In recent years the United Arab Emirates has gone through economic development and has embraced technological advancements including the internet and digital growth which the criminals view as a good ground to attack.
The experience of today’s technology reveals that threats of cyber incidents are on the rise threatening businesses and individuals with associated monetary loss, tarnished image and leak of sensitive data.
In this article, a closer look will be taken at the 15 most frequent types of cyber attacks that target UAE businesses and the specific TTPs that cyber criminals utilize in the context of these organizations.
List of Top 15 Most Common Cyber Attacks on UAE Businesses

Here is the List of Top 15 Most Common Cyber Attacks on UAE Businesses:
1. Phishing Attacks
Phishing attacks are the most reported cyber attacks in the UAE emerging as the largest type of cyber attack in the country accounting for more than 40% of all cyber attacks.
Through impressive impersonations, cyber criminals target persons in organizational systems and organizations through fake emails, messages or text messages in an effort to get the receiver to give out legitimate information like login credentials or other financial details.
2. Ransomware Attacks
Over the recent past, ransomware threats have been on the rise in the UAE as hackers employ the use of malware to lock the users’ data and then seek to be paid ransomware to unlock the same.
A widely known example of a threat that targets databases is ransomware which interrupts business processes and leads to severe economic consequences.
3. SQL Injection Attacks
SQL injection is one of the classes of web application security risks where hackers insert malicious code into a given website’s database to get privileged data or manipulate it, usually without express permission from the owner of the website in question.
This type of attack was noticed to be prevalent in the UAE, particularly among companies that use web applications in business transactions.
4. Cross-Site Scripting (XSS) Attacks
XSS has its roots in the unauthorized introduction of scripts into a web page, as a result allowing the hacker to steal user information and take control of their sessions. In the UAE, XSS attacks are normally aimed at gaining login credentials or the introduction of malicious code on sites.
5. Denial of Service (DoS) Attacks.
Such attacks have the victim’s website or network flooded with traffic making it impossible for any users to access it. DoS attacks are commonly being used in UAE either for blackmailing money or to stop business entirely.
6. Insider Threats
An insider threat occurs when an employee or a contractor who has legitimate access to an organization’s system, data or facilities, has ergo abused this access to become a threat. As for the UAE insider threats, they are mainly driven by greed for monetary benefits and anger as a result of prior dismissal.
7. Social Engineering Attacks
Social engineering as a type of attacks involves tricking employees into disclosing information or doing something contrary to the security policy. In UAE, attacks under social engineering are mainly pretexting, baiting, and quid pro quo attack types.
8. Malware Attacks
A malware attack can be defined as an act of using virus-like programs to corrupt a computer system or respond to vital data. In UAE, virus attacks usually come in the form of an e-mail attachment, contaminated program download, or contaminated website.
9. Man-in-the-Middle (MitM) Attacks
Man-in-the-middle attacks work based on the transparency of the connection between two concerned entities, through which an attacker gets an opportunity to gain access to information being transferred or even become a part of the conversation and introduce a virus. However, in the UAE, these MitM attacks are personalised to capture other important details; this could be login information or even financial details.
10. Distributed Denial of Service (DDoS) Attacks
DDoS attacks are – when hackers flood a website or a network with traffic from different sources which makes the website or the network unavailable to users. In the UAE, DDoS attacks are usually conducted for the purpose of receiving ransom money from the targeted company or for the destruction of its business.
11. Password Cracking Attacks
Password cracking attacks basically refer to an unauthorized attempt to guess or to ‘crack’ passwords for the purpose of gaining access to certain systems or data. In the UAE, password cracking attacks are most times used to attack vulnerable password types, or those that have not been updated often.
12. Spear Phishing Attacks
Spear phishing is a more specific form of phishing and it directly addresses various people with specific e-mails or messages, sometimes using social engineering techniques. In UAE, these attacks are targeted at senior personnel in an organization or anyone with a high level of access to an organization’s information.
13. Drive-by Downloads
The drive-by-download method of penetrating a website actually implies that malware is placed on a website and is downloaded to an individual’s device without his or her consent. In the case of the UAE, drive-by downloads are mainly utilized for the spread of malware or ransomware.
14. Watering Hole Attacks
One of the popular attacks is watering hole attacks that target websites that employees in a given sector or industry are likely to visit, thus incapacitating many employees in one go. In watering hole attack scenarios in UAE, they specifically select certain industries like the finance sector or the healthcare sector among others.
