SOC 2 Compliance in Australia

SOC 2 Compliance in Australia Made Easy & Effortless!
Our team of experts is dedicated to providing comprehensive SOC 2 Compliance solutions tailored to your organization’s unique needs.
We guide you through the entire compliance journey, from assessment to implementation and ongoing maintenance, helping you navigate the complex requirements of SOC 2 compliance with confidence and ease.
Just fill out the form below to get in touch with us!!!
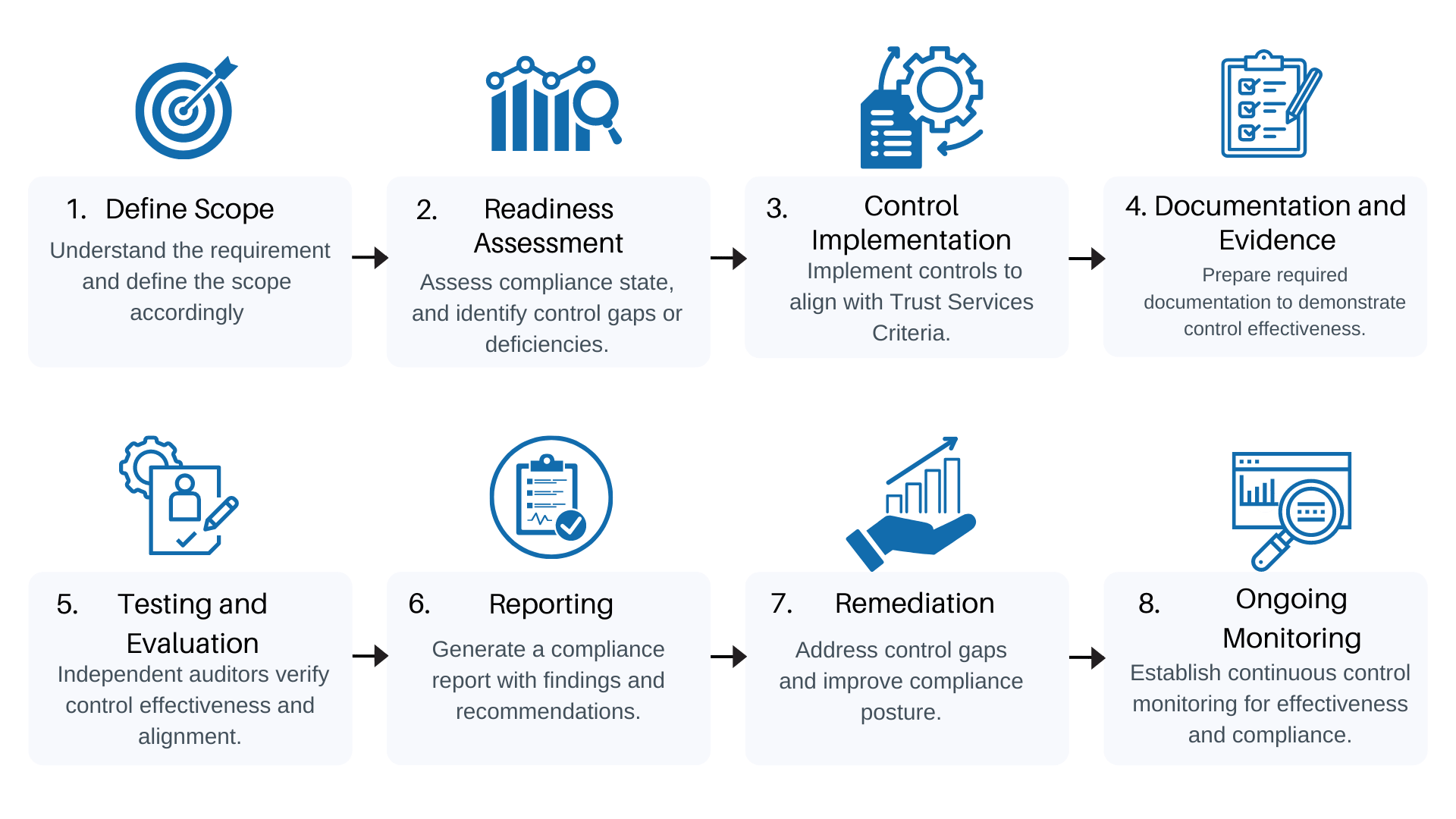
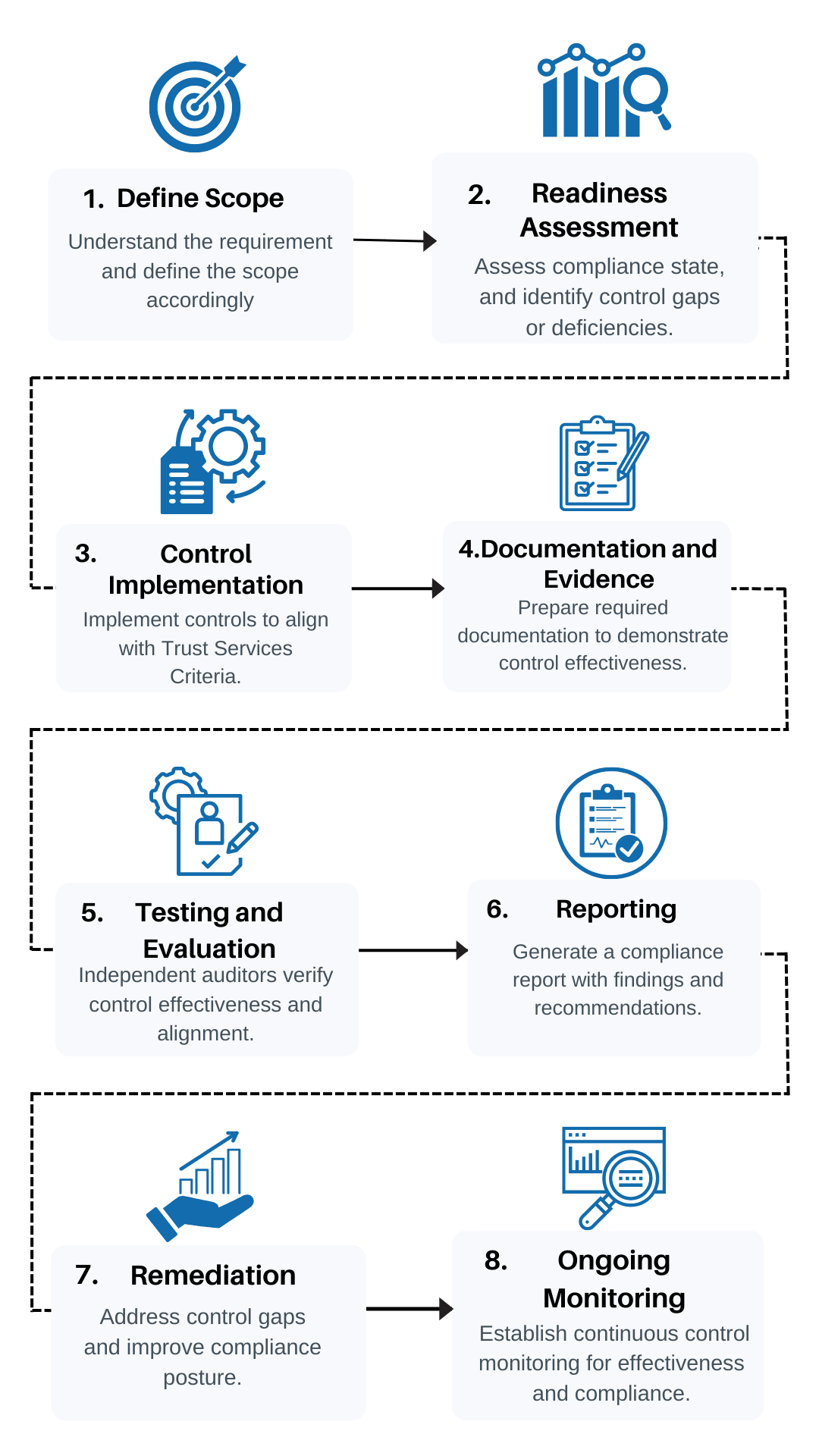
Our SOC 2 Compliance Process
Our Clients






























What is SOC 2 Compliance?
Ensuring SOC 2 compliance is crucial when aiming to establish credibility and foster trust in the contemporary digital landscape.
