles and responsibilities of each security team and stakeholder involved in incident response.
5. Review and Update
Review and update the playbook regularly to ensure that it remains current and effective.
Best Practices for Implementing a SOC Playbook
Here are some best practices for implementing a SOC playbook:
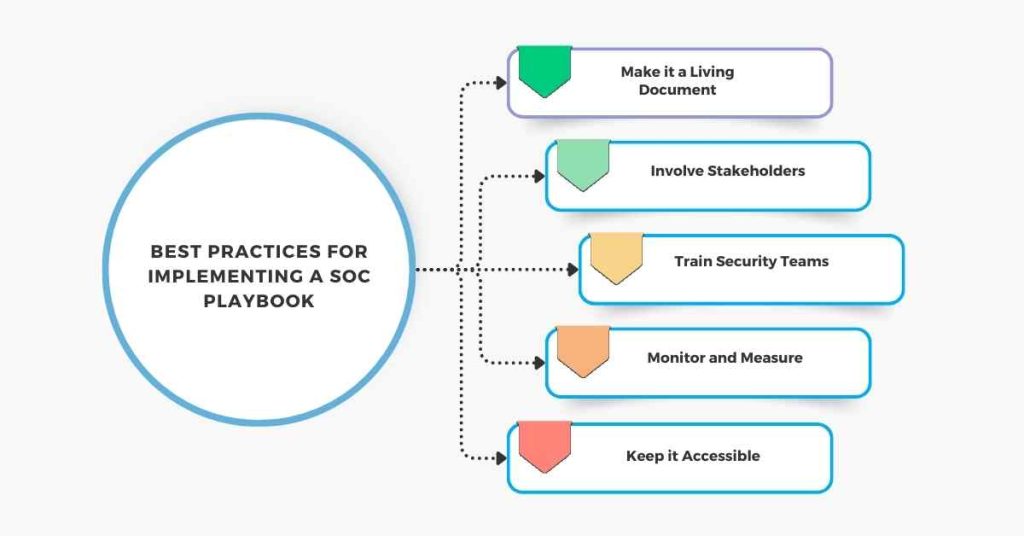
1. Make it a Living Document
The playbook should be a living document that is regularly updated and reviewed to ensure that it stays current and effective.
2. Involve Stakeholders
Involve stakeholders from various security teams in the development and review of the playbook to ensure that it is comprehensive and effective.
3. Train Security Teams
Train security teams on the playbook and its contents to ensure that they understand their roles and responsibilities.
4. Monitor and Measure
Monitor and measure the effectiveness of the playbook and make improvements as needed.
5. Keep it Accessible
Keep the playbook accessible to all security teams and stakeholders, and ensure that it is easy to use and understand.
Conclusion
A SOC playbook is a comprehensive, living document that outlines the processes, procedures, and practices for responding to security incidents. The primary purpose of a SOC playbook is to provide a structured approach to incident response, ensuring consistency, efficiency, and effectiveness in the way security teams handle various types of security incidents.
By standardizing incident response processes and procedures, a SOC playbook can improve incident response times, reduce the risk of human error, and contribute to the overall security posture of an organization. By following best practices for creating and implementing a SOC playbook, organizations can ensure that their security teams are equipped to respond quickly and effectively to security incidents, minimizing the impact on their digital assets.
FAQs: What is the Purpose of a Security Operations Center Playbook?
1. What is a Security Operations Center (SOC) Playbook?
A SOC playbook is a comprehensive, living document that outlines the processes, procedures, Ans: and practices for responding to security incidents. It standardizes incident response processes and procedures, ensuring consistency, efficiency, and effectiveness in the way security teams handle various types of security incidents.
2. Why do I need a SOC Playbook?
Ans: A SOC playbook is essential for organizations that want to establish a robust incident response framework. It helps to improve incident response times, reduce the risk of human error, and contribute to the overall security posture of an organization.
3. What types of security incidents should a SOC Playbook cover?
Ans: A SOC playbook should cover various types of security incidents, including threat types, risk categories, and attack vectors. Examples of security incidents that a playbook should cover include network intrusions, malware outbreaks, data breaches, and Denial of Service (DoS) attacks.
4. Who should be involved in creating a SOC Playbook?
Ans: A SOC playbook should be created by a team of stakeholders from various security teams, including security analysts, incident responders, and security managers. This ensures that the playbook is comprehensive and effective.
5. What is the format of a SOC Playbook?
Ans: A SOC playbook can be in various formats, including Word documents, Excel spreadsheets, or online platforms. The format should be easy to use and understand, and should facilitate collaboration and version control.
6. How often should a SOC Playbook be reviewed and updated?
Ans: A SOC playbook should be reviewed and updated regularly to ensure that it stays current and effective. This can be done monthly, quarterly, or annually, depending on the organization’s needs and requirements.
7. How can I ensure that my SOC Playbook is effective?
Ans: To ensure that your SOC playbook is effective, you should review and update it regularly, involve stakeholders in the development and review process, and train security teams on the playbook and its contents.
8. What are some best practices for implementing a SOC Playbook?
Ans: Some best practices for implementing a SOC playbook include making it a living document, involving stakeholders in the development and review process, training security teams on the playbook, and monitoring and measuring its effectiveness.
9. Can I customize a SOC Playbook to fit my organization’s specific needs?
Ans: Yes, you can customize a SOC playbook to fit your organization’s specific needs. This can include adding or removing procedures, modifying the format, or incorporating organization-specific language and terminology.
10. How can I measure the effectiveness of my SOC Playbook?
Ans: You can measure the effectiveness of your SOC playbook by tracking metrics such as incident response times, mean time to detect (MTTD), and mean time to respond (MTTR). You can also conduct regular reviews and assessments to ensure that the playbook is meeting its intended goals and objectives.