15. Business Email Compromise (BEC) Scams
The BEC scams compel employees to pay large sums of money to fraudsters through social engineering techniques. In the UAE, BEC scams are mostly applied to companies that engage in international money transfers more often.
Number of Cyberattacks Done in UAE
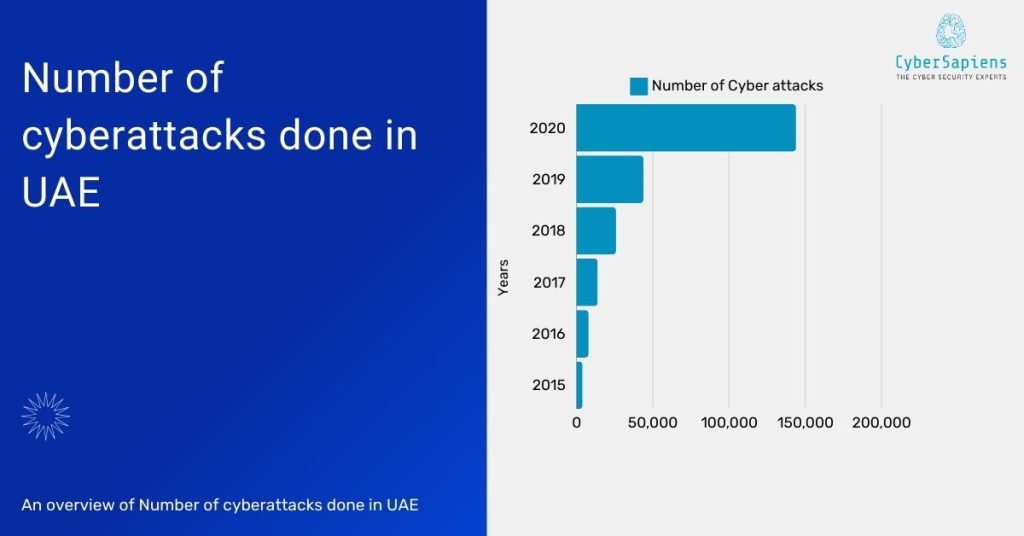
Excited to know the number of cyberattacks that have been done in UAE so why late look into the below data, we have covered the data year-wise.
In the year of 2020:
- Total number of cyberattacks: 144,000
- Average number of cyberattacks per day: 1,115
- Increase in cyberattacks compared to 2019: 250%
- Total estimated cost of cyberattacks: AED 3.4 billion (approximately USD 927 million) (IDC)
- Number of ransomware attacks: 64% of businesses
In the year of 2019:
- Total number of cyberattacks: 44,000
- The average number of cyberattacks per day: 120
In the year of 2018:
- Total number of cyberattacks: 26,000
- The average number of cyberattacks per day: 71
In the year of 2017:
- Total number of cyberattacks: 14,000
- The average number of cyberattacks per day: 38
In the year of 2016:
- Total number of cyberattacks: 8,000
- Average number of cyberattacks per day: 22
In the year of 2015:
- Total number of cyberattacks: 4,000
- The average number of cyberattacks per day: 11
How to Secure your data from these cyberattacks?
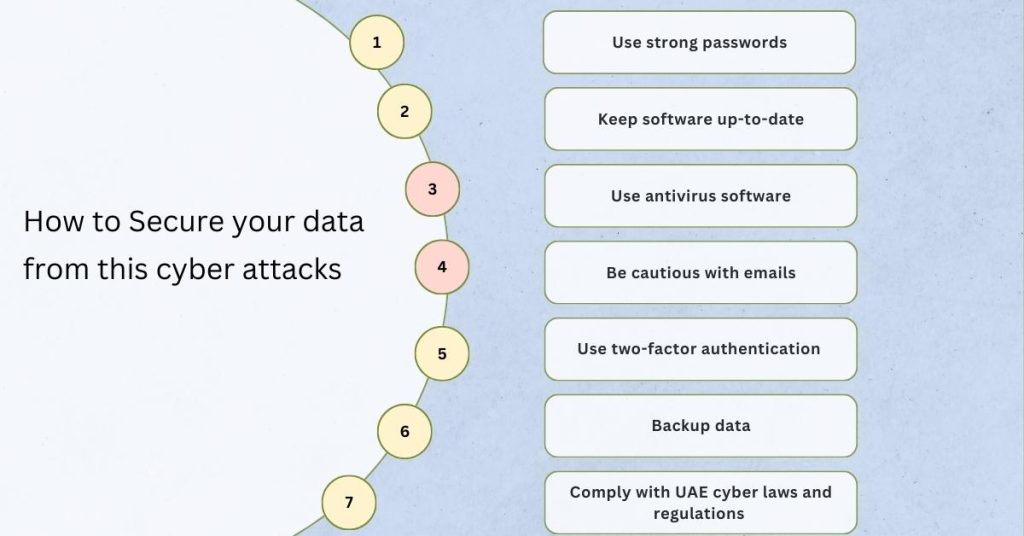
As you have seen in the above paragraph cyberattacks are continuously occurring in UAE, so now you are deciding to protect your data and thinking about how to do it, no worries we have bought you the best tips to secure your data from Cyberattacks just follow the below steps
1. Use strong passwords
Include both, upper case and lower case letters, numbers and various symbols and signs.