RephraseThe American Institute of CPAs (AICPA)’s stringent Trust Services Criteria must be met by an organization’s controls. Businesses can prove their dedication to upholding high standards of security, availability, processing integrity, confidentiality, and privacy by adhering to SOC 2 standards. Insights into an organization’s control environment are gained from SOC 2 compliance audits, which reassure clients and stakeholders that their data and systems are secure.
Developing a robust cybersecurity framework is an essential process that helps to mitigate risks and provides a competitive edge in an increasingly security-aware market.
Hence, it is essential to prioritize investing in SOC 2 compliance to safeguard your business and cultivate trust and loyalty among your valued clients.
Why your Organisation needs SOC 2 Compliance?
In the digital age, consideration and credibility must be established through SOC 2 compliance. Customers and other stakeholders are reassured that a business has put strong controls in place to safeguard sensitive data and guarantee the security, accessibility, processing integrity, confidentiality, and privacy of their information.
Companies can demonstrate their commitment to industry-recognized requirements and acceptable practices through the current SOC 2 audit process. SOC 2 compliance allows for risk mitigation, data breach prevention, and meeting the growing demand for data privacy and security. It gives organizations a competitive edge because customers prioritize working with dependable partners who prioritize the security and integrity of their data.

Types of SOC 2 Compliance
There are 2 types of SOC 2 Compliance! We are offering SOC 2 audit services in Australia.
SOC 2 Type 1
The SOC 2 Type 1 report evaluates the effectiveness of a company's controls over a predetermined time frame. It gives a summary of the branding that has been used and evaluates whether it is appropriate for achieving dependable service standards. This report gives stakeholders information about the controls' designs and how they compare to accepted standards, reassuring them that the organization has put in place the proper procedures to manage security and address issues with availability, functional integrity, privacy, and confidentiality.
SOC 2 Type 2
A SOC 2 Type 2 report assesses the design and functionality of an organization's controls over a defined period of time, typically six to twelve months, and the effectiveness of those controls over time. As a result, stakeholders are provided with a comprehensive view of how well the controls have been established and operated over time, as well as how well they have been used. It is important to note that SOC 2 Type 2 provides significant insights into the continued adherence to the Trust Services Criteria, providing a greater level of confidence regarding the effectiveness of security controls.
Benefits of SOC 2 Compliance!
Enhanced Security
Compliance with SOC 2 regulations requires the implementation of strong security controls, ensuring the protection of sensitive data against unauthorized access and breaches.
Regulatory Compliance
SOC 2 compliance adheres to industry-specific regulations, helping your organization meet compliance requirements and avoid fines or legal issues.
Increased Client Trust
SOC 2 compliance demonstrates your commitment to data security and privacy, building trust with customers and stakeholders who value the security of their information.
Competitive Advantage
SOC 2 compliance sets you apart from competitors by demonstrating your commitment to data security and privacy, giving you a competitive edge in the marketplace.
Operational Efficiency
SOC 2 compliance encourages the implementation of standardized processes and systems, leading to improved performance and efficiency.
Risk Mitigation
SOC 2 compliance involves identifying and mitigating risks, allowing you to address vulnerabilities and strengthen your risk management processes.
Vendor Due Diligence
SOC 2 compliance helps facilitate a vendor's due diligence process as potential customers can trust that they have implemented effective controls to protect their data.
Improved Internal Processes
A SOC 2 compliance process often highlights areas of improvement within your organization, allowing you to improve your internal processes and security measures.

Certified Company!

Why Choose Us for your SOC 2 Compliance Audit?
Reach Compliance at your own pace
Establish Roadmap & Stay on Target
Save time & money
Ensure you meet the control requirements
Ensure you pass your certification audit
Ensure you maintain certification every year
Certified Company!


Get In Touch
By filling this form ↓
FAQ's
Yes, CyberSapiens provides expert support for businesses in the Australia seeking SOC 2 compliance.
Our experienced team provides comprehensive SOC 2 audit services, and guides organizations through every step of the compliance journey to ensure successful outcomes.
Yes, SOC 2 compliance is in line with local data security laws in the Australia.
By implementing SOC 2 controls, companies can demonstrate compliance with data privacy laws and protect the personal information of Australian residents.
