Phishing attacks have grown increasingly common in today’s digital world, where technology plays a major part in our personal and professional lives. Phishing attacks are malicious attempts by cybercriminals to gain sensitive information such as passwords, credit card information, or personal information.
In this blog, we’ll study the world of phishing attacks, look at some of their different types, and provide helpful tips on how individuals and companies can protect themselves from this common online threat.
Table of Contents
What are Phishing Attacks?

Phishing attacks are commonly carried out using email, instant messaging, social media, and fake websites.
Attackers imitate trustworthy organizations or individuals, taking advantage of human psychology to trick victims into revealing personal information. Phishing attacks often rely on urgency, fear, curiosity, or a sense of authority to trick unknown victims.
Types of Phishing Attacks
Phishing attacks can take on different forms, including:
1. Email phishing
This is the most common form of phishing, in which hackers send false emails that seem to be from legitimate businesses in an attempt to get victims to click on harmful links or disclose personal information.
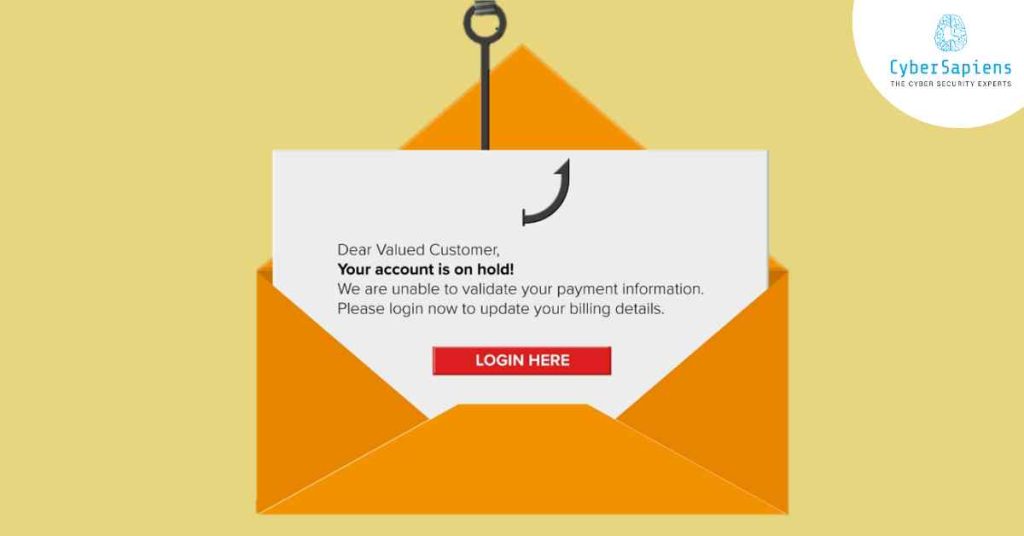
2. Spear Phishing
To make the emails seem more authentic, spear phishing attacks often target specific individuals or organizations and use personal information to do so. To create personalized and convincing emails, the attackers do a lot of research.
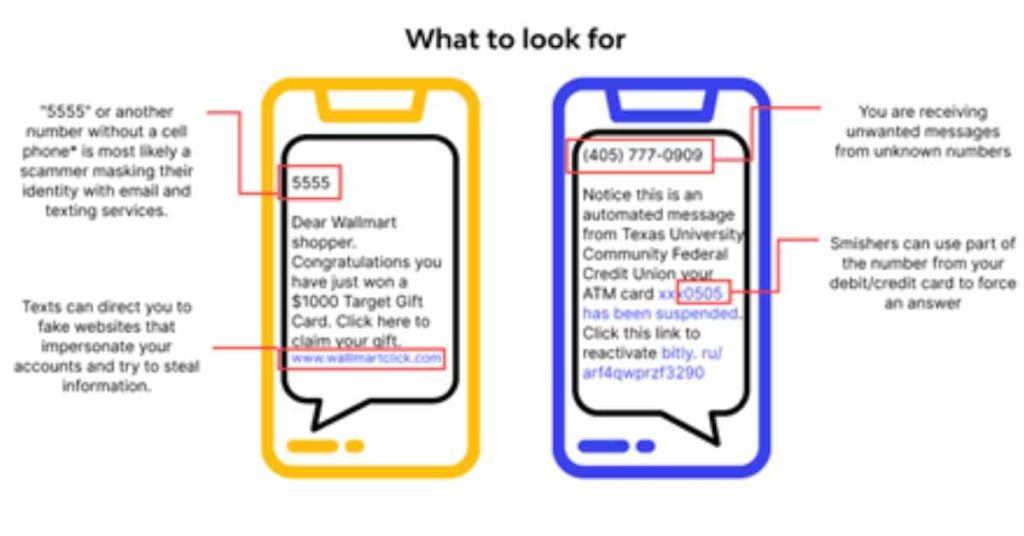
3. Smishing
Phishing attacks are performed through SMS or text messages. Attackers often use fake identities of banks or service providers to send misleading SMS that include dangerous links or prompt victims to contact a scam number.