2. Keep software up-to-date
It is recommended that you keep your operating system, browser and the various plugins you use up to date as this reduces vulnerability to various threats.
3. Use antivirus software
Subscribe and update your computer with anti-virus software to prevent Russian hackers’ malware.
4. Be cautious with emails
Do not click on or click through on the links or files that are received from unknown senders.
5. Use two-factor authentication
Consequently, enable 2FA every time you get a chance to do it to increase security measures.
6. Backup data
Never keep your important files and data only on the computer, always copy them to another storage media, CD or DVD, or an external hard drive or if possible, keep them in a cloud or on a secure online server.
7. Comply with UAE cyber laws and regulations
Make sure that you meet the requirements of UAE cyber laws and cyber regulations policies like the UAE Cybercrime Law and or the National Electronic Security Authority NESA.
Summary
Here is the summary of the blog titled “Top 15 Most Common Cyber Attacks on UAE Businesses“
- Phishing Attacks
- Ransomware Attacks
- SQL Injection Attacks
- Cross-Site Scripting (XSS) Attacks
- Denial of Service (DoS) Attacks.
- Insider Threats
- Social Engineering Attacks
- Malware Attacks
- Man-in-the-Middle (MitM) Attacks
- Distributed Denial of Service (DDoS) Attacks
- Password Cracking Attacks
- Spear Phishing Attacks
- Drive-by Downloads
- Watering Hole Attacks
- Business Email Compromise (BEC) Scams
Conclusion
Cybercrimes are making rounds in UAE for succeeding in defrauding various companies, tarnishing their reputation and stealing sensitive information.
Due to these threats, it is necessary for organizations to pay maximum consideration to cyber security which consists of awareness among employees, upgrading of software, and installation of spam detection systems.
Due to the completion of the following research, the fifteen frequent cyber attacks observable in UAE are revealed; Accordingly, organizations are in a position to defend themselves in order to safeguard their valuable information.
FAQs
1. What are the most common cyber attacks in the UAE?
Ans: Phishing, malware attacks, social engineering, and denial-of-service attacks are some of the most prevalent threats targeting UAE businesses.
2. How can employees be tricked by phishing attacks?
Ans: Phishing emails often appear legitimate, impersonating trusted sources like banks or colleagues. They trick employees into clicking malicious links or downloading infected attachments.
3. What damage can malware cause to a business?
Ans: Malware can steal sensitive data, disrupt operations, encrypt files for ransom, and damage a company’s reputation.
4. How can social engineering attacks be prevented?
Ans: Employee awareness training on identifying suspicious communication and verifying sender identity is crucial. Additionally, strong access control policies and a culture of cybersecurity awareness are essential.
5. What happens during a denial-of-service attack?
Ans: DoS attacks flood a website or server with excessive traffic, making it unavailable to legitimate users and causing business disruptions.
6. How can businesses protect themselves from Man-in-the-Middle attacks?
Ans: Using a VPN on public Wi-Fi and implementing encryption protocols like SSL/TLS secures online communication and prevents data interception.
7. What are zero-day attacks, and why are they dangerous?
Ans: Zero-day attacks exploit unknown software vulnerabilities, making them highly successful until a patch is developed.
8. How do watering hole attacks target specific businesses?
Ans: Attackers compromise websites frequented by employees of a targeted industry. When employees visit these sites, malware is downloaded to their devices.
9. What is the risk of SQL injection attacks?
Ans: These attacks inject malicious code into user inputs, allowing unauthorized access to sensitive data stored within databases.
10. How can businesses protect against password-spraying attacks?
Ans: Enforcing strong password policies with minimum length, complexity requirements, and regular changes, coupled with multi-factor authentication, significantly reduces the risk.