SOC 2 compliance is a rigorous proof of an organization’s commitment to data security, privacy, and the integrity of its processes and operations SOC 2 compliance is essential for businesses in the Australia to gain trust among customers, assured partners and complied with stringent regulations in the region.
SOC 2 compliance offers a number of benefits to organizations in the Australia.
Builds customer trust, helps build valuable partnerships, sets businesses apart from competitors, and ensures compliance with local data security regulations SOC 2 compliance establishes a strong cybersecurity posture, and strengthens an organization’s reputation in the Australian market.
Failure to comply with SOC 2 in the Australia may result in reputational damage, loss of customer confidence, legal fines and legal liabilities.
Compliance with SOC 2 is essential for those processing sensitive data to mitigate these risks and ensure robust cybersecurity practices.
The time for businesses to comply with SOC 2 in the Australia varies depending on factors such as the size of the organisation, complexity of systems and existing security measures and the average process can take several months.
At CyberSapiens, we work closely with clients to prepare timelines that meet their specific needs and ensure proper compliance.
Yes, CyberSapiens helps businesses in the Australia determine the most appropriate location for SOC 2 compliance audits.
We scrutinize organizational performance, identify appropriate trust management metrics, and scale the analysis to address specific compliance needs.
The need for a SOC 2 Type 1 or Type 2 assessment depends on the objectives of the organization. SOC 2 Type 1 assessments are appropriate if companies want to identify policies and processes in use over a specific period of time.
Whereas SOC 2 Type 2 analyzes are recommended in order to demonstrate the continued efficiency of the controls over the period.
SOC 2 compliance enhances the cyber security posture of businesses in the Australia by implementing robust systems, consistent monitoring and introducing data protection measures.
Implementing SOC 2 requirements enables organizations to proactively address potential security risks, and strengthen their overall cybersecurity capabilities.
SOC 2 compliance enhances the cyber security posture of businesses in the UAE by implementing robust systems, consistent monitoring and introducing data protection measures. Implementing SOC 2 requirements enables organizations to proactively address potential security risks, and strengthen their overall cybersecurity capabilities.
Employee training is critical to ensure compliance and maintenance of SOC 2 in the Australia.
Well-trained employees are better equipped to understand and implement security controls, maintain data confidentiality, and investigate and report potential security issues.
CyberSapiens provides a customized training program that ensures employees are aware effective compliance requirements for.
Businesses in the Australia typically conduct SOC 2 Type 2 inspections annually.
This period allows for a comprehensive review of resources at a critical point in time and provides stakeholders with confidence in the organization’s ongoing compliance efforts.
Organizations in the Australia may face challenges such as scaling up compliance research, identifying and addressing jurisdictional gaps, and managing costs associated with achieving compliance.
We understand such challenges under this and provides expert guidance and support for compliance, and ensures a successful compliance journey..
SOC 2 compliance builds trust with customers and partners in the Australia, and provides independent assurance regarding the organization’s commitment to data security and privacy.
By demonstrating compliance with stringent cybersecurity standards, companies can reassure customers that their data is protected, resulting in stronger partnerships and increased customer loyalty.
Yes, CyberSapiens can help businesses in the Australia address control gaps identified in SOC 2 assessments.
Our experts conduct comprehensive gap analysis and provide guidance to implement critical controls and disciplines, ensuring organizational compliance and maintenance.
Absolutely! CyberSapiens provides expertise in the development and implementation of security programs tailored to the unique Australia legal environment.
Our team ensures systems comply with SOC 2 requirements and local data security regulations, promoting a secure and compliant business environment.
Yes, SOC 2 compliance is crucial for cloud service providers and technology companies in the Australia.
As these organizations handle sensitive customer information.
SOC 2 compliance gives them a competitive advantage, giving customers confidence in their data security practices
In order to maintain SOC 2 compliance, organizations in the Australia should conduct regular internal process reviews, continuously monitor and evaluate the control systems, and update them when regulatory requirements change.
Employee training, incident management and regular audits are also important best practices for maintaining compliance.
Our extensive experience and expertise in cybersecurity and compliance makes CyberSapiens a reliable partner for SOC 2 compliance services in the Australia.
Our tailored solutions, client-centric approach, and proven track record of successful compliance assessments make us the ideal choice for businesses seeking SOC 2 compliance in the Australia.