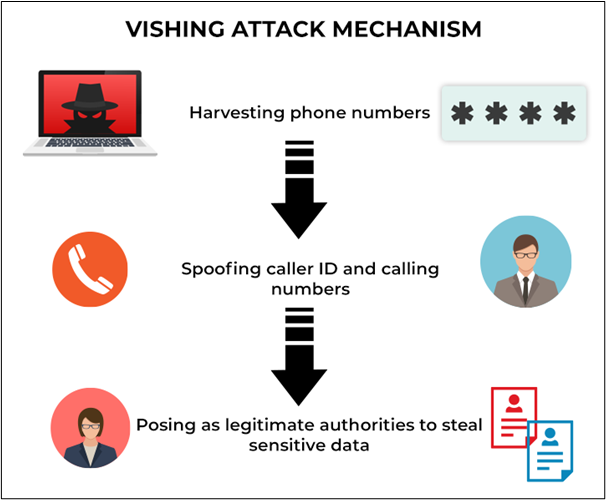
4. Vishing
It refers to phone-based phishing attacks. Attackers act as reputable companies to trick victims into revealing personal information or engaging in fraudulent transactions.
Preventing and Safeguarding Against Phishing Attacks
Protecting yourself and your organization from phishing attacks requires a proactive approach. Here are some essential preventive measures to consider:
1. Increase Security Awareness:
Educate yourself and your employees about phishing attack strategies, warning signals, and common cybercriminal methods. To keep everyone informed, conduct training sessions and update often.
2. Be Alert:
Exercise caution when encountering unsolicited emails, messages, or phone calls. Pay attention to grammatical errors, misspellings, or suspicious requests. Verify the authenticity of any communication through separate channels.
3. Verify URLs:
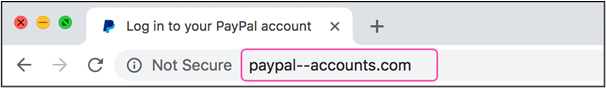
Hover your mouse over links in emails or texts to examine their URLs before clicking on them. Watch out for URLs that look strange, include typos, or redirect to unknown websites. If in doubt, enter the website’s address into your browser and go there immediately.
4. Strengthen Passwords:

For all online accounts, use strong, unique passwords and use multi-factor authentication (MFA) wherever available. Passwords should not contain easily guessable information such as birthdays or names.
5. Install Security Software:
Install robust antivirus, anti-malware, and anti-phishing software on all devices. Keep these software packages up to date to defend yourself from the most recent attacks.
6. Keep Systems and Software Up to Date:
Keep operating systems, web browsers, and software programs up to date. Security patches can be found in software updates to fix vulnerabilities exploited by cybercriminals.
7. Be Wary of Personal Information Requests:
Legitimate organizations typically do not request sensitive information via email or text messages. Engaging in unwanted demands for personal information, financial information, or passwords should be avoided.
8. Report Suspicious Activity:
If you come across a phishing attack, immediately notify your organization’s IT or security team. Reporting incidents assists in preventing others from being victims of the same attack.
Conclusion: Types of Phishing Attacks
Phishing attacks represent a danger to individuals and organizations, exposing sensitive information, financial security, and reputation at risk. We hope that after reading our blog titled “Types of Phishing Attacks & How to Prevent Against Them”.
You got some insights on what the different types of phishing attacks are there and how you can protect yourself and your organization against them.
FAQs
What are the most common types of phishing attacks?
The most common types of phishing attacks include spear phishing, in which attackers target specific individuals or organisations, and pharming, in which attackers lead users to fake websites. Additional types include whaling (targeting high-profile individuals), vishing (phishing via voice calls), and smishing (phishing via SMS). Being aware of these attack types can help you spot potential risks.
How can I recognize a phishing email or message?
Always check for red flags such as dubious senders, grammatical problems, urgent or worrisome wording, and requests for personal information when identifying a phishing email or message. Be wary of emails that request sensitive information or link you to strange websites. Before taking any action, make sure to confirm the sender’s identity and double-check the email’s veracity.
What should I do if I receive a suspicious email or message?
If you receive a strange email or message, do not open any links or download any attachments. Instead, report the email to your email provider as phishing and delete it. If the mail purports to be from a legitimate organisation, authenticate its validity using their established support methods. Taking these actions helps to keep you safe from phishing schemes.
How can I protect myself and my sensitive information from phishing attacks?
Implement many precautionary measures to defend yourself against phishing assaults. These include updating your software and operating systems on a regular basis, using strong and unique passwords, activating two-factor authentication, exercising caution when sharing personal information online, and running dependable antivirus software. By implementing these practices, you can strengthen your security and lower your vulnerability to phishing assaults.
Are there any warning signs that indicate a website may be a phishing page?
Yes, there are signs that a website may be a phishing page. Check for Misspelt URLs, unusual domain names, the absence of SSL encryption (HTTPS), bad website design or graphics, and requests for personal information on insecure pages are some of the warning signals. Paying attention to these indicators will assist you in avoiding interactions with phishing websites.
Can phishing attacks target mobile devices or social media platforms?
Yes, phishing attacks can target social media sites and mobile devices. Mobile phishing, often known as “smishing,” uses malicious apps or phoney SMS messages. Social media networks may also be misused by sending phoney messages, phoney profiles, or links to phishing websites. When using social media and mobile devices, be on the lookout for shady messages or links.
What role does employee training play in preventing phishing attacks?
Employee training is essential for phishing attacks to be avoided. Organisations can inform employees about the dangers of phishing and teach them how to spot and handle such attacks by offering thorough cybersecurity awareness training. Employee empowerment through training makes them the organization’s first line of defence and promotes a security-conscious culture.
Are there any technological solutions or tools available to prevent phishing attacks?
To stop phishing attacks, there are technological solutions and techniques available. Email filters that prevent suspicious emails, anti-malware programs that identify and eliminate phishing threats, browser add-ons that alert users to shady websites, and safe browsing tools that assist in spotting phishing efforts are some examples of these. Implement
About the Author!













